Key Cloak
ServiceOps offers support for SAML 2.0, which facilitates integration for Single Sign-On. ServiceOps acts as the Service Provider (SP) and it integrates with Identity Providers (IdP) using SAML 2.0. The integration basically involves supplying details about SP to IdP and vice-versa. Once you integrate ServiceOps with an IdP, the users simply have to sign-in to IdP and then, they can automatically sign-in to ServiceOps from the respective identity provider’s GUI without having to provide credentials again. ServiceOps supports integration with Key Cloak.
To configure SSO with the Keycloak service, follow the below steps:
Step 1: Sign-in to the ServiceOps portal as a Technician.
Step 2: Navigate to Settings > Admin > Organization > System Preference > Application Settings tab. Verify that the Base URL is the same as the portal URL. If it has the default IP Address, update it.
Step 3: Navigate to Settings > Admin > Users > SSO Configuration > Identity Providers and click Add Identity Provider. The following popup appears.

Step 4: Provide the following details. In this, you need to configure the IDP details of Key Cloak in the ServiceOps while the SP details in the Key Cloak.
| Parameter | Description |
|---|---|
| Name | Enter the name of the identity provider. |
| Identity Provider | To set the Key Cloak login button, select the Identity Provider as Other. If Other is selected, you can set the IDP Logo and IDP Login Button Text. Once configured, the respective login button will appear on the Login page. |
| Auto Create User | Enable if the user is to be created automatically, if not available in the system. By default, disabled. |
| IDP Entity ID | Enter the Entity ID of the IDP from the Okta portal. It is a mandatory field. You can get these details from the Metadata file of Key Cloak |
| IDP Login URL | Enter the login URL of the IDP on which the user will get redirected. It is a mandatory field. You can get this from Key Cloak. |
| IDP Logout URL | Enter the logout URL of the IDP on which the user will be redirected once signing-out from the ServiceOps portal. If not provided, the user will remain on the same page. This field is optional. |
| IDP Security Certificate | Enter the certificate that IDP provides for integration. The response sent by the IDP is validated using it. |
| SP Entity ID | It displays the entity ID of the Service Provider. You have to configure this in the Key Cloak. |
| Assertion Consumer URL | It displays the endpoint of the ServiceOps application where the IDP posts the SAML responses. You have to configure this in the Key Cloak. |
| SP Single Logout URL | It displays the URL to which the user gets redirected after sign-out. You have to configure this in the Key Cloak. |
| SP Public Key | It is provided by the Service Provider. |
| SP Private Key | It is provided by the Service Provider. |
| Mappings | Map additional fields required for more details. Using this, whenever the values of the mapped fields are changed in the respective provider, they will automatically get updated in ServiceOps. Note: Field Mapping is unsupported for Multi-Select Drop Down, Checkbox, Date Field, and Dependent (Custom Type) field types. |
Step 5: Click Add, and the provider will be displayed on the list page.
