Discovery
Asset Discovery is the feature that discovers the assets in the network for asset management. It supports both On-Premise and SaaS-based platforms. Using Asset Management, the admin maintains the records of all the hardware or software assigned to each employee.
Here, Motadata ServiceOps helps in maintaining as well as discovering all the possessed asset records in just one application. In addition, it adds with the asset’s number and exact names. Thus, Asset Discovery helps to find all the assets of each single network or single location using various features such as network scan, domain scan, and SCCM scan. Moreover, adding multiple Credentials for successful network connection will ultimately show the discovery of the assets after the scan.
Supported OS Version List
Linux OS Version List:
The * marked OS versions are not supported for patch management.
| Linux OS | Version |
|---|---|
| Ubuntu |
|
| CentOS | 9 and 10 (Stream) |
| RedHat | 9.5, Core, 8, 7, 6 |
| Mint | 20, 19, 18* |
| openSUSE/SUSE | 15.6, 15.5, 15.4*, 15.3* |
| Debian | 12, 11, 10*, 9*, 8* |
| Oracle Linux | 9, 8, 7 |
| Fedora OS | - |
| SunOS | - |
| VMware | - |
| VMware Photon | - |
| Solaris | - |
| IBM | AIX, VIO |
| Rocky Linux | 9.5 |
| Almas Linux | 9.5 |
Mac OS Version List
- macOS ("10.15", "10.16", "12", "13", "14")
Windows Server OS List:
- Windows Server 2012
- Windows Server 2016
- Windows Server 2019
- Windows Server 2022
Windows OS Version List
- Windows OS v10 and above
Assets can be discovered in two ways:
- Using Discovery Service: This is used in the On-premise ServiceOps application for discovering the assets (Agentless and Agent-based). To discover the agent-based assets, Motadata ServiceOps agent is required to be installed in the target machines. To install the agent, refer to the Agent Installation Guide. To discover the agentless assets, use the features like Network Scan, Domain Scan, Cloud Network, and SCCM Scan.
Prerequisites for Asset Discovery:
To perform Agentless Asset Discovery, run the below commands using the Powershell application v3.0 or above with Run as Administrator rights:
set-WSManQuickConfig -Force
enable-PSRemoting -SkipNetworkProfileCheck -Force
set-Item -Force WSMan:\localhost\Client\TrustedHosts -Value {ServiceOps IP or hostname/Poller IP}
set-Item -Force WSMan:\localhost\Service\AllowUnencrypted -value 'true'
set-Item -Force WSMan:\localhost\Service\Auth\Basic -value 'true'
set-Item -Force WSMan:\localhost\Service\MaxConnections -value '100'
set-Item -Force WSMan:\localhost\Service\MaxConcurrentOperationsPerUser -value '4294967295'
set-Item -Force WSMan:\localhost\Service\MaxConcurrentOperations -value '4294967295'
set-Item -Force WSMan:\localhost\Shell\MaxMemoryPerShellMB -value '1024'
set-Item -Force WSMan:\localhost\Shell\MaxProcessesPerShell -value '2147483647'
set-Item -Force WSMan:\localhost\Shell\MaxConcurrentUsers -value '100'
set-Item -Force WSMan:\localhost\Shell\MaxShellsPerUser -value '2147483647'
set-Item -Force WSMan:\localhost\MaxEnvelopeSizeKb -value '8192'
net stop winrm
net start winrm
| Command | Description |
|---|---|
| set-WSManQuickConfig -Force | This command configures the WinRM service to enable remote management. The `-Force` parameter is used to automatically configure WinRM without prompting for confirmation. |
| enable-PSRemoting -SkipNetworkProfileCheck -Force | This command enables PowerShell remoting, which allows remote management of Windows computers using PowerShell commands. The -SkipNetworkProfileCheck parameter allows remoting in public networks. The '-Force' parameter enables remoting without prompting for confirmation. |
| set-Item -Force WSMan:\localhost\Client\TrustedHosts -Value (ServiceOps IP or hostname/Poller IP) | This command sets the list of trusted hosts for WinRM client. You need to replace (ServiceOps IP or hostname/Poller IP) with the IP address or hostname of the ServiceOps system or the Poller system, whichever system you want to trust for remote management. |
| set-Item -Force WSMan:\localhost\Service\AllowUnencrypted -value 'true' | This command allows unencrypted WinRM connections. |
| set-Item -Force WSMan:\localhost\Service\Auth\Basic -value 'true' | This command enables basic authentication for WinRM connections, providing a simple authentication mechanism for remote management. |
In case the Powershell application is disabled, fulfill the below prerequisites:
UAC should be allowed. The user can allow this in two ways:
Manually by going to the path “Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System” and setting the value of “LocalAccountTokenFilterPolicy” parameter as “1”.
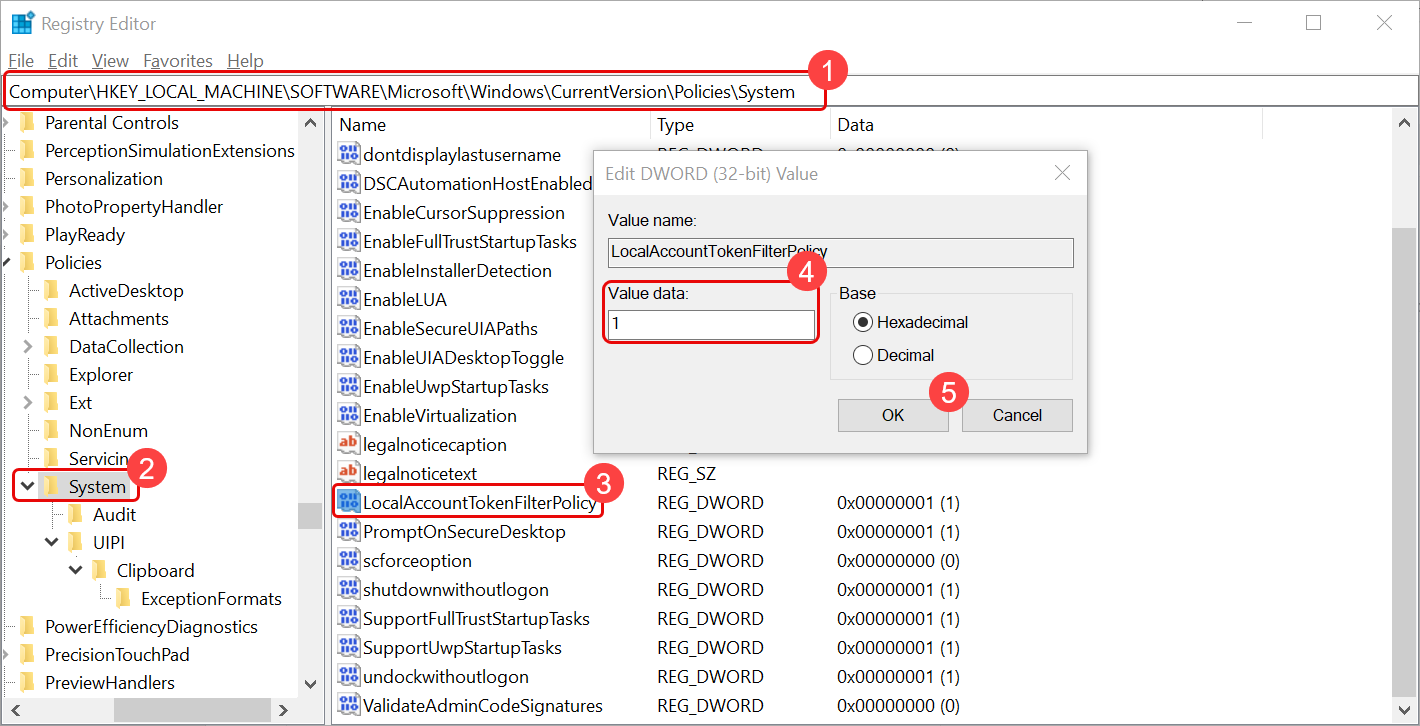
Once done, reboot the machine.
Directly executing the below command in the Command Prompt using Run As Administrator rights.
