Azure AD
ServiceOps offers support for SAML 2.0, which facilitates integration for Single Sign-On. ServiceOps acts as the Service Provider (SP) and it integrates with Identity Providers (IdP) using SAML 2.0. The integration basically involves supplying details about SP to IdP and vice-versa. Once you integrate ServiceOps with an IdP, the users simply have to sign-in to IdP and then, they can automatically sign-in to ServiceOps from the respective identity provider’s GUI without having to provide credentials again. ServiceOps supports integration with Azure.
To configure SSO with the Azure AD service, follow the below steps:
- Sign in to the Microsoft Azure portal.
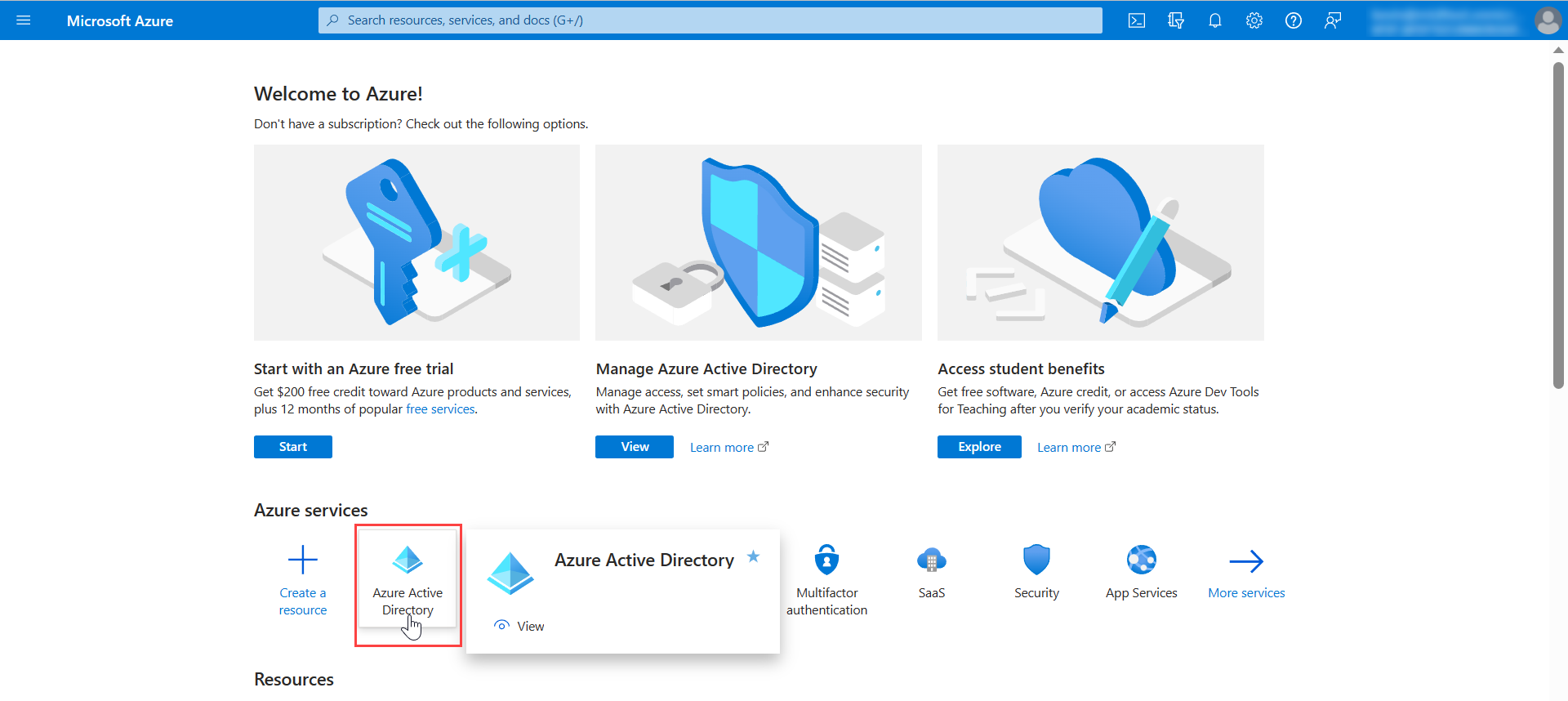
- In the Azure services section, click Azure Active Directory > Enterprise Applications, and click New Application.