Step 7: In Key Cloak, navigate to ServiceOps (Realm) > Realm Settings > General tab, and the below page will appear:
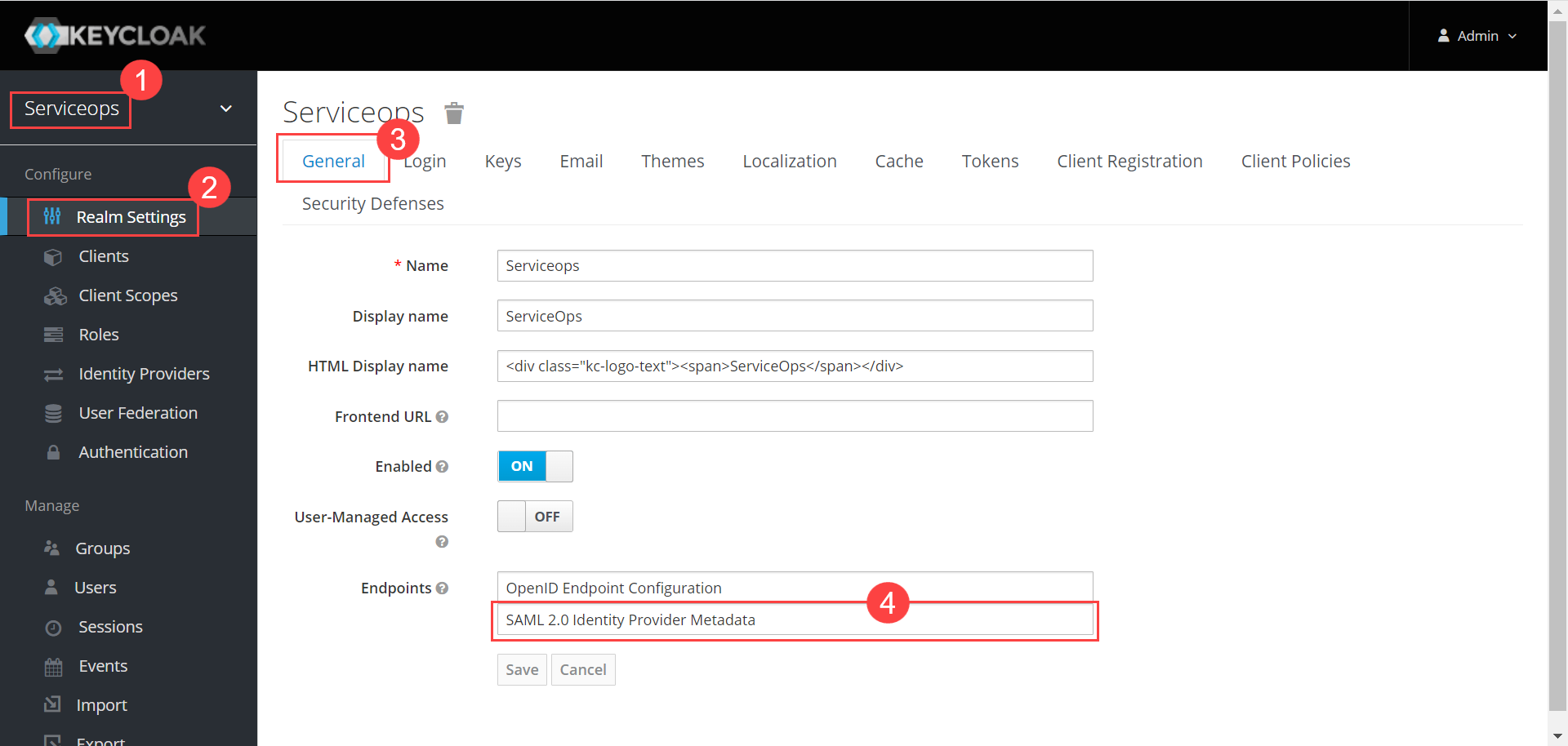
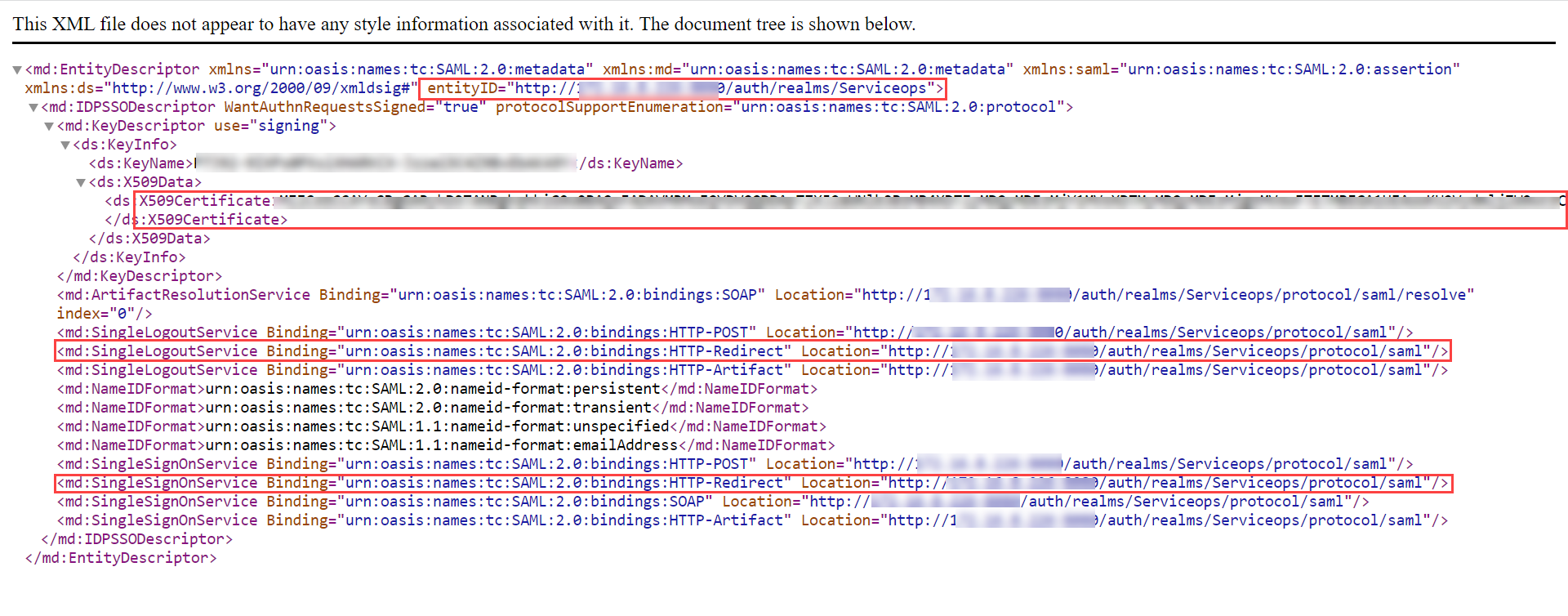
Step 8: Click the SAML 2.0 Identity Provider Metadata, and the XML file appears as shown below. Copy the highlighted Entity ID, Login URL, Logout URL, and the Security Certificate from here and paste them into the ServiceOps.
Step 9: Navigate to Serviceops (Realm) > Identity Providers > saml > Settings tab, as shown below. Configure the following details:
- Service Provider Entity ID
- Single Sign-On Service URL
- Single Logout Service URL
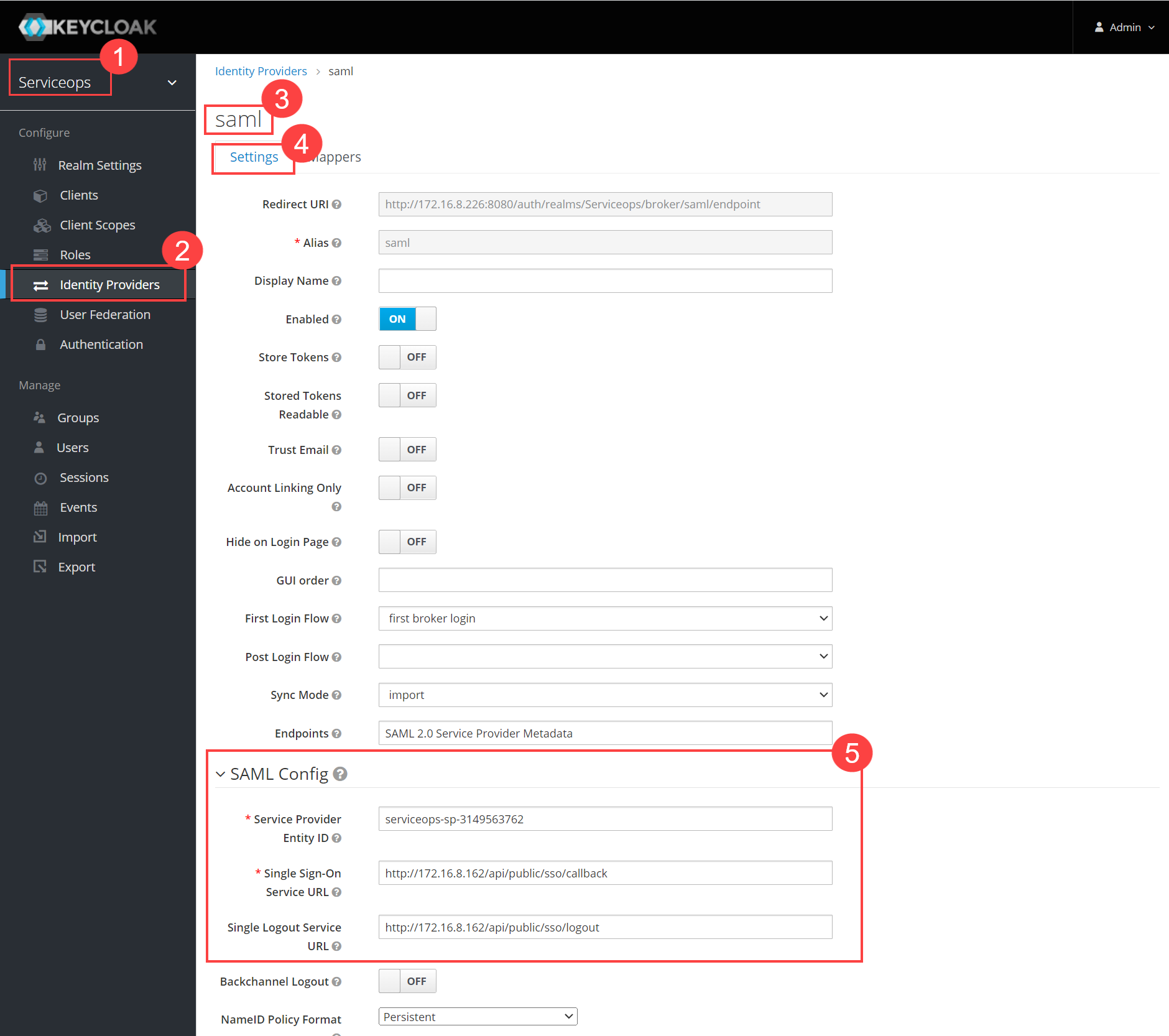
You can get these details from ServiceOps Home page > Admin > Users > SSO Configuration page.

Once added, click Save.
Step 10: Next, navigate to the Clients tab, and click Create.
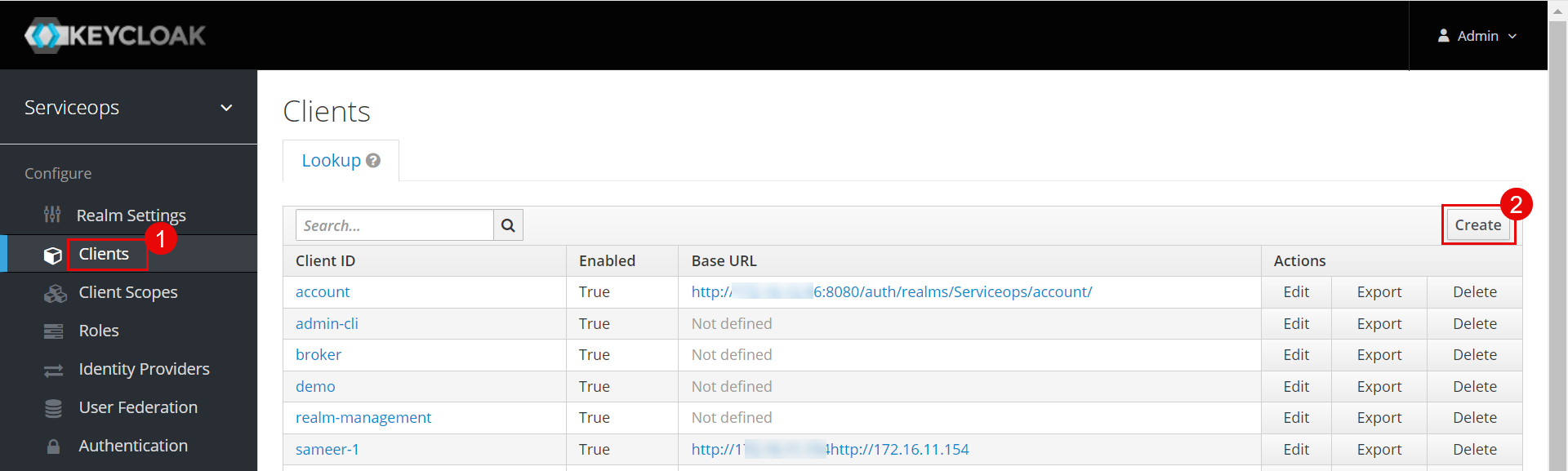
The following screen appears. Enter the below details.
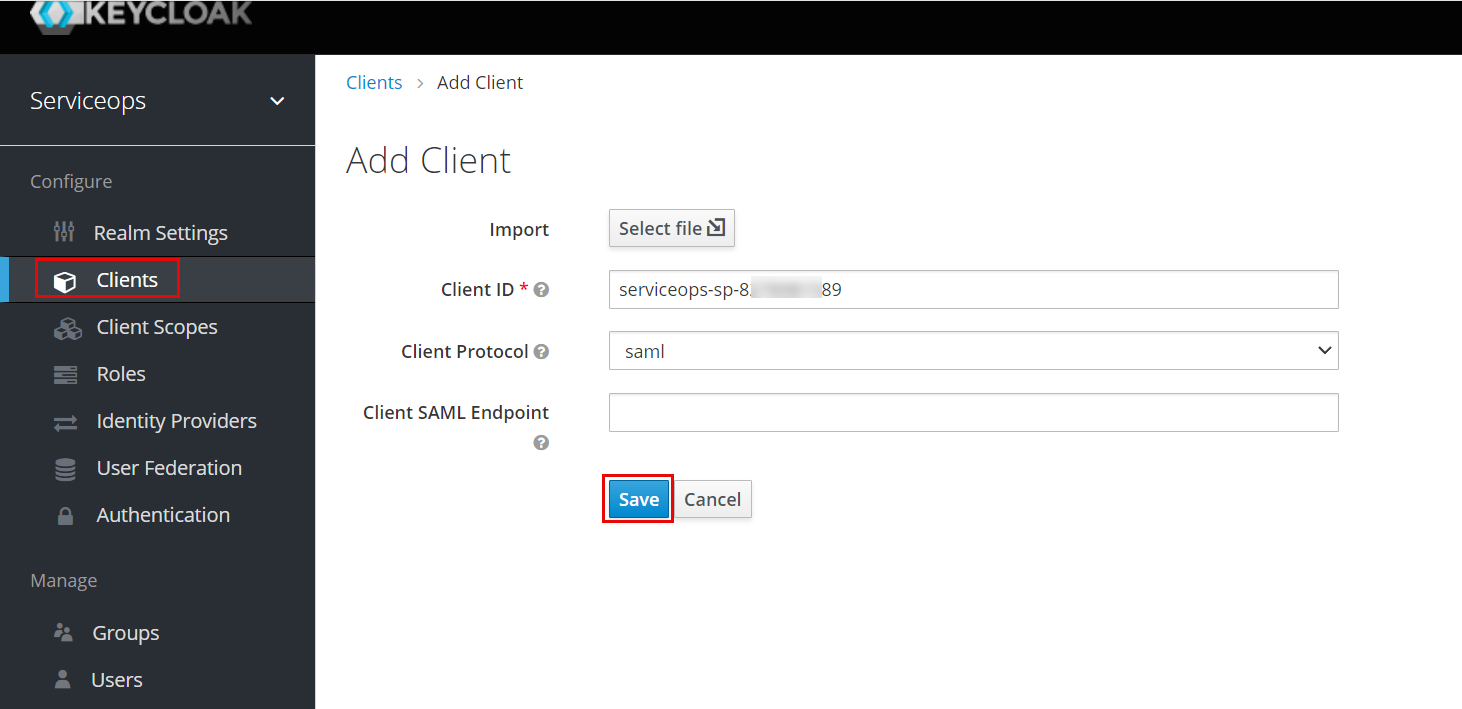
- Copy the Client ID from ServiceOps (SP Entity ID).
- Select the Client Protocol as saml.
- Click Save. The details page will appear.
Step 11: Set the following configurations:
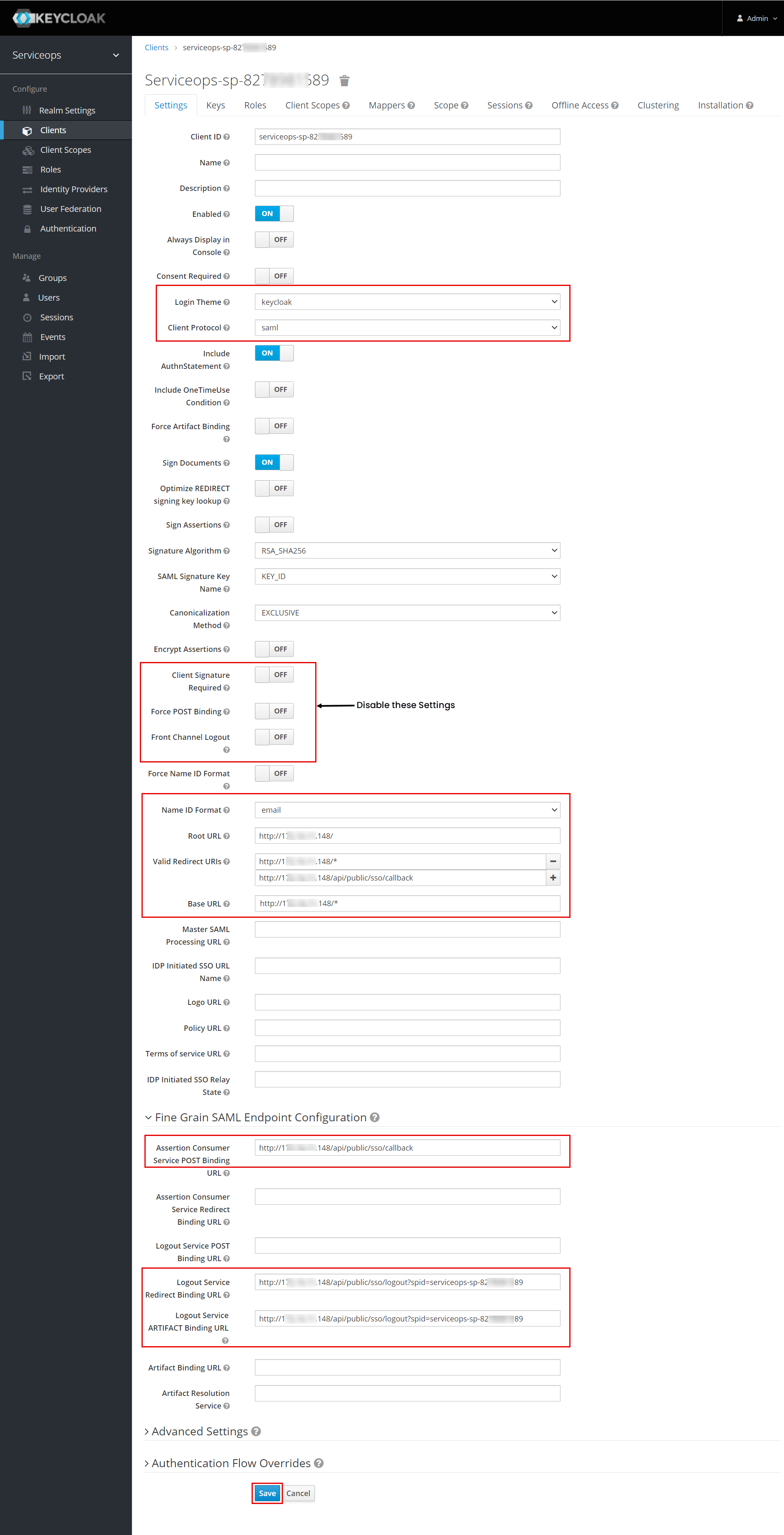
Login Theme: Select the theme as Keycloak.
Disable the following parameters:
- Client Signature Required
- Force POST Binding
- Force Channel Logout
Name ID Format: Select the email option from the dropdown.
Root URL: Enter the ServiceOps URL.
Valid Redirect URIs: Add the Assertion Consumer URL from ServiceOps.
Base URL: Add the ServiceOps Base URL.
Logout Service Redirect Binding URL: Copy and paste the SP Single Logout URL from ServiceOps.
Logout Service ARTIFACT Binding URL: Copy and paste the SP Single Logout URL from ServiceOps.
Once done, click Save. The SSO is now configured.
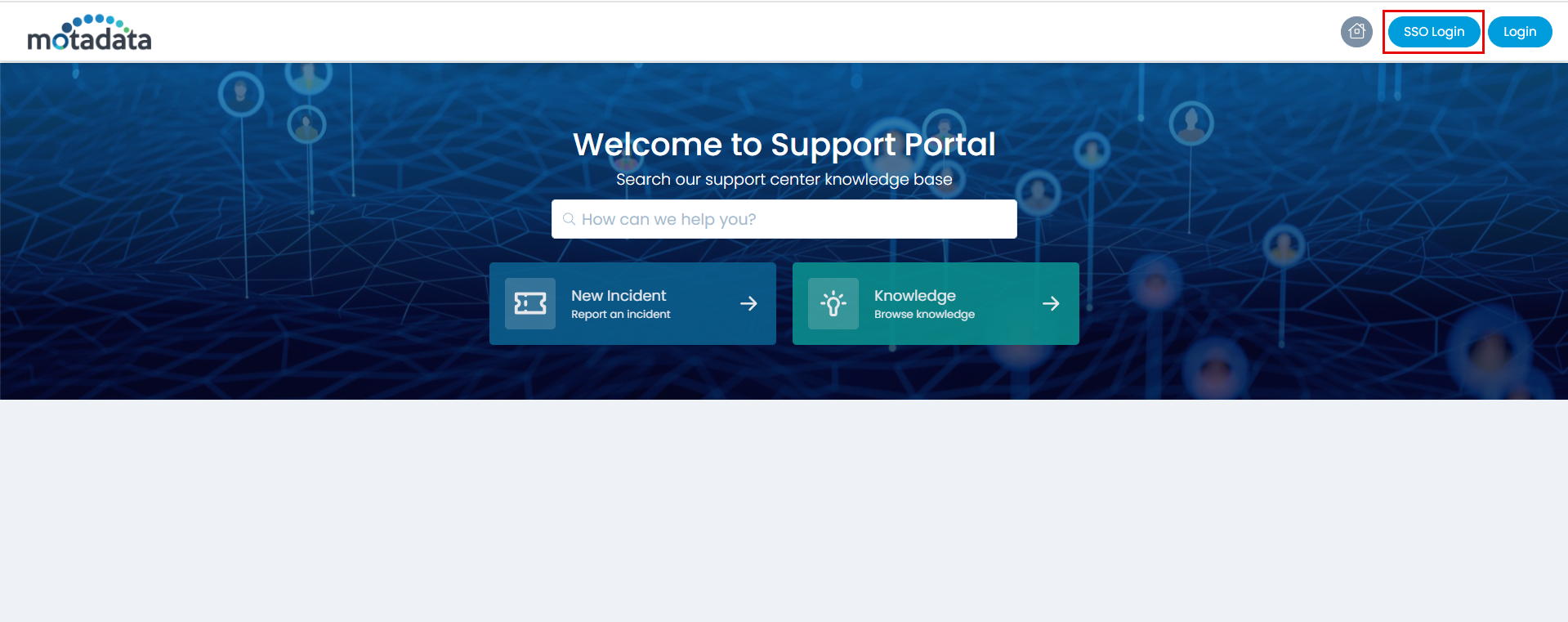
Step 12: You can verify this, by opening the ServiceOps Portal, and signing-in using the SSO Login button as shown below.
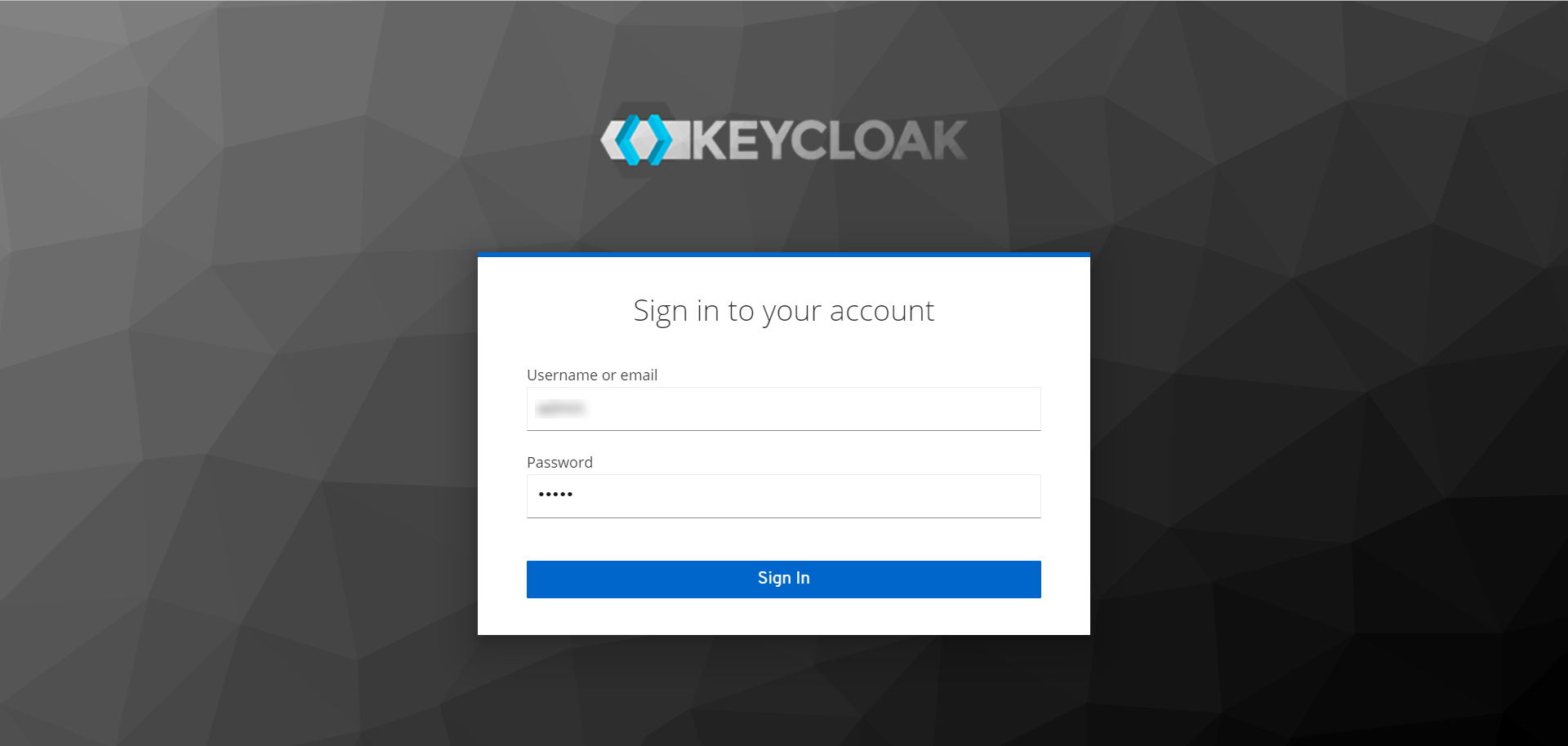
Step 13: You will be redirected to the Key Cloak Sign-in page, as shown below.
Step 14: Sign-in to Key Cloak, and you will be redirected to the ServiceOps portal as shown below.
Step 15: To sign-out, click on the username, and click Sign-Out. You will be redirected to the Key Cloak page again or remain on the portal as per the configured SAML logout URL.
Once the SSO is configured, you can now proceed to import users from the Keycloak directory into ServiceOps, enabling Keycloak users to authenticate via SSO.