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\system /v LocalAccountTokenFilterPolicy /t REG_DWORD /d 1 /f
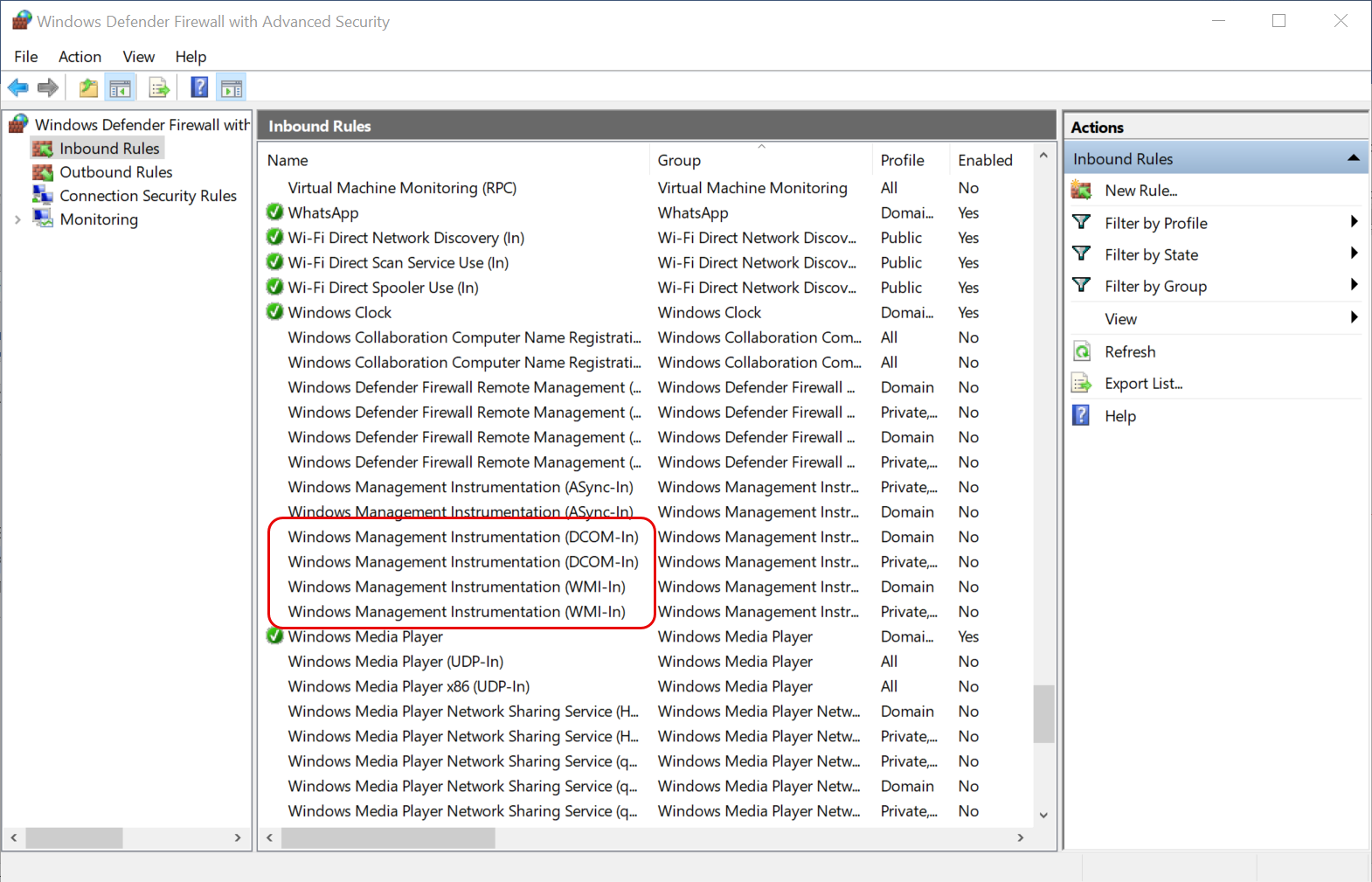
If the Firewall is ON, allow the below Inbound Rules:
- Windows Management Instrumentation (DCOM-In) (Private, Public)
- Windows Management Instrumentation (DCOM-In) (Domain)
- Windows Management Instrumentation (WMI-In) (Private, Public)
- Windows Management Instrumentation (WMI-In) (Domain)
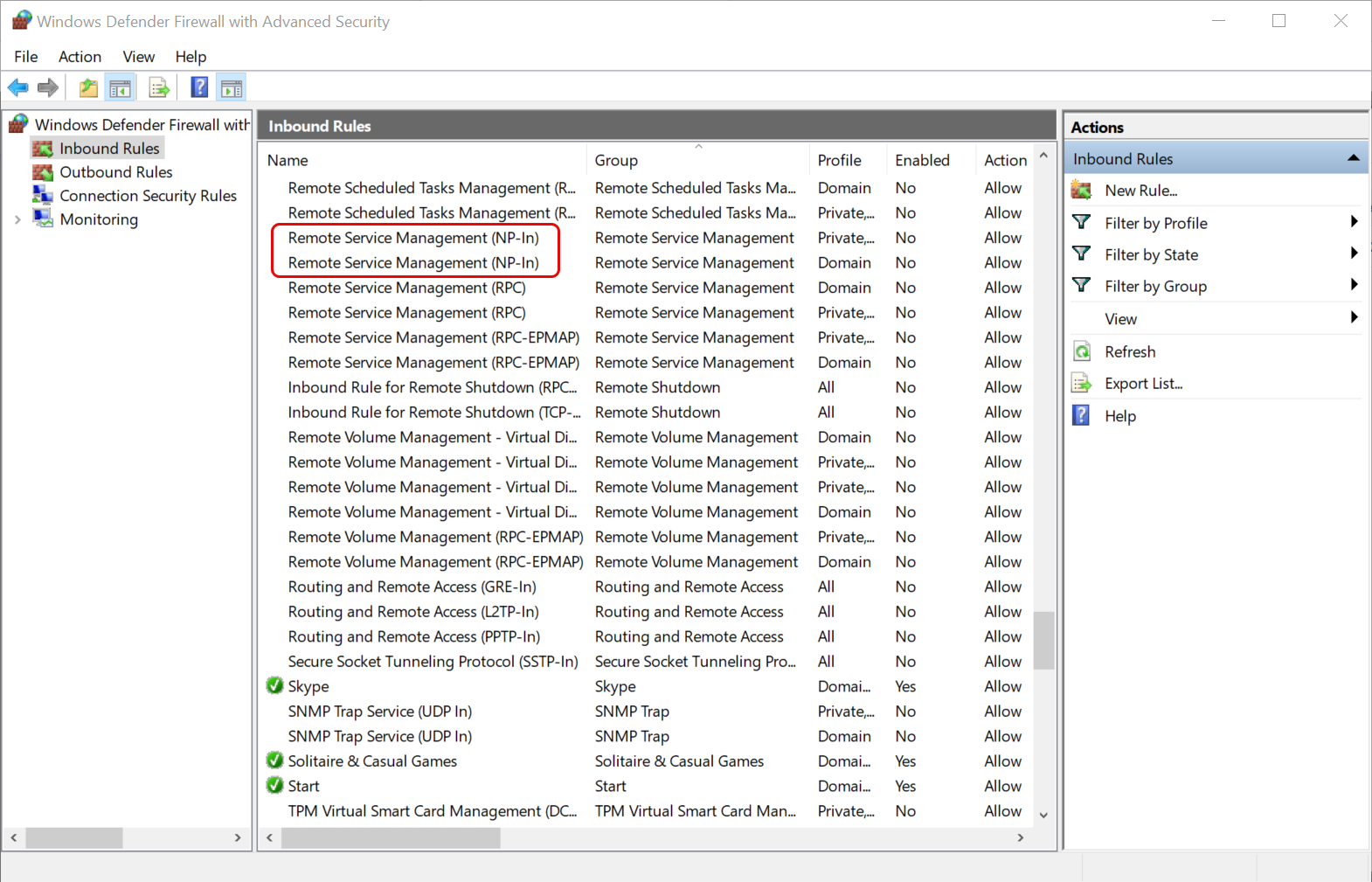
- If the Firewall is ON, allow the below Inbound Rules:
- Remote Service Management (NP-In) (Private, Public)
- Remote Service Management (NP-In) (Domain)
To check whether the server can communicate with the Agent, use the below command:
python3 /opt/flotomate/main-server/config/impacket/examples/wmiexec.py {user_name}:{password}@{ip} "wmic os get Name"Using Discovery Poller Service: This is used in the SaaS-based as well as On-Premise ServiceOps application. It discovers the assets in the local network behind the firewall and also remote offices. To achieve this, the Poller service is required to be installed in the network in which the assets are available. To install the Poller Service, refer to the Poller Service Installation Guide.
To view the Asset Discovery page, navigate to Admin > Discovery and Agents > Discovery.
Discovery Service
This page shows the list of all assets discovered either by using the poller service or without it. When a scan is manually performed or scheduled, all the assets list down here in numbers.
It displays three tabs: Pending Scan, Running Scan and Completed Scan.
Pending Scan
This tab displays the scan that is in pending state. Once it starts running, it will be moved to the Running Scan tab.
This tab is available only if Poller service is selected.
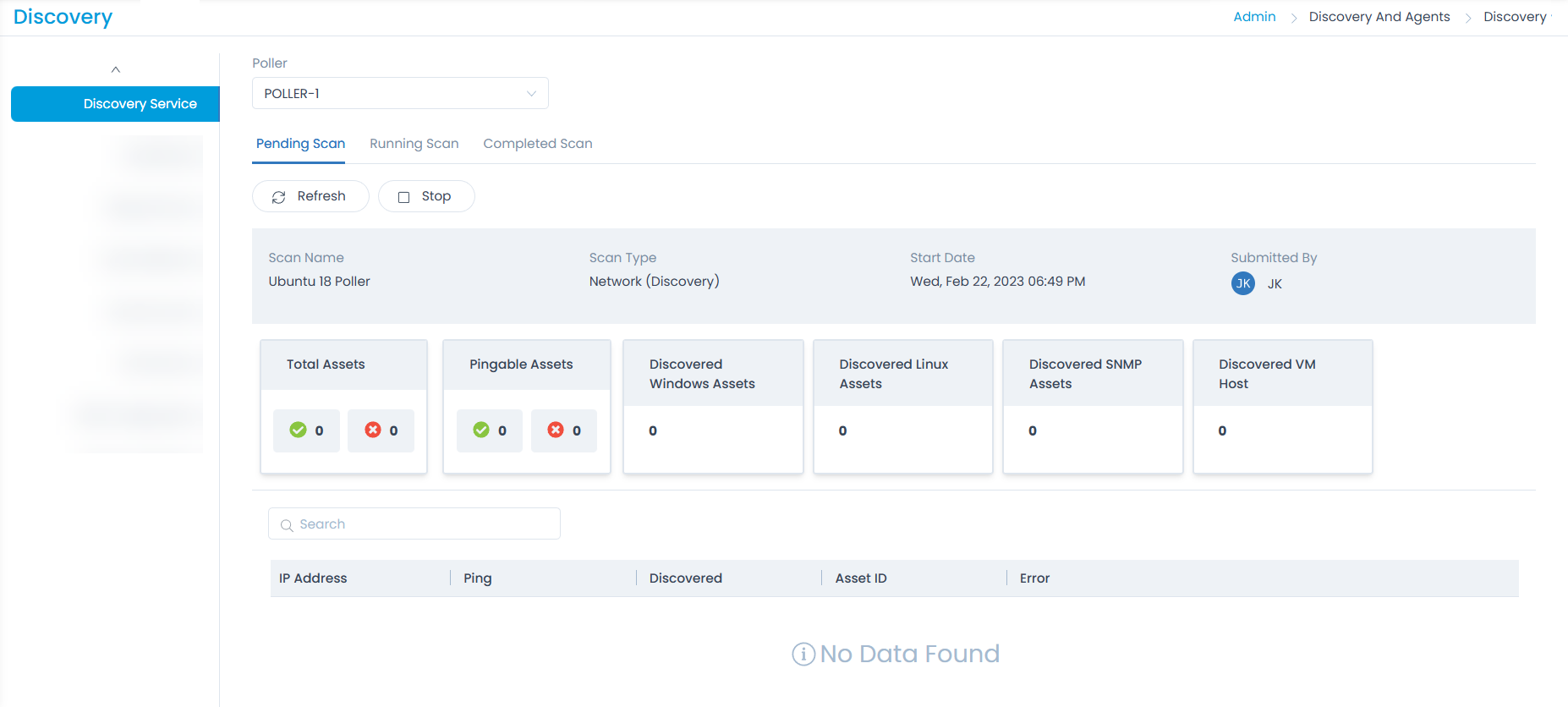
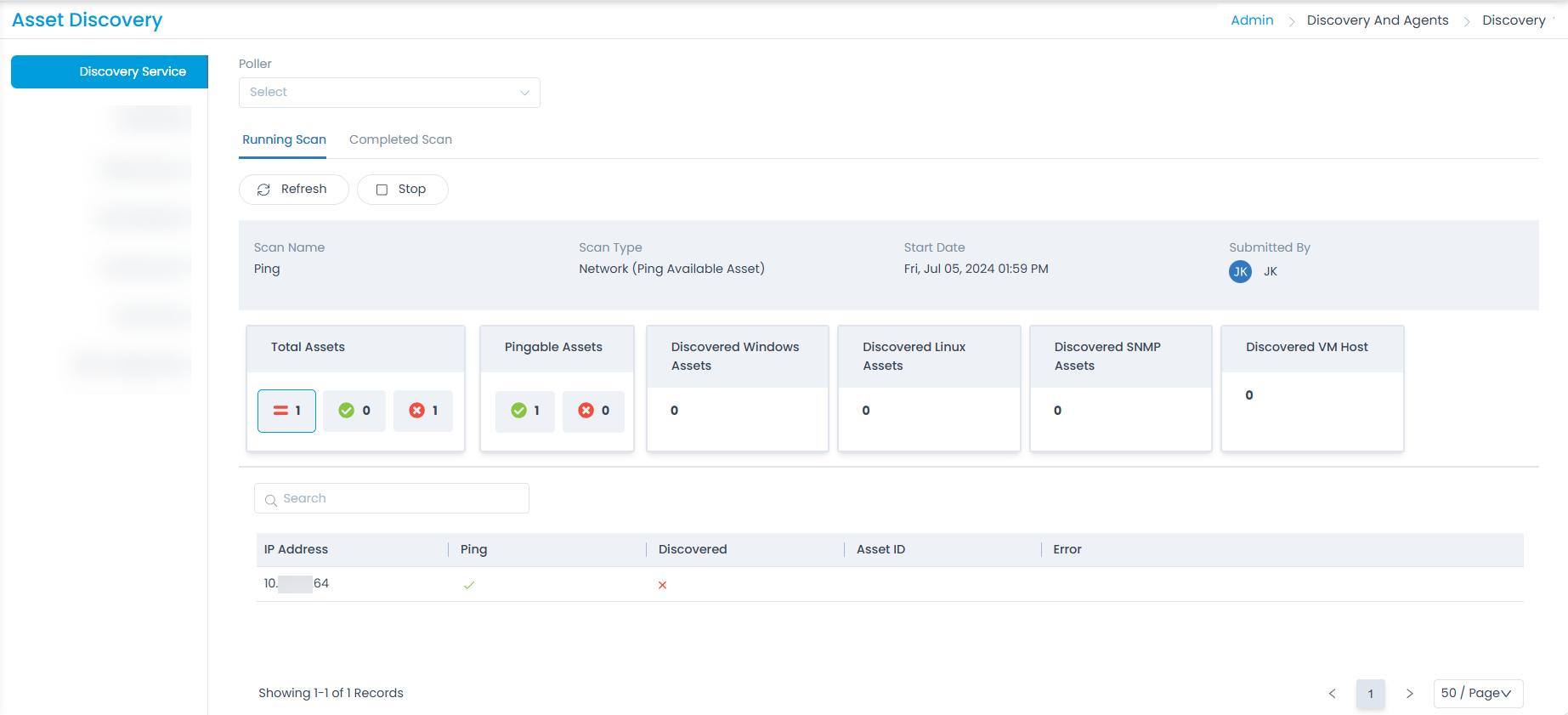
Running Scan This tab displays the scan currently running along with the details as shown below.
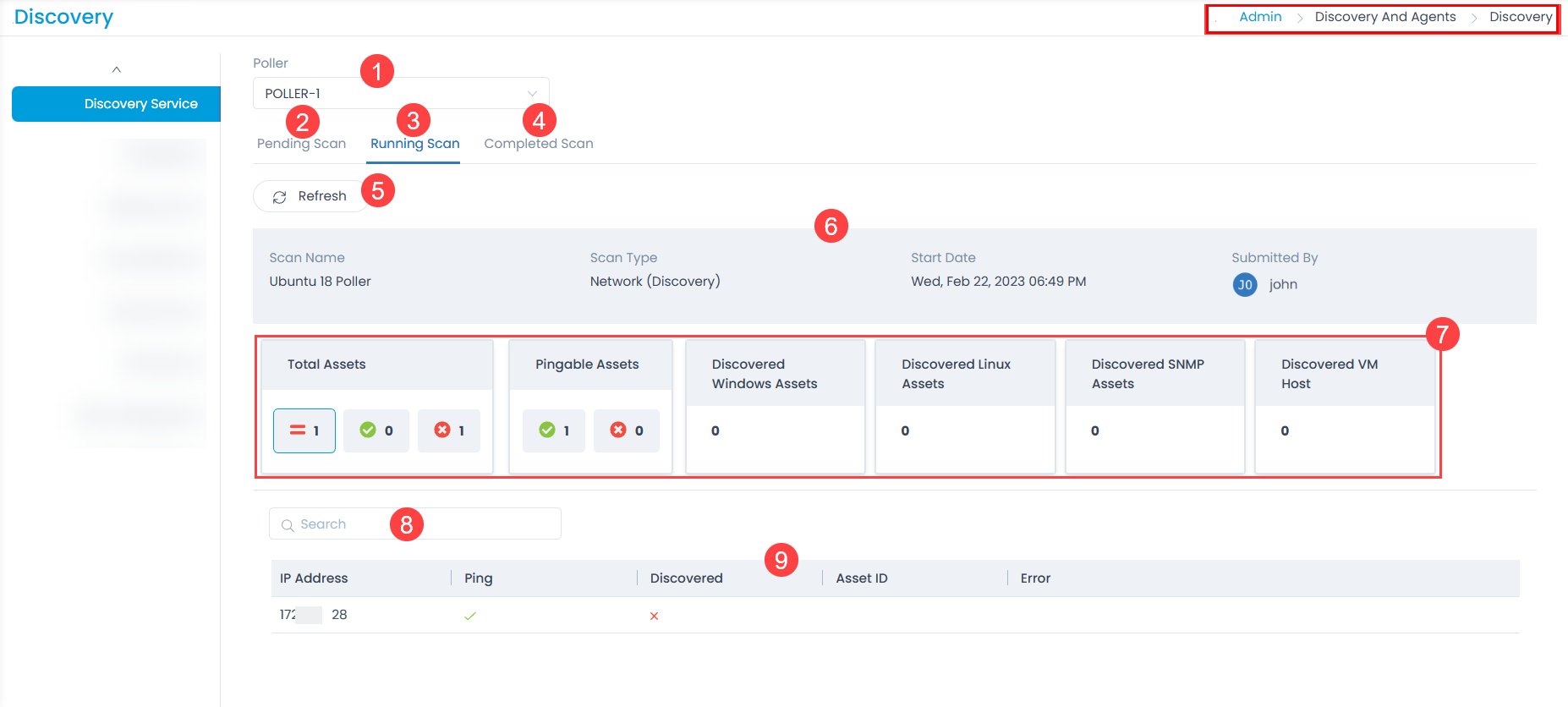
- Poller: Select the poller service for which you want to view the scan details.
- Pending Scan: Displays the pending scan. It is available only while performing scan based on a particular poller service.
- Running Scan: Displays the Ongoing Scan services, where the status gets updated as long as the scan keeps on running.
- Completed Scan: Displays the completed scan results with the number of assets that are discovered or not discovered.
- Refresh: You can refresh the page for continuous update of assets discovered.
- Scan Details: Displays the details of the scan which includes the network’s name, type of scan, Start date/time, and User.
- Discovery Details: Displays bifurcation of the assets such as Total Assets, Pingable assets, Discovered Assets, and Not Discovered assets.
- Search: You can search the required IP Address from a list of assets discovered.
- IP Address List: Displays a list of IP Addresses that are pingable and discovered along with their asset IDs.
Completed Scan
This tab displays the details of the scan that is completed.
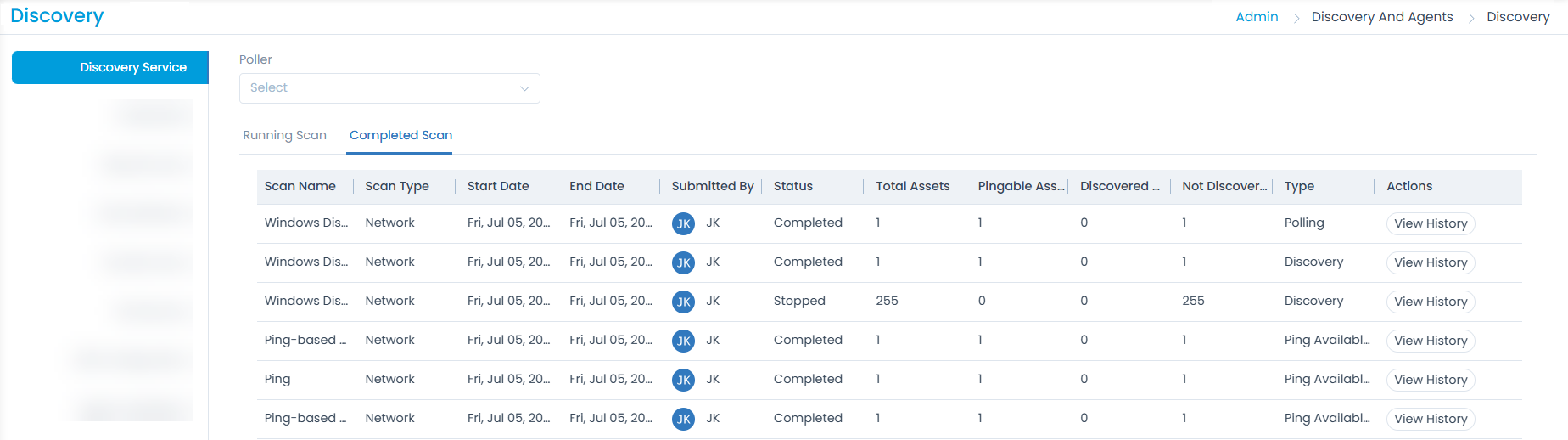
You can also view the history of the scan by clicking the View History button. The popup displays the Success and Failed count of the assets discovered by clicking on the count of the respective block. It displays the total assets, pingable, and not pingable assets, discovered Windows, Linux, SNMP, and VM Host assets respectively. Additionally, you can download the history details in Excel and PDF formats.
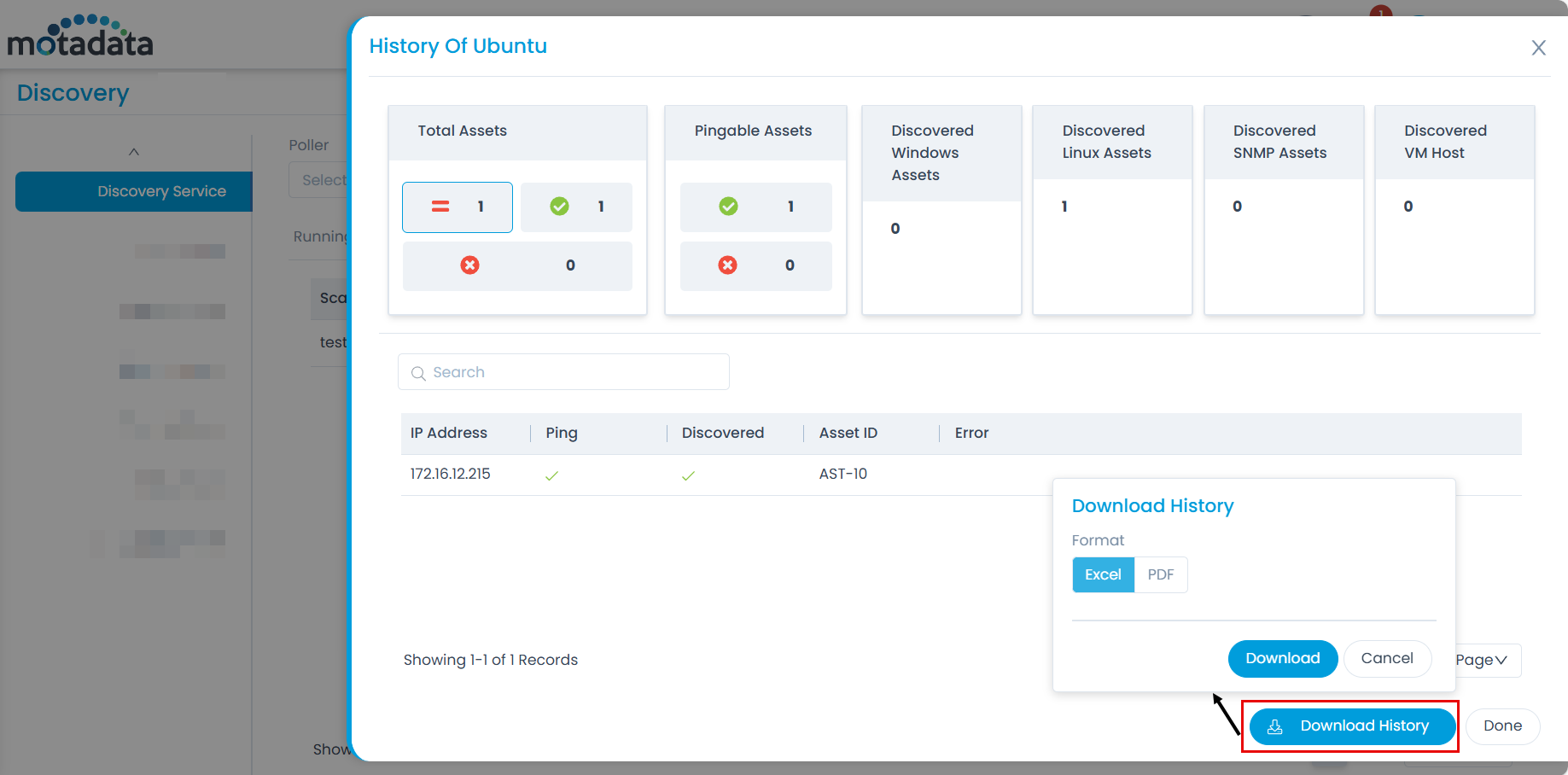
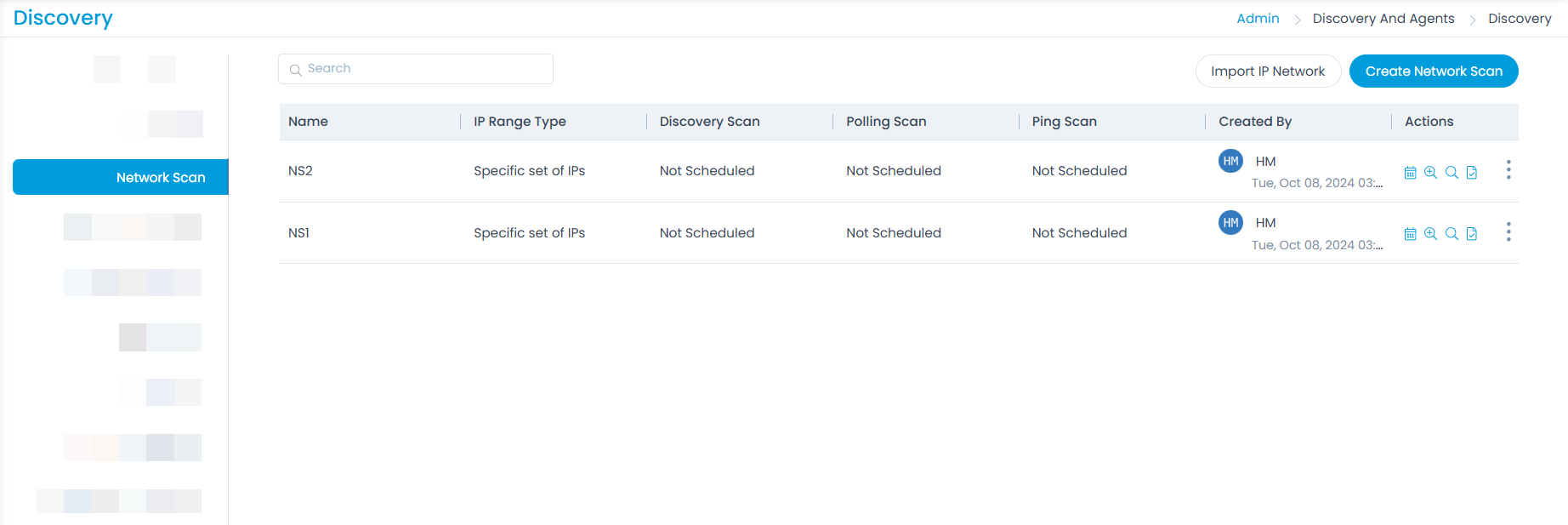
Network Scan
Network Scan allows scanning of the whole network specified along with the credentials, authentication, and successful connections.
Here, you can view, add, as well as import IP Networks. Also, you can create a schedule, discover a new asset, poll existing asset, add Asset in Stage, and add CI in Stage. To import IP Networks, follow the same steps as Import Credentials.
To create a Network Scan, Click the Create Network Scan button and a popup appears.

Enter the below details:
| Parameter | Description |
|---|---|
| Name | Enter the name of the network scan. |
| IP Range Type | Select the type of IP Range. The options are: - Entire Network: All the IPs in the whole network will be scanned for the discovery. If selected, enter the IP Range Start. - Specific IP Range: Select if assets from a specific IP Range are to be scanned. If selected, enter the IP Range Start and IP Range End for discovery. - Specific set of IPs: Select if you want to scan only specific IP Addresses for asset discovery. If selected, enter the IP Addresses. Also, you can import the IP addresses via a CSV file using the Import IP Addresses link. |
| Authentication Preference | Select the type of authentication to use to create a network scan. The options are: - Credential-Based: Select to perform discovery based on credentials. - Credential-Less: Select to perform discovery without credentials using the Nmap software. This is supported for Windows OS only. For more details, refer to the Credential-Less Authentication page. |
| Location | Select the location of the netwasset-discoork from the dropdown. |
| Department | Select the department. |
| Exclude IPs | Enter the list of IPs you want the network to skip while running the scan. You can also import the IP Addresses via a CSV file using the Import Exclude IPs link. |
| Protocol Type | Select the type of protocol for the network. The options are: Static and DHCP. If DHCP is selected, DNS configuration is required for Domain Scan. |
| Description | Enter the description of the network scan. |
| Credentials | Select the credentials of the machines that you want to discover. You can also create new credentials using the Create Credentials link. |
| Poller | Select the poller for which you want to create the network scan. |
Once all the details are filled, click Save. The created network will appear on the list page as shown below.
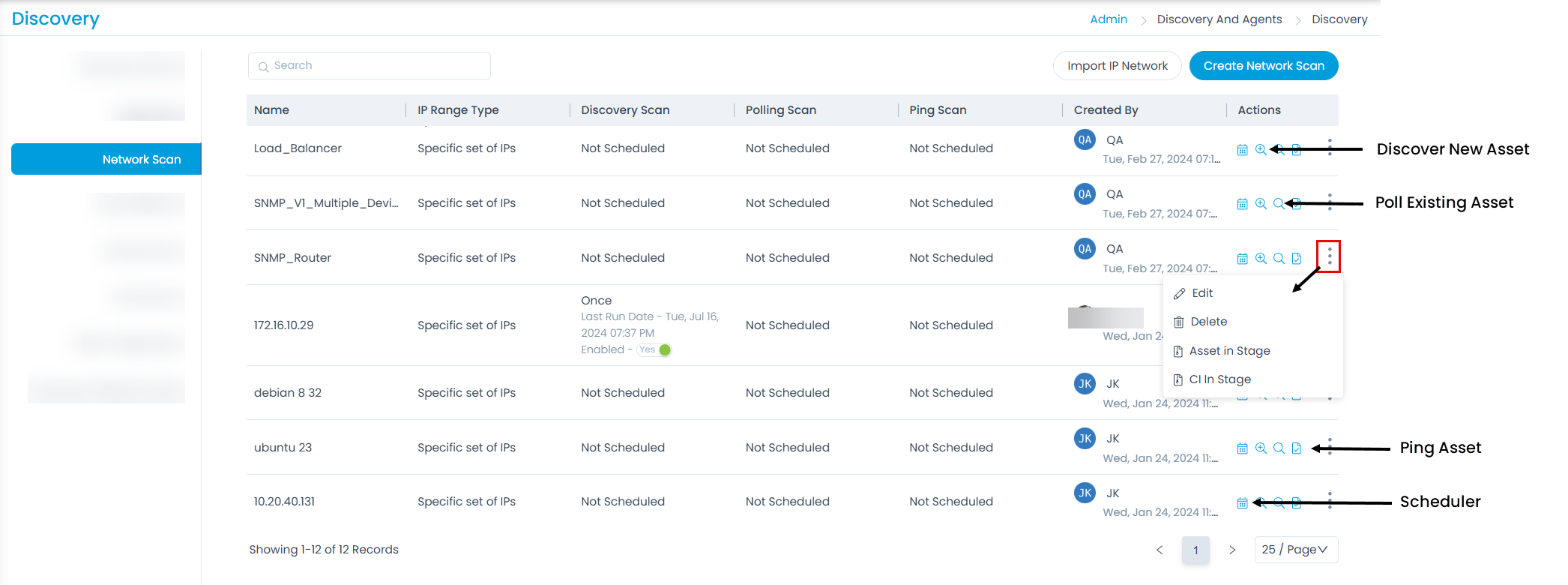
Here, you can do the following:
- Schedule the network scan
- Discover New Asset (Only if Credential is selected)
- Poll Existing Asset (Only if Credential is selected)
- Ping Asset (Credentials are not required)
- Edit the network scan.
- Delete the network scan if not required.
- You can add the Assets in Stage by selecting the option, the asset type, assets, and then clicking the Add to CMDB button.

- You can add CI in stage by selecting the option, the CI filter, CI, and then clicking the Add to CMDB button.

Schedule Network Scan, Polling, and Ping Scan
Scheduling the discovery scan helps to overcome the similar activity of adding assets every time when a new asset is added. For every created network, the Scheduler option is given besides the created network as shown in the above figure.
Select the Scheduler option and a popup appears. It displays the following three tabs:
- Discover Scan Schedule: Configure to automatically populate the inventory with assets and CIs.
- Polling Scan Schedule: Configure to regularly poll the assets and CI devices to monitor their status in real-time and update the details accordingly.
- Ping Schedule: Configure to check the status (active/inactive) and availability of assets and CIs.
In the Discover Scan Schedule, click Create Discovery Schedule button and the options appear.


Enter the below details:
- Schedule Type: Select the type of schedule. The options are:
- Once: The schedule will run only once on the selected start date.
- Daily: The schedule will run daily starting from the selected start date and time.
- Weekly: The schedule will run once a week as per the selected day and time. Also, provide the start date from which the schedule will be applicable.
- Monthly: The schedule will run once a month as per the selected date, time, and month. Also, provide the start date from which the schedule will be applicable.
- Interval: Set the interval in hours or days within which the schedule should run. Also, provide the start date from which the schedule will be applicable.
- Automatically add Assets in CMDB?: Select Yes if you want to add the discovered assets automatically in CMDB.
- Email: You can add the email id’s for notification email of network scan results after completion.
- Once done, click Save. Similarly, you can configure the polling scan schedule and ping schedule. Once the schedule is configured it will run as per the set time and its status will be visible on the Discovery Service tab. Once the scan is completed, you can view its details from the Completed Scan tab and View History.


Discover New Asset
Incase of addition of asset in a particular network, you can just click the Discover New Asset option, which will scan the network and discover newly added assets. You can also add the newly scanned assets automatically in CMDB if required or in stage.
This option is available for credential-based discovery only.
Poll Existing Asset
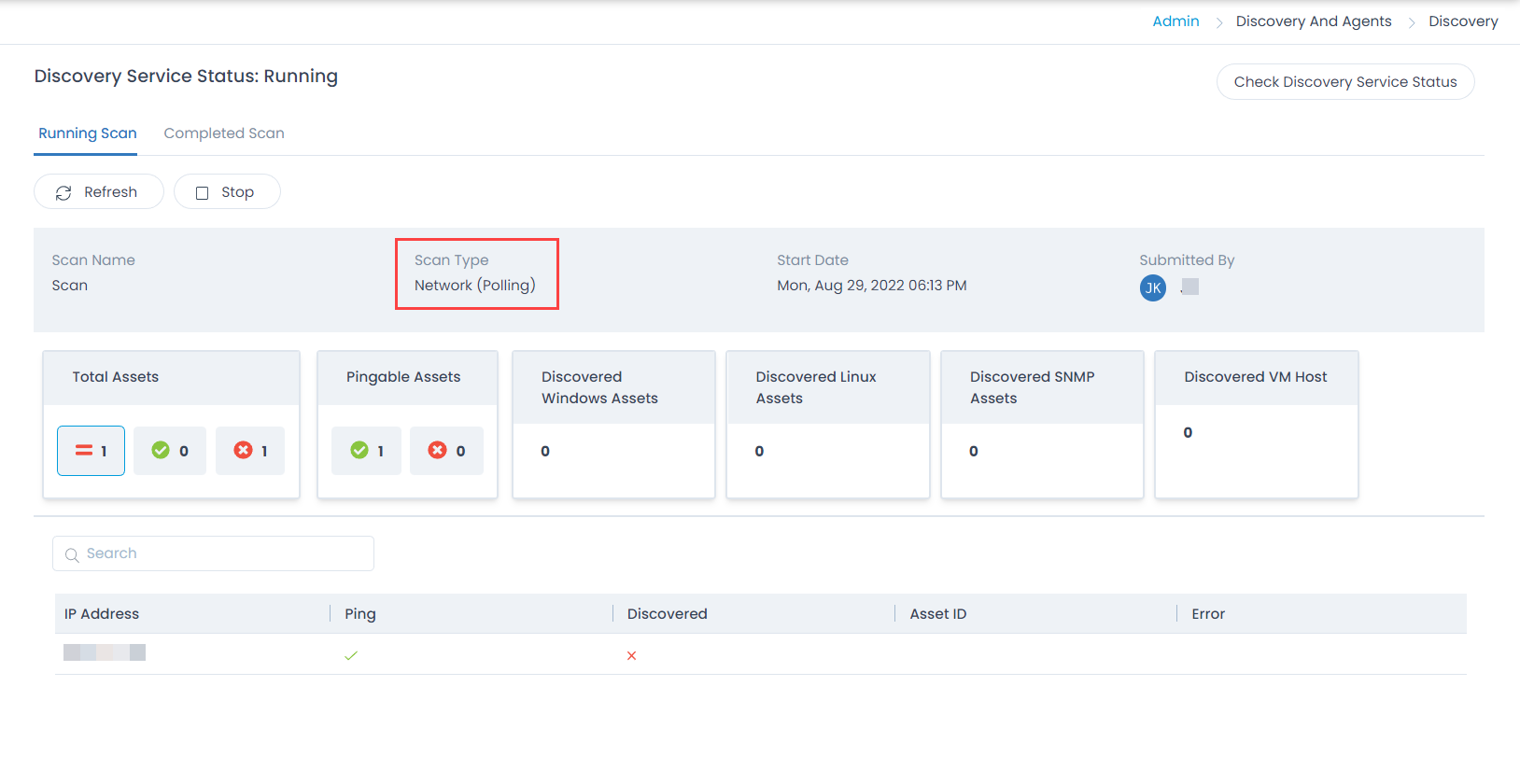
You can poll the existing assets in the network using the Poll Existing Asset option which will update the added information while discovering.
This option is available for credential-based discovery only.
When the polling completes, the discovery page will display the discovery through Polling as shown below:
Ping Asset
You can ping the asset manually using the 'Ping Asset' icon which will scan the network and identify the pingable assets. It does not need any credentials for scanning the network. Once clicked, the Network scan will begin in the Discovery Service tab as shown below.
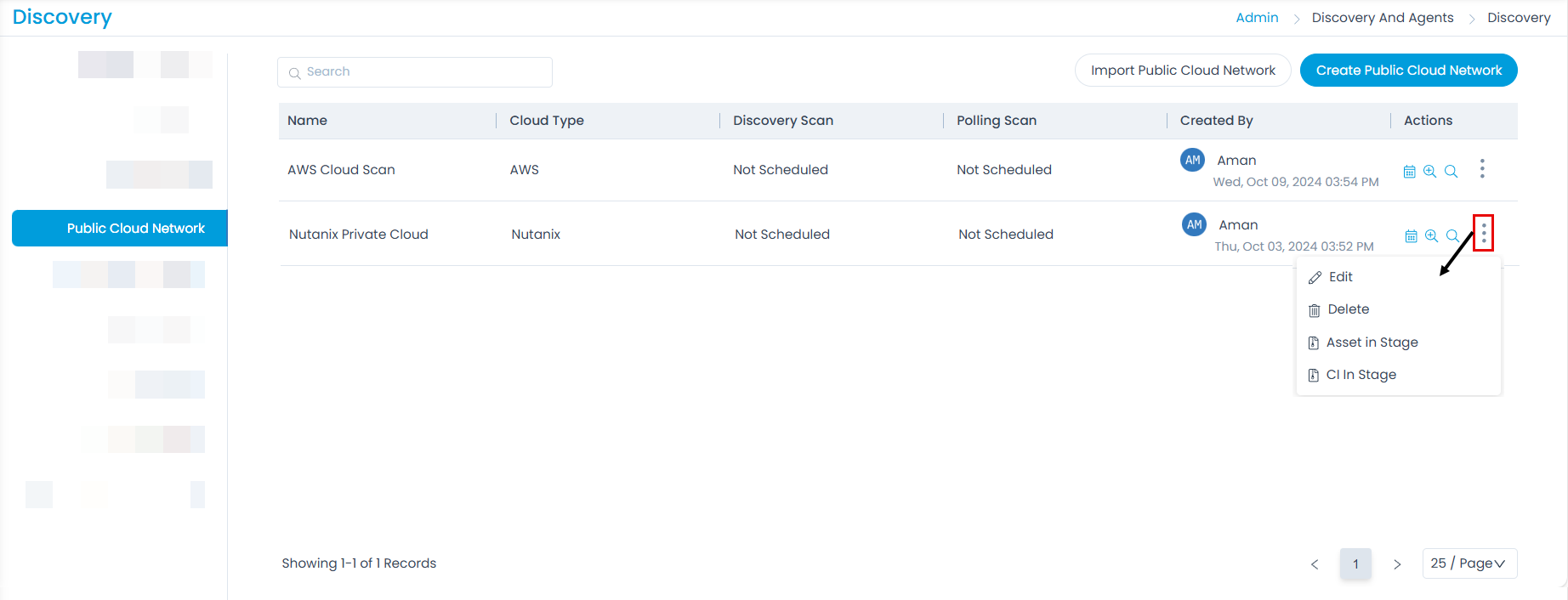
Public Cloud Network
This allows to import and create a network scan to discover the cloud assets. The configurations are similar to network scan.
Here, you can view, add, as well as import public cloud networks. Also, you can create a schedule, discover a new asset, poll existing asset, add Asset in Stage, and add CI in Stage. To import Cloud Networks, follow the same steps as Import Credentials.
To create a Public Cloud Network, click the Create Public Cloud Network button, and a popup appears.

Enter the below details:
| Parameter | Description |
|---|---|
| Name | Enter the name of the public cloud network scan. |
| Cloud Type | Select the type of cloud. The options are: - AWS - Azure |
| Description | Enter a brief description about the public cloud network scan. |
| Credentials | Select the credentials to be used from the dropdown. You can also create new credentials using the Create Credentials link. |
| Poller | Select the Poller to allow only specific devices to access the required cloud entities. |
| Proxy Server | Select the requried Proxy server when the Internet is needed to discover assets or CI in the Private and Public Cloud infrastructure. Note: The Proxy server configuration is not supported for Azure Cloud type in the Public Cloud Network. |
Once all the details are filled, click Save. The created network will appear on the list page. Here, you can do the following:
- Schedule the cloud network scan. For more details, refer to the section Network Scan.
- Discover New Asset. For more details, refer to the section Network Scan.
- Poll Existing Asset. For more details, refer to the section Network Scan.
- Edit the cloud network scan.
- Delete the cloud network scan if not required.
- You can add the Assets in Stage to CMDB by selecting the option, the asset type, assets and then clicking the Add to CMDB button. For more details, refer to the section Network Scan.
- You can add the CIs in Stage to CMDB by selecting the option, the CI filter, CIs and then clicking the Add to CMDB button. For more details, refer to the section Network Scan.
Private Cloud Network
A private cloud network is a cloud computing environment that is dedicated to a single organization. Unlike public cloud services, which are shared among multiple users, a private cloud offers exclusive access to cloud resources (such as storage, computing power, and networking) that are hosted either on-premises or in a third-party data center. The key features of a private cloud include enhanced control, customization, and security, making it ideal for organizations with strict data privacy, compliance, or performance requirements.
In a private cloud, the organization can tailor the infrastructure to its specific needs, manage workloads more efficiently, and control access to its data. It often provides the flexibility and scalability of cloud computing while maintaining a higher level of security and governance than a public cloud environment. Examples of private cloud platforms include Nutanix servers.
Key Characteristics:
- Exclusive Access: Only one organization uses the private cloud environment.
- Enhanced Security: Provides higher control over security and compliance as resources are not shared with other users.
- Customization: Organizations can customize the environment to suit their specific needs.
- Scalability: Resources can be scaled up or down based on organizational demand, similar to public cloud environments but with more control.
Benefits:
- Improved security and privacy.
- Greater control over the infrastructure.
- Better performance for mission-critical applications.
This tab allows to import and create a network scan to discover the private cloud assets. The configurations are similar to network scan.
Here, you can view, add, as well as import private cloud networks. Also, you can create a schedule, discover a new asset, poll existing asset, add Asset in Stage, and add CI in Stage. To import Cloud Networks, follow the same steps as Import Credentials.
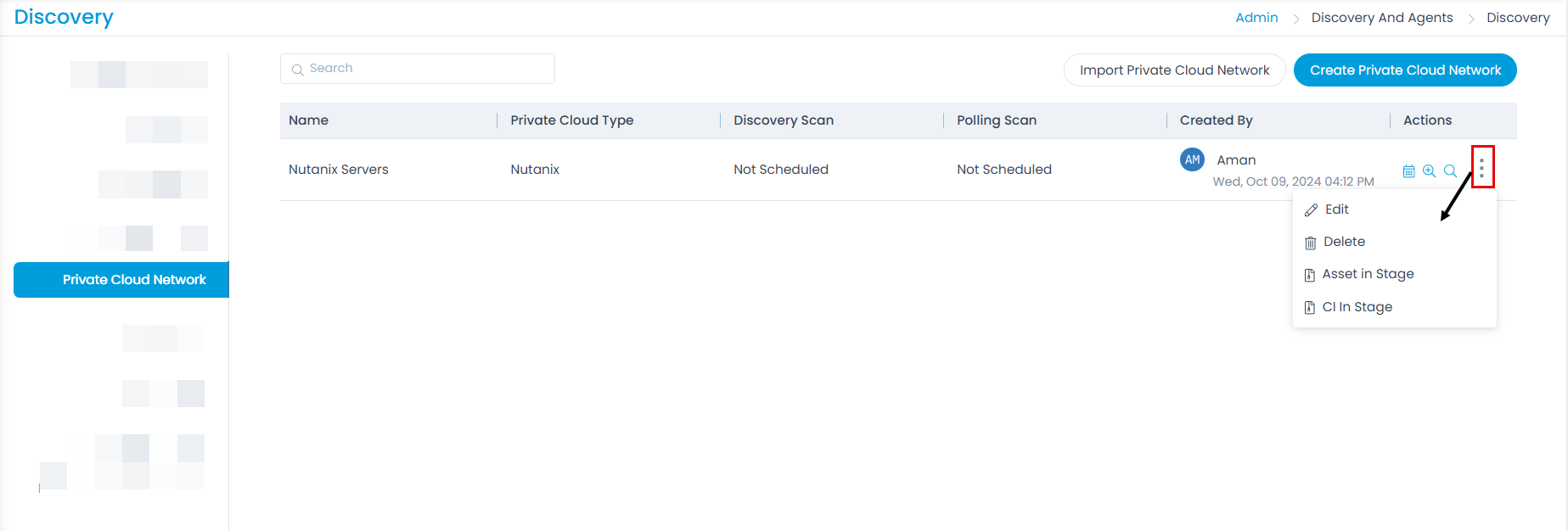
To create a Private Cloud Network, click the Create Private Cloud Network button, and a popup appears.

Enter the below details:
| Parameter | Description |
|---|---|
| Name | Enter the name of the public cloud network scan. |
| Connection Timeout | Enter the time after which the connection should be closed. |
| Location | Select the location of the private cloud network. |
| Department | Select the department of the private cloud network. |
| IP Addresses | Enter the IP Addresses manually which you want to scan. You can also import the credentials using the Import IP Addresses link. |
| Description | Enter a brief description about the scan. |
| Credentials | Select the credentials to be used from the dropdown. You can also create new credentials using the Create Credentials link. |
| Poller | Select the Poller service from the dropdown list. |
| Proxy Server | Select the requried Proxy server when the Internet is needed to discover assets or CI in the Private Cloud infrastructure. |
Once all the details are filled, click Save. The created network will appear on the list page. Here, you can do the following:
- Schedule the cloud network scan. For more details, refer to the section Network Scan.
- Discover New Asset. For more details, refer to the section Network Scan.
- Poll Existing Asset. For more details, refer to the section Network Scan.
- Edit the cloud network scan.
- Delete the cloud network scan if not required.
- You can add the Assets in Stage to CMDB by selecting the option, the asset type, assets and then clicking the Add to CMDB button. For more details, refer to the section Network Scan.
- You can add the CIs in Stage to CMDB by selecting the option, the CI filter, CIs and then clicking the Add to CMDB button. For more details, refer to the section Network Scan.
Domain Scan
Discovery can be done via scanning. Apart from network scan, you can perform the discovery via domain scan too.
DNS configuration is required for Domain Scan.
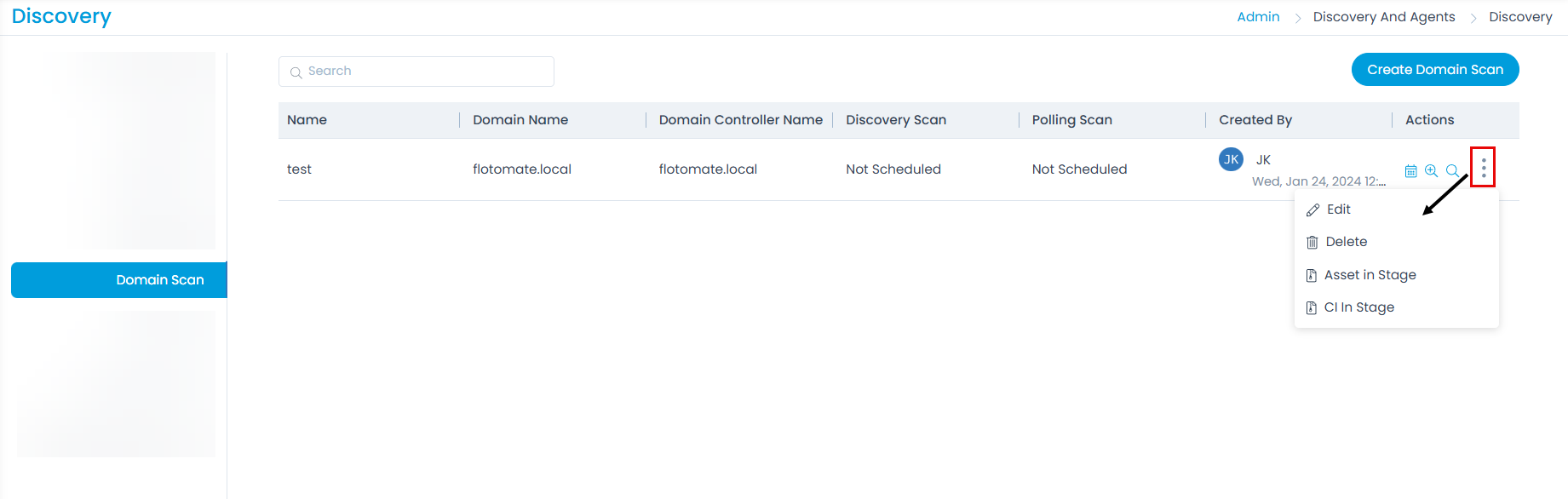
The list page displays the Name and Domain Name details. Also it displays the created date, time, and name of the creator.
To create a new domain Scan, click Create Domain Scan on the top-right corner of the page, and a popup appears.
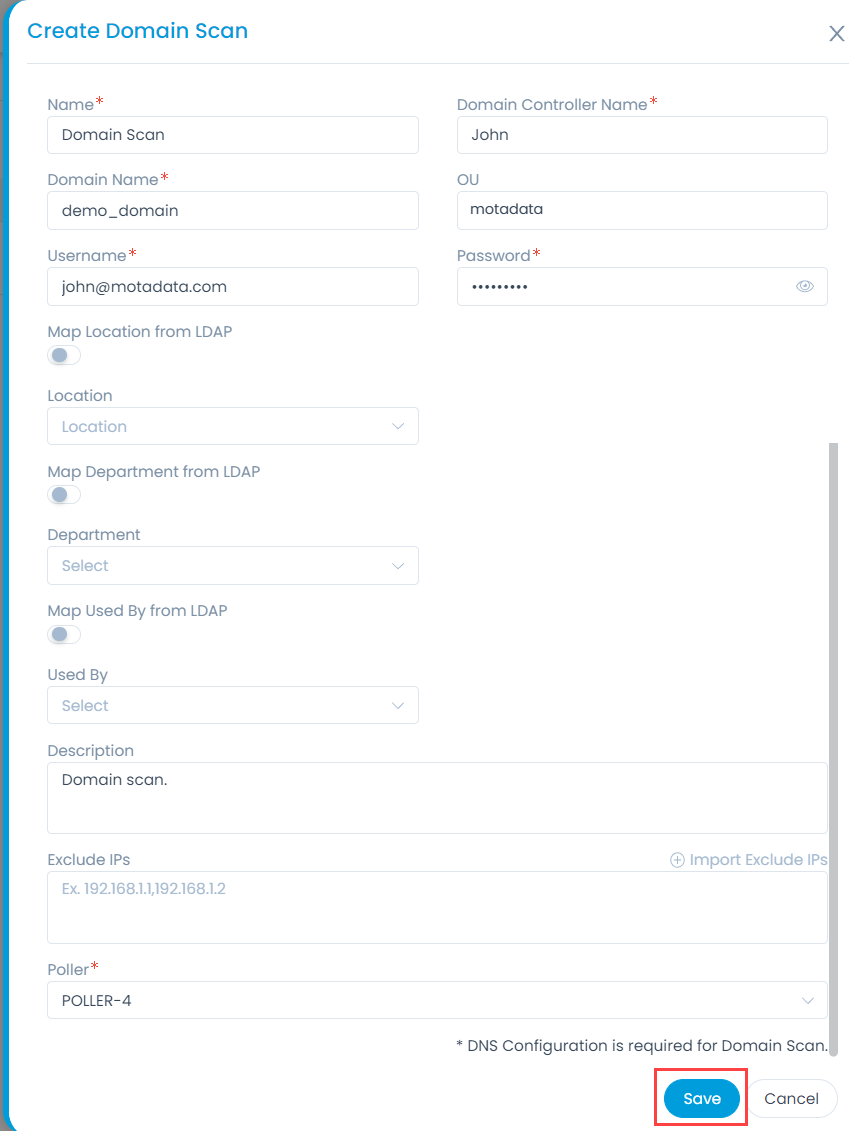
Enter the below details:
| Parameter | Description |
|---|---|
| Name | Enter the name of the domain scan. |
| Domain Controller Name | Enter the name of the controller of the organization’s domain. |
| Domain Name | Enter the domain name of the organization. For example: Acne.com |
| OU | Enter the Organizational Unit name of the domain. For example: OU=motadata |
| Username | Enter the username. |
| Password | Enter the password for successful domain connection. |
| Map Location from LDAP | Enable if you want to map the location of the domain from the LDAP server. If enabled, specify the LDAP Location Field. If the entered location is not present you can also create it by enabling the Create Location option. |
| Location | Select the location of the domain from the dropdown. |
| Map Department from LDAP | Enable if you want to map the department of the domain from the LDAP server. If enabled, specify the LDAP Department Field. If the entered Department is not present you can also create it by enabling the Create Department option. |
| Department | Select the department belonging to the domain. |
| Map Used By from LDAP | Enable if you want to map the user of the domain from the LDAP server. If enabled, specify the LDAP Used By Field. If the entered user is not present you can also create it by enabling the Create Used By option. |
| Used By | Select the user from the dropdown. |
| Description | Enter a brief description about the domain scan. |
| Exclude IPs | Enter the list of IPs you want the network to skip while running the scan. |
| Poller | Select the poller for which you want to create the domain scan. |
Once all the details are filled, click Save. The created domain scan will appear on the list page. You can also click the Test Connection button to check if its successful and authenticating.
The Test Connection button is unavailable in the SaaS application.
On the list page, you can do the following:
- Schedule the domain scan. For more details, refer to the section Network Scan.
- Discover New Asset. For more details, refer to the section Network Scan.
- Poll Existing Asset. For more details, refer to the section Network Scan.
- Edit the domain scan.
- Delete the domain scan if not required.
- You can add the Assets in Stage to CMDB by selecting the option, the asset type, assets, and then clicking the Add to CMDB button. For more details, refer to the section Network Scan.
- You can add the CIs in Stage to CMDB by selecting the option, the CI filter, CIs, and then clicking the Add to CMDB button. For more details, refer to the section Network Scan.
SCCM Scan
Motadata uses Microsoft System Centre Configuration Manager (SCCM) to manage desktops and Windows-based applications where you can integrate with SCCM and fetch the SCCM-scanned asset data. The integration leverages SCCM’s scan capabilities users to avoid installing two agents to fetch asset details. You can also use SCCM for asset discovery and also simultaneously update the asset data.
The assets fetched from the the SCCM database will have the source as SCCM and resource id generated by the SCCM server.

The list page displays the Name, Authentication Type, and Host Name details. Also it displays the created date, time, and name of the creator.
To create a new SCCM Scan, click Create SCCM Scan on the top-right corner of the page, and a popup appears.

Enter the below details:
| Parameter | Description |
|---|---|
| Name | Enter the name of the SCCM scan. |
| Authentication Type | Select the type of authentication. The options are: - SQL Server Authentication - Windows Authentication |
| Username | Enter the username. |
| Password | Enter the password for successful domain connection. |
| Database Name | Enter the name of the database that you want to scan. |
| Port | Enter the port number. |
| Host Name | Enter the host name for connection. |
| Domain Name | Enter the domain name of the organization. It is mandatory for Windows type of Authentication. |
| Description | Enter a brief description about the SCCM scan. |
| Location | Select the location of the SCCM from the dropdown. |
| Department | Select the department belonging to the SCCM. |
| Poller | Select the poller for which you want to create the SCCM scan. |
Once all the details are filled, click Save. The created SCCM scan will appear on the list page. You can also click the Test Connection button to check if its successful and authenticating.
The Test Connection button is unavailable in the SaaS application.
On the list page, you can do the following:
- Schedule the SCCM scan. For more details, refer to the section Network Scan.
- Discover New Asset. For more details, refer to the section Network Scan.
- Poll Existing Asset. For more details, refer to the section Network Scan.
- Edit the SCCM scan.
- Delete the SCCM scan if not required.
- You can add the Assets in Stage to CMDB by selecting the option, the asset type, assets and then clicking the Add to CMDB button. For more details, refer to the section Network Scan.
- You can add the CIs in Stage to CMDB by selecting the option, the CI filter, CIs, and then clicking the Add to CMDB button. For more details, refer to the section Network Scan.
ChromeOS Scan
Similar to Network Scan, this tab allows to scan and discover ChromeOS devices. Based on the Discovery Preference, the ChromeOS device will be added as an Asset or CI to the system.
Here, you can create and manage the ChromeOS Scan.
To create,
- Click the Create ChromeOS Scan button and the following pop-up appears.
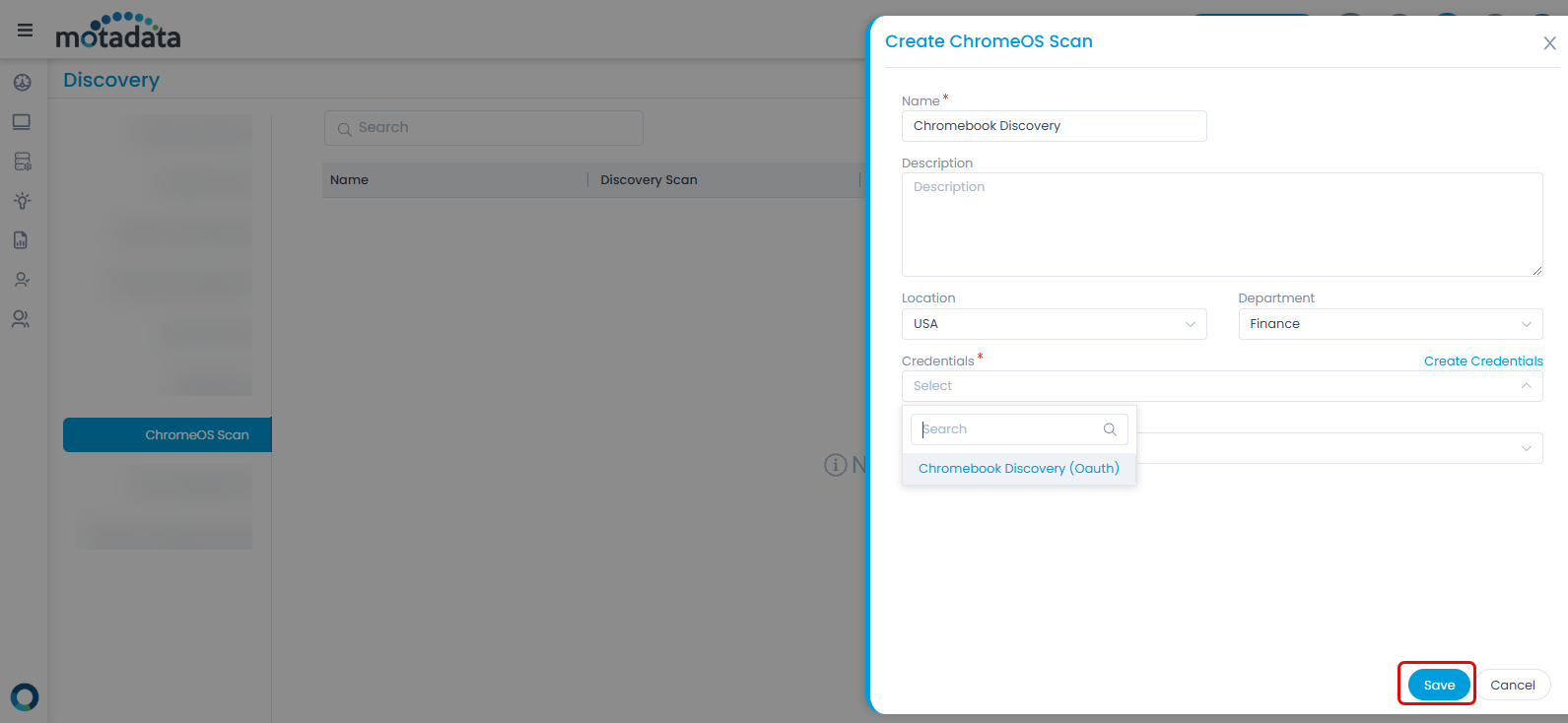
- Enter the below details:
- Name: Name of the ChromeOS Scan.
- Description: Enter a brief description about the scan.
- Location: Select the location of the scan.
- Department: Select the department.
- Credentials: Select the OAuth credentials created to discover the ChromeOS devices.
- Poller: Select the poller to perform discovery using poller.
- Once done, click Save. The newly created scan will appear on the list page as shown below.

You, can now create a scheduler to perform discovery at the scheduled time, manual discovery, and poll the existing chrome device.
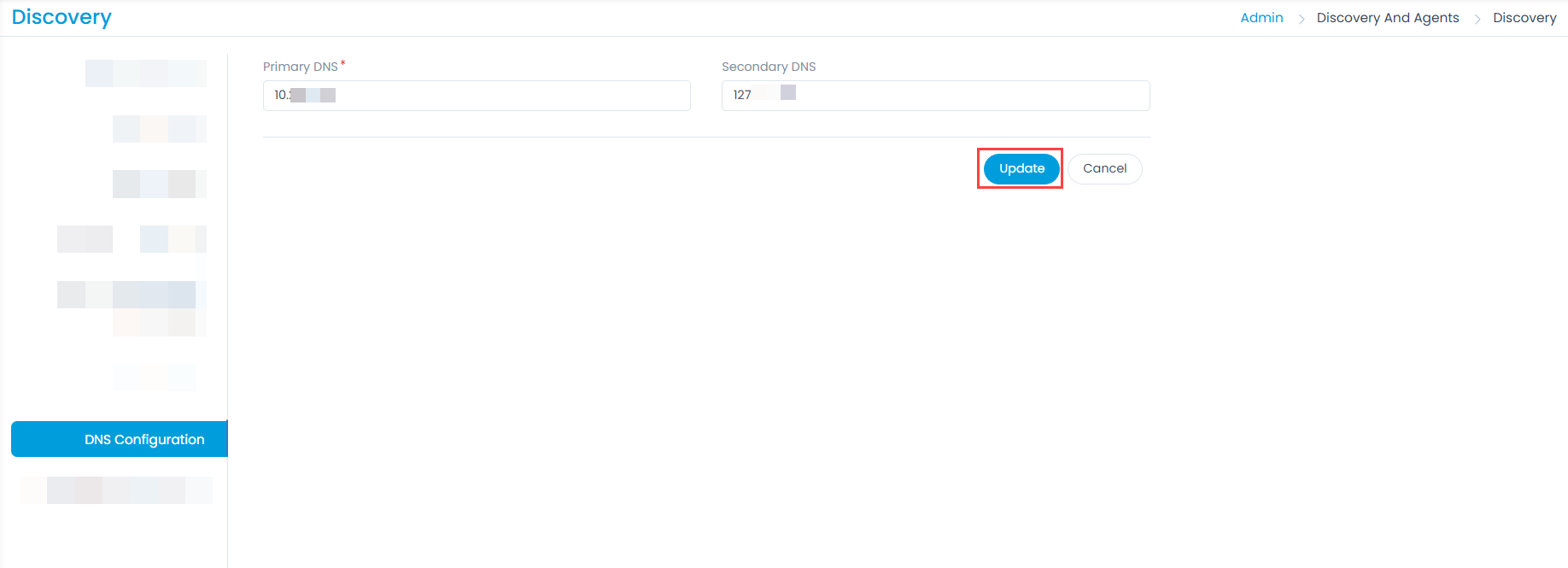
DNS Configuration
You can configure the DNS server of the application network by adding the Primary and Secondary DNS.