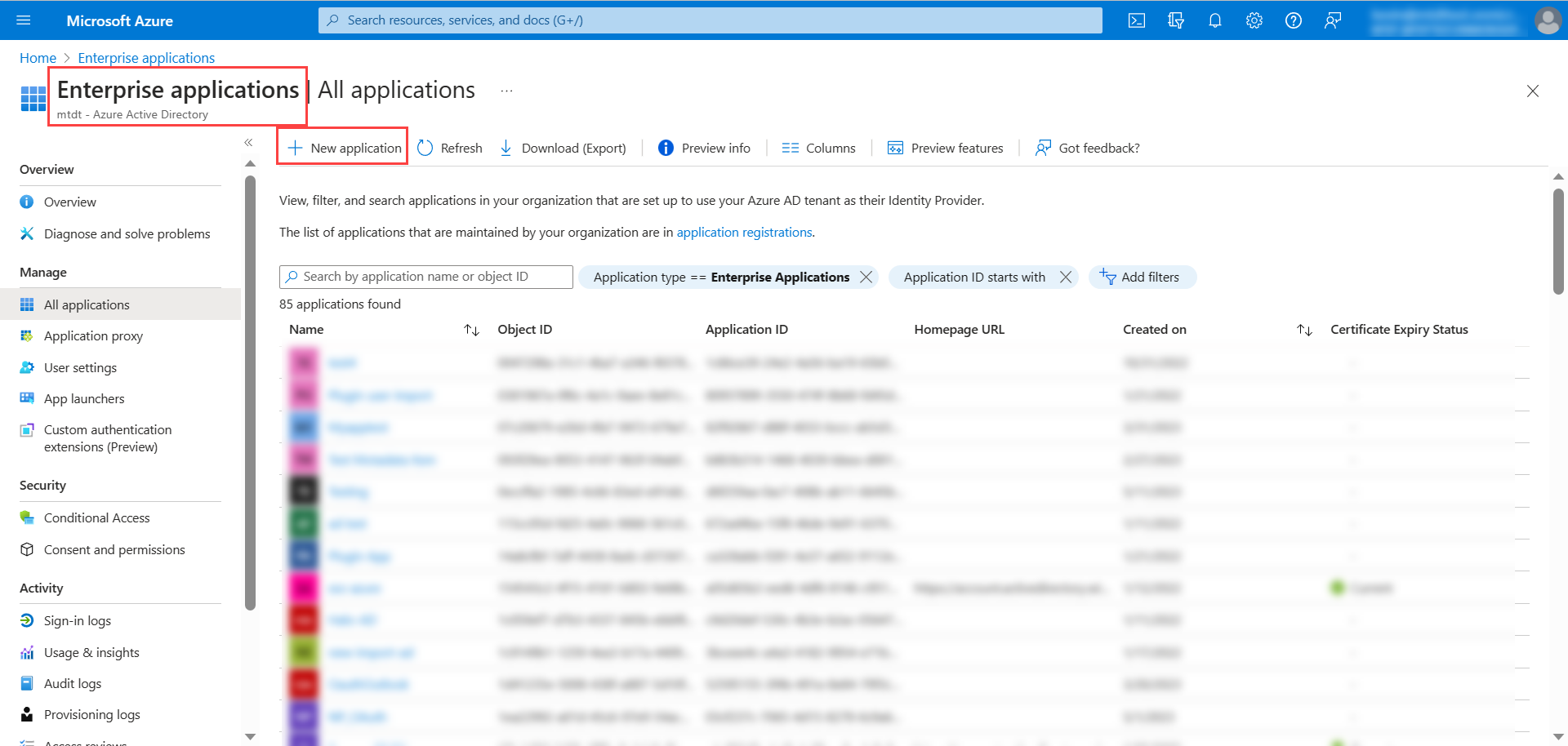
- In the next screen, click Create your own application, enter the app name, select the option "Integrate any other application you don't find in the gallery", and click Create. The app will get created. Here, the app name is SSO App.
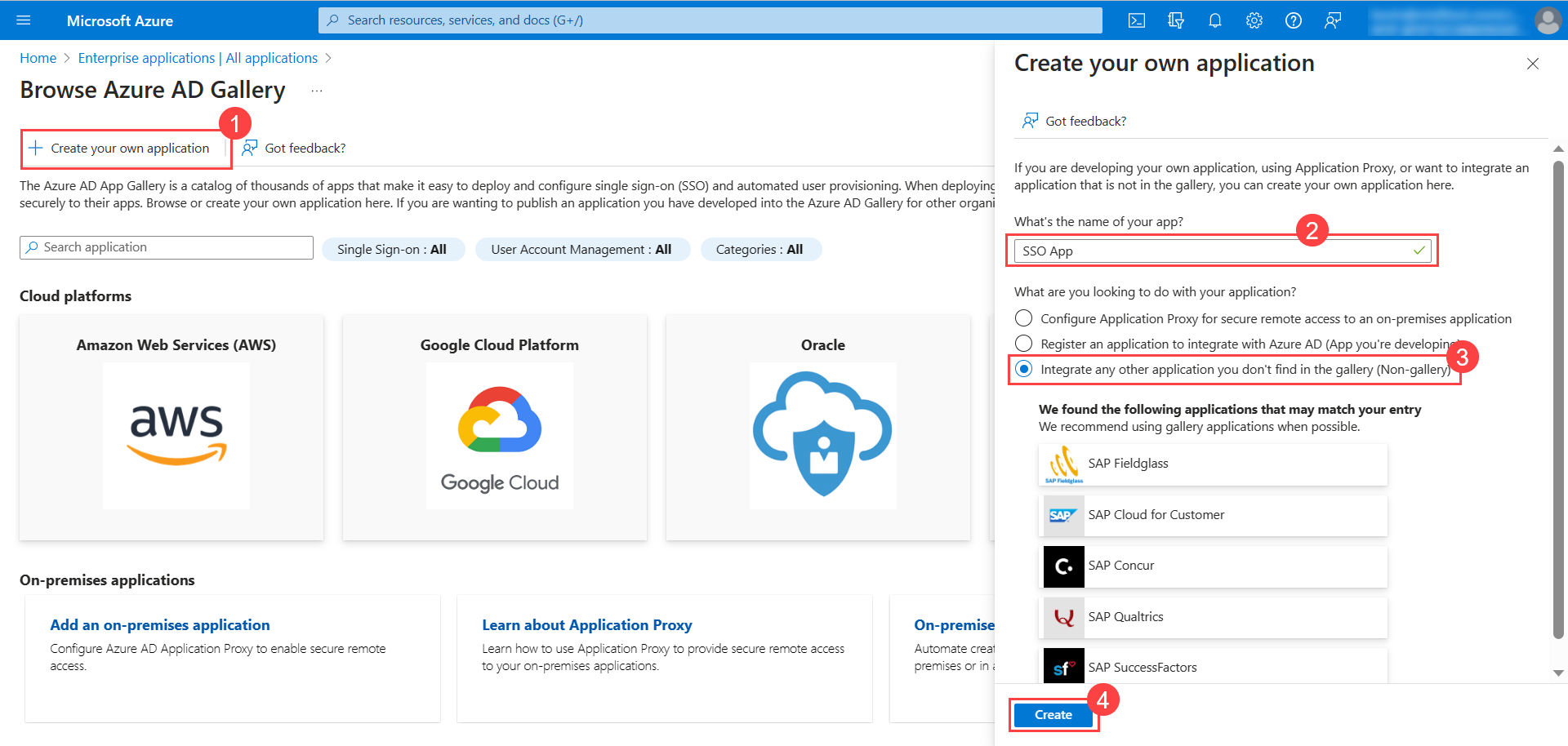
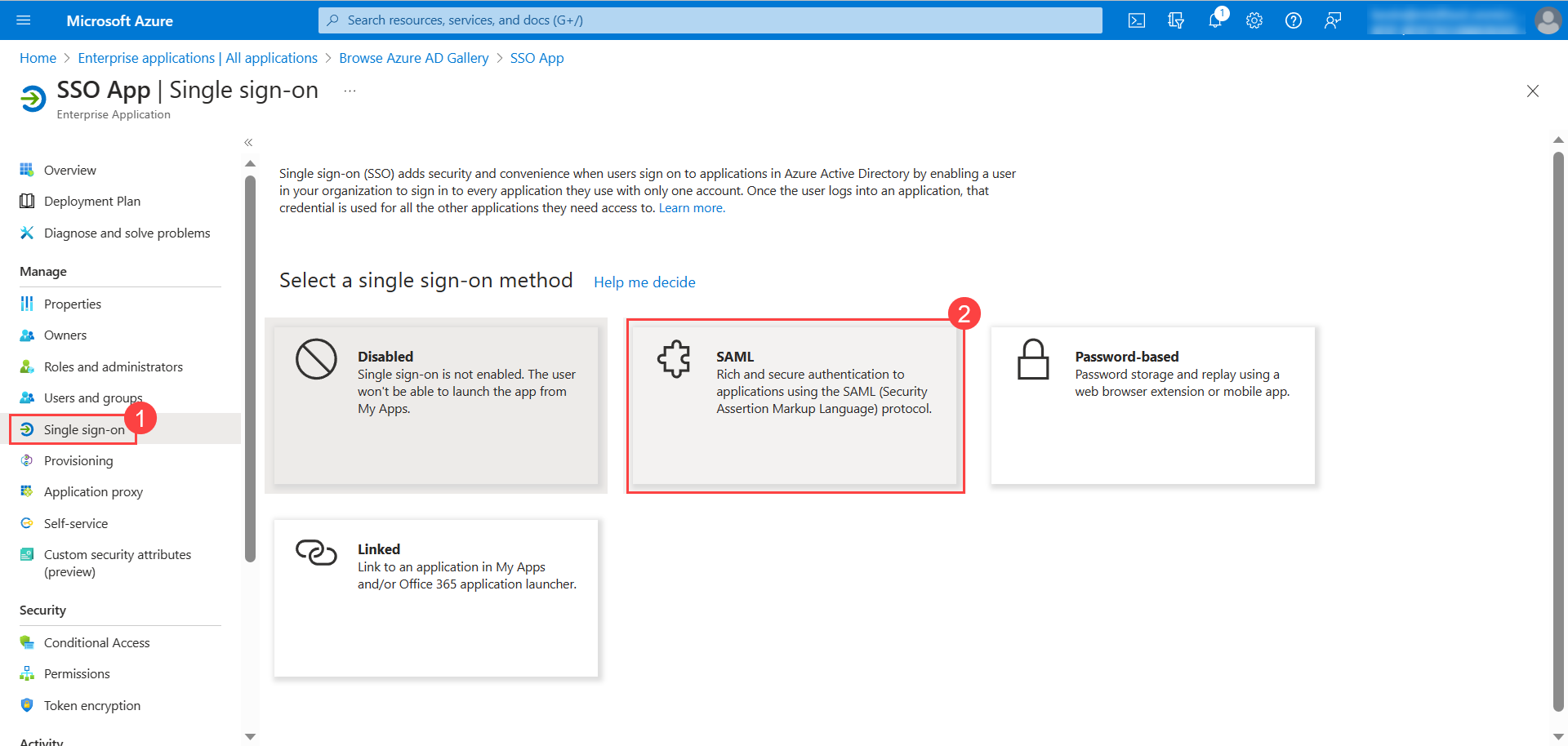
- Next, click Single sign-on from the left panel, and select the method as SAML.
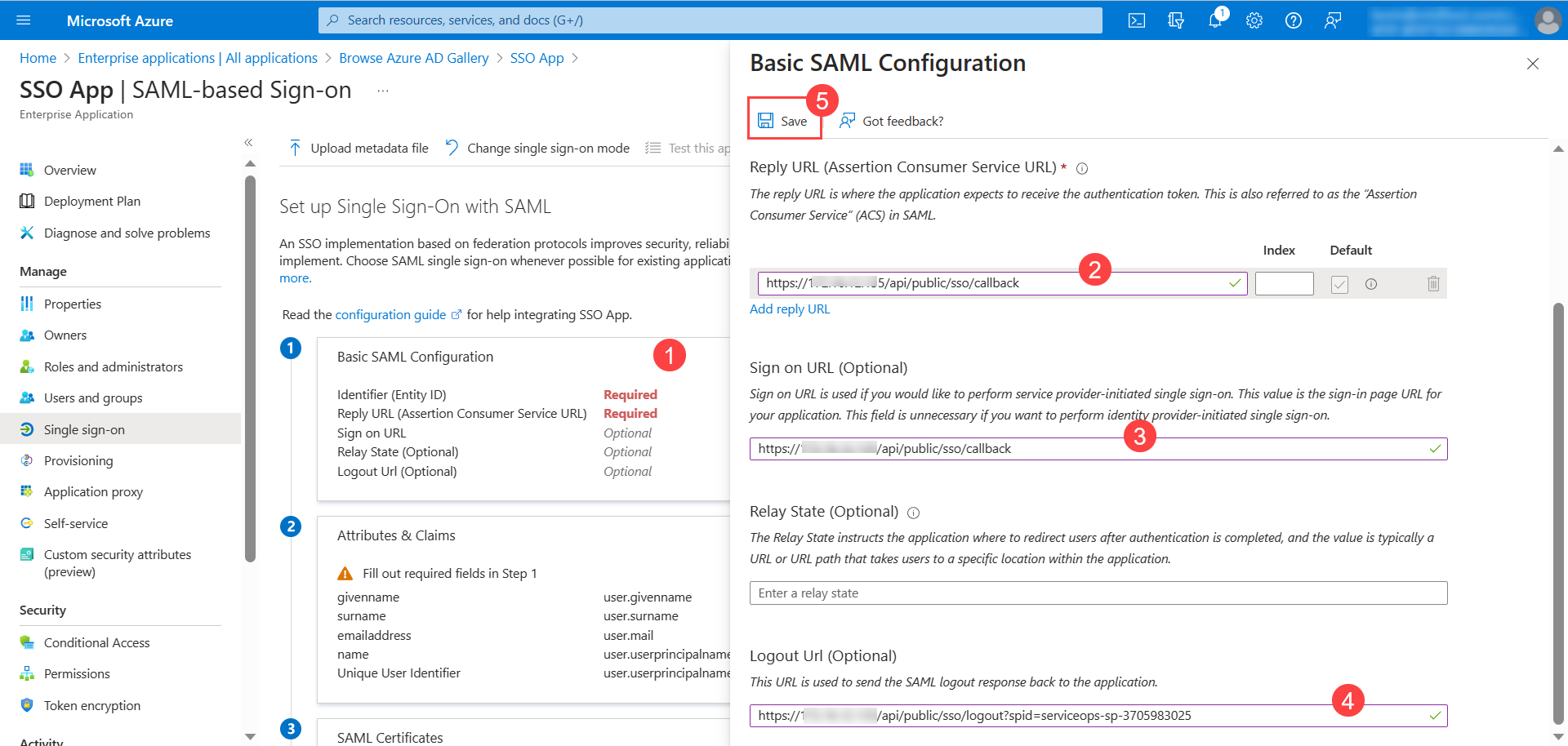
- Edit the Basic SAML Configuration and configure the following details. These are available from ServiceOps.
- Identifier Entity ID
- Reply URL
- Sign-on URL
- Relay State
- Logout URL
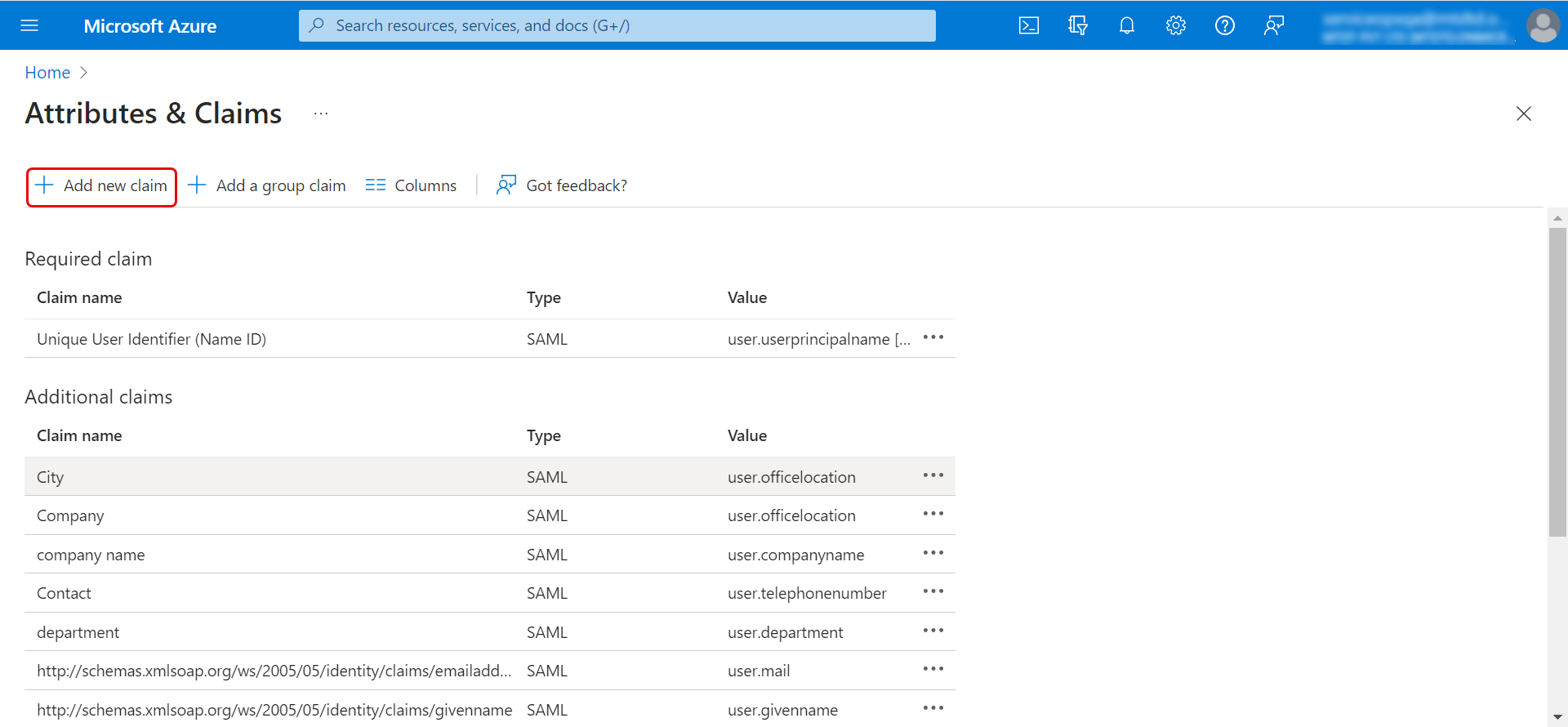
- Edit the Attributes & Claims and add a new claim for mapping the field with the ServiceOps field. Here, Company field is mapped.
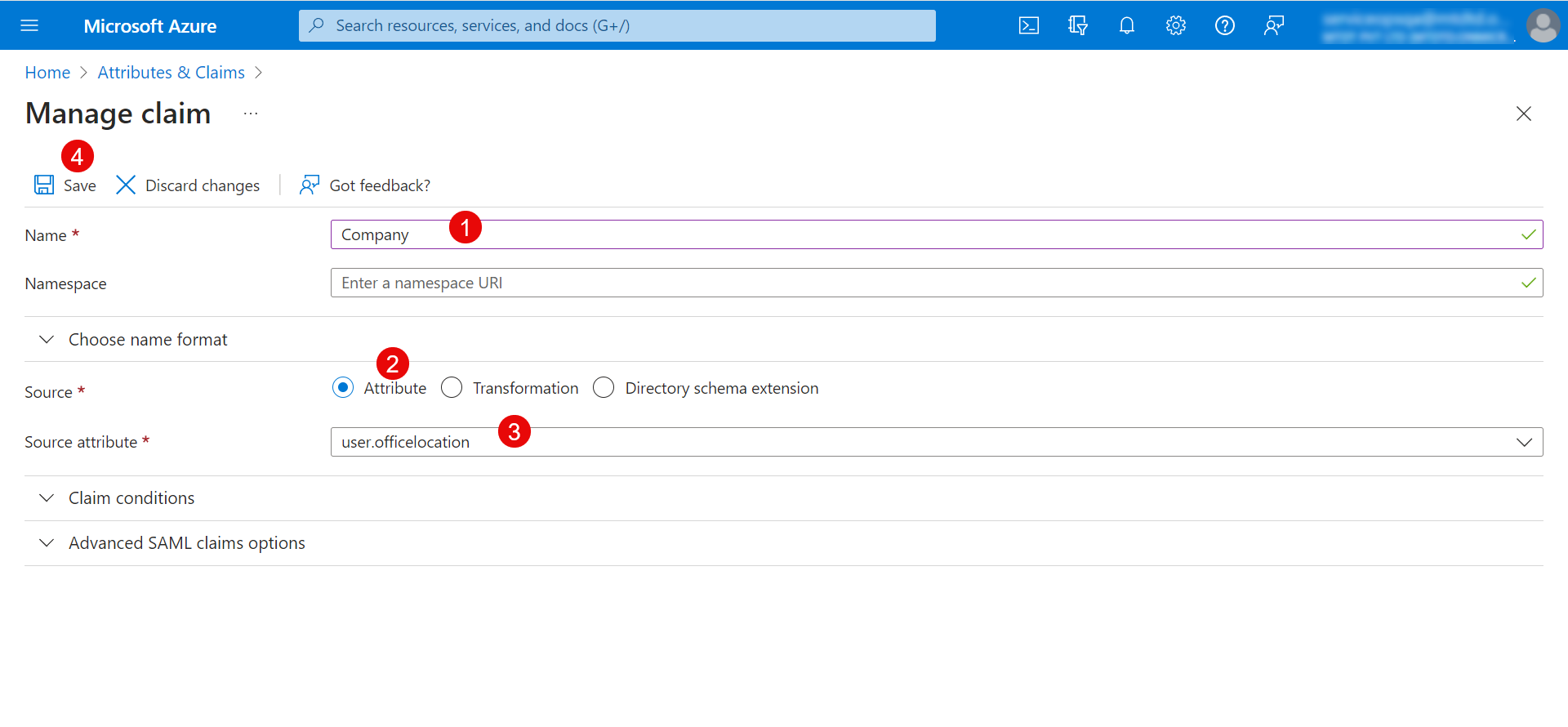
Enter the Name, select Source as Attribute, and enter the Source attribute. Once done, click Save. Similarly, you can map other fields.
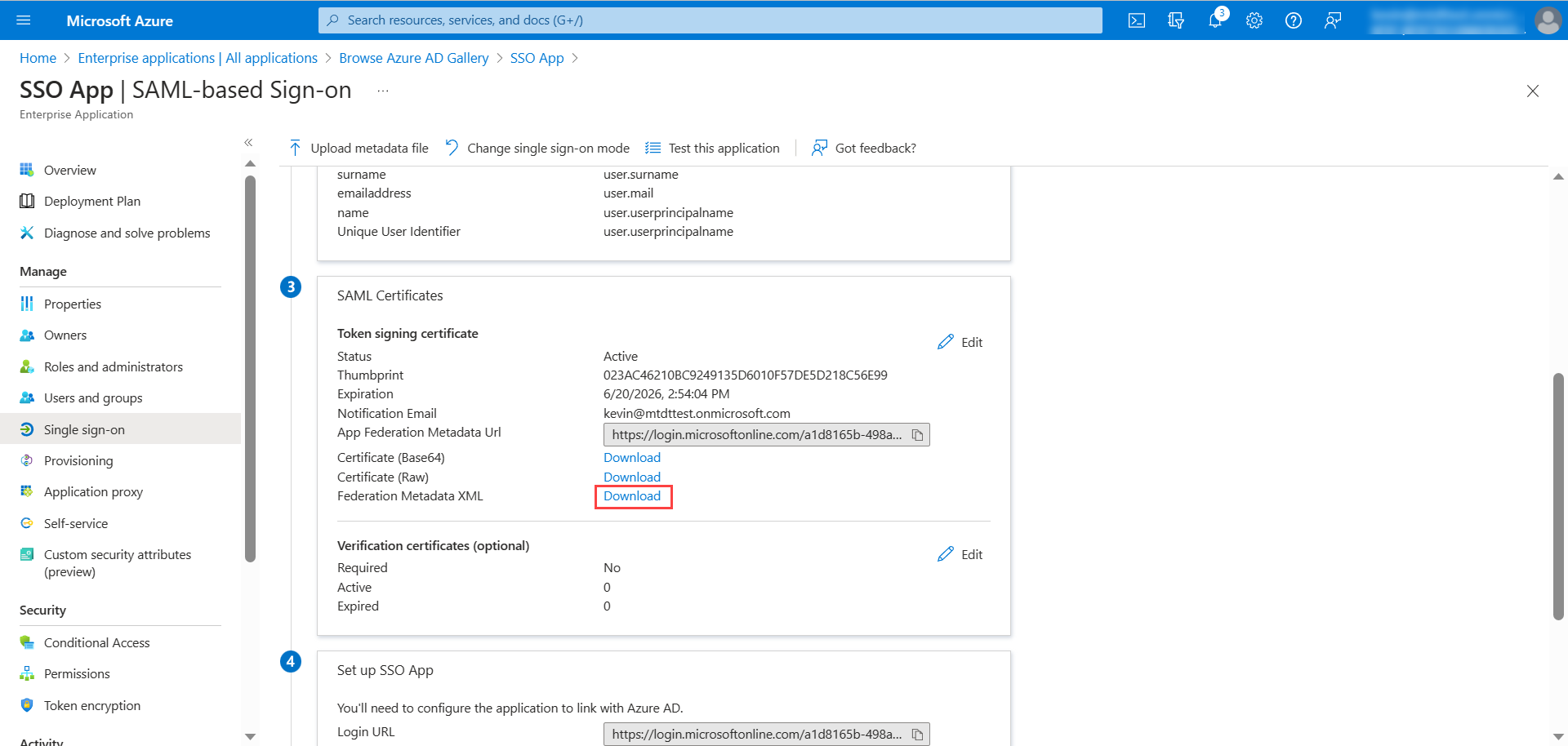
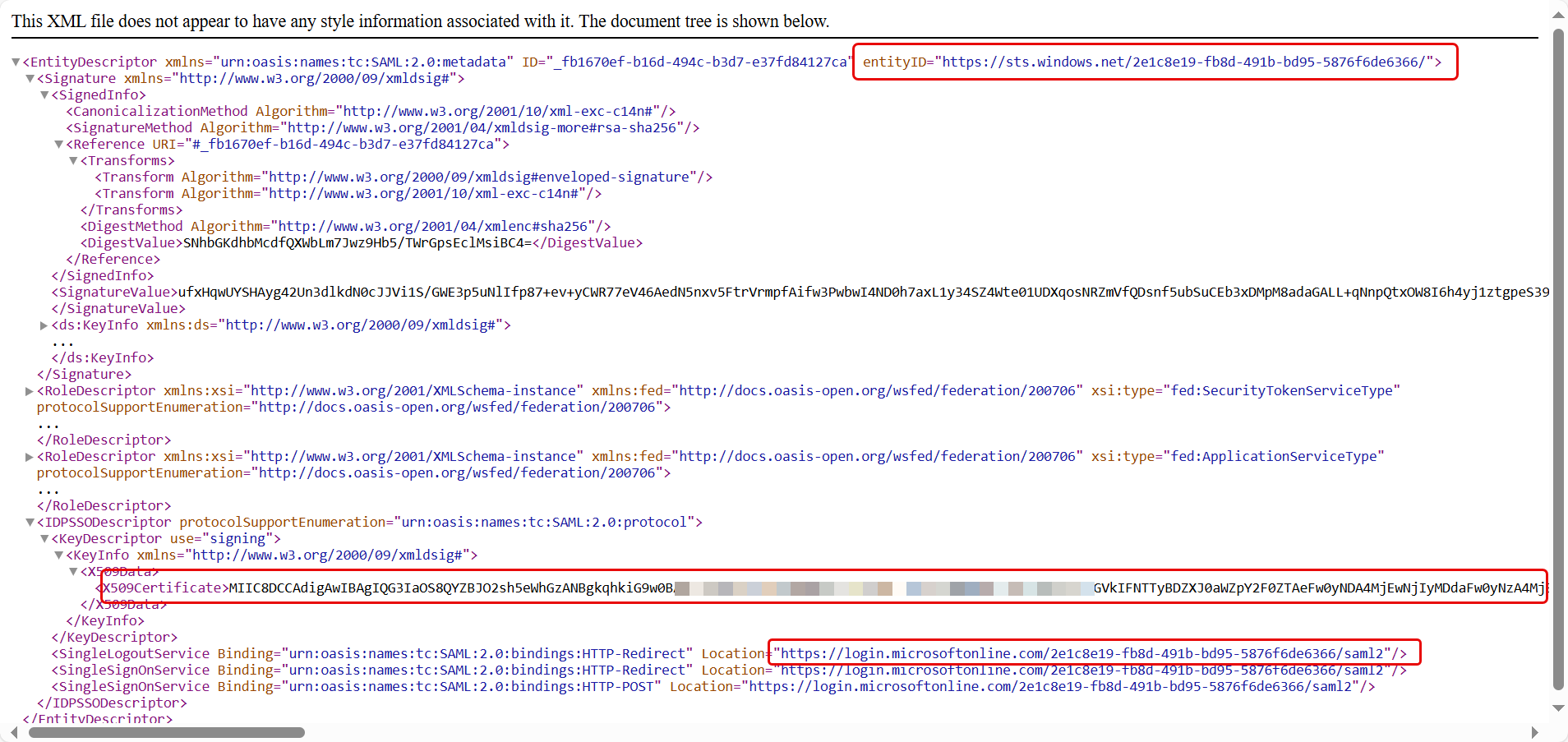
- In the SAML Certificates, download the Federation Metadata XML file, copy the details (entityID, certificate, and logout URL) from it, and paste them in the ServiceOps.
Now, sign-in to the ServiceOps portal as a Technician.
Navigate to Settings > Admin > Users > SSO Configuration > Identity Providers and click Add Identity Provider. The following popup appears.

- Provide the following details. In this, the IDP details of the Azure AD portal are to be configured in the ServiceOps while the SP details in the Azure AD. The IDP details are available in the metadata file downloaded from Azure in the point no.7.
| Parameter | Description |
|---|---|
| Name | Enter the name of the identity provider. |
| Identity Provider | Select the Identity Provider as Azure AD/Office 365 to login. |
| Auto Create User | Enable if the user is to be created automatically, if not available in the system. By default, disabled. |
| IDP Entity ID | Enter the Entity ID of the IDP from the metadata file. It is a mandatory field. |
| IDP Login URL | Enter the login URL of the IDP on which the user will get redirected. It is a mandatory field. You can get this from the metadata file. |
| IDP Logout URL | Enter the logout URL of the IDP on which the user will be redirected once signing-out from the ServiceOps portal. If not provided, the user will remain on the same page. This field is optional. |
| IDP Security Certificate | Enter the certificate that IDP provides for integration. The response sent by the IDP is validated using it. |
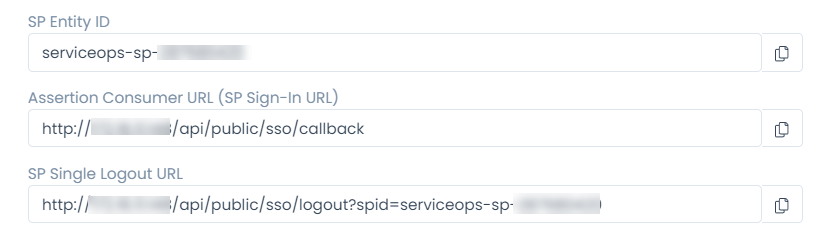
| SP Entity ID | It displays the entity ID of the Service Provider. You have to configure this in the Azure portal. |
| Assertion Consumer URL | It displays the endpoint of the ServiceOps application where the IDP posts the SAML responses. You have to configure this in the Azure portal. |
| SP Single Logout URL | It displays the URL to which the user gets redirected after sign-out. You have to configure this in the Azure portal. |
| SP Public Key | It is provided by the Service Provider. |
| SP Private Key | It is provided by the Service Provider. |
| Mappings | Map additional fields required for more details. Using this, whenever the values of the mapped fields are changed in the respective provider, they will automatically get updated in ServiceOps. Note: Field Mapping is unsupported for Multi-Select Drop Down, Checkbox, Date Field, and Dependent (Custom Type) field types. |
Click Add, and the provider will be displayed on the list page. The SSO is now configured.
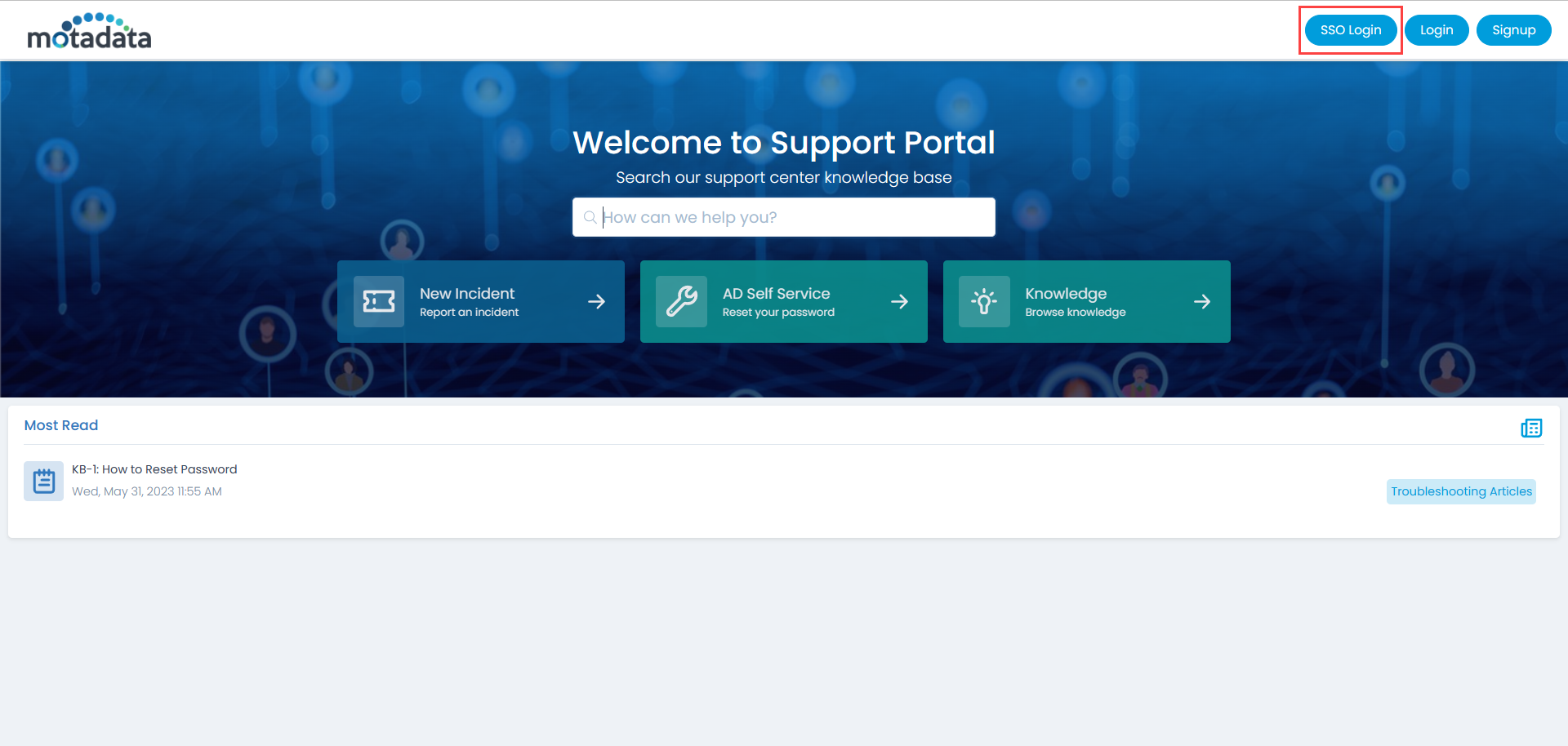
You can verify this, by opening the ServiceOps Portal, and signing-in using the SSO Login button as shown below.
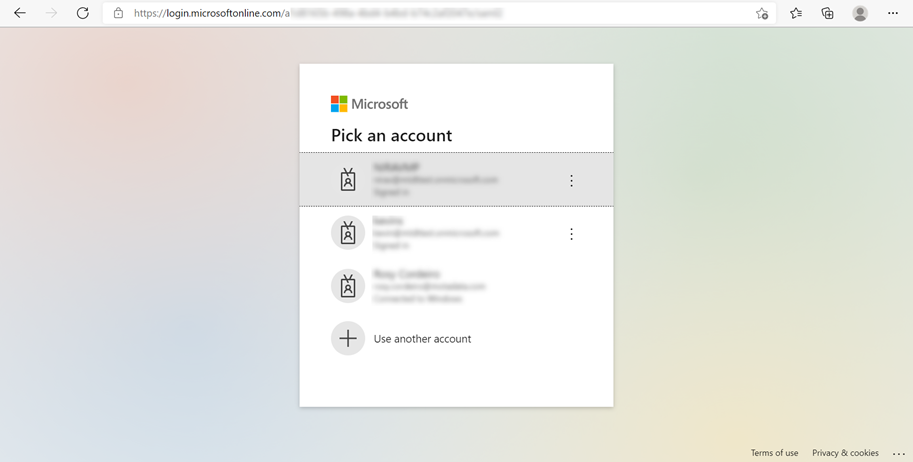
- You will be redirected to the Microsoft Azure sign-in page, as shown below.
- Sign-in to Microsoft Azure, and you will be redirected to the ServiceOps Portal. For Signing out, go to username, and click Sign-Out. You will be redirected again to the Microsoft Azure page.
After configuring SSO, you can proceed to import users from the Azure directory into ServiceOps, enabling Azure users to authenticate via SSO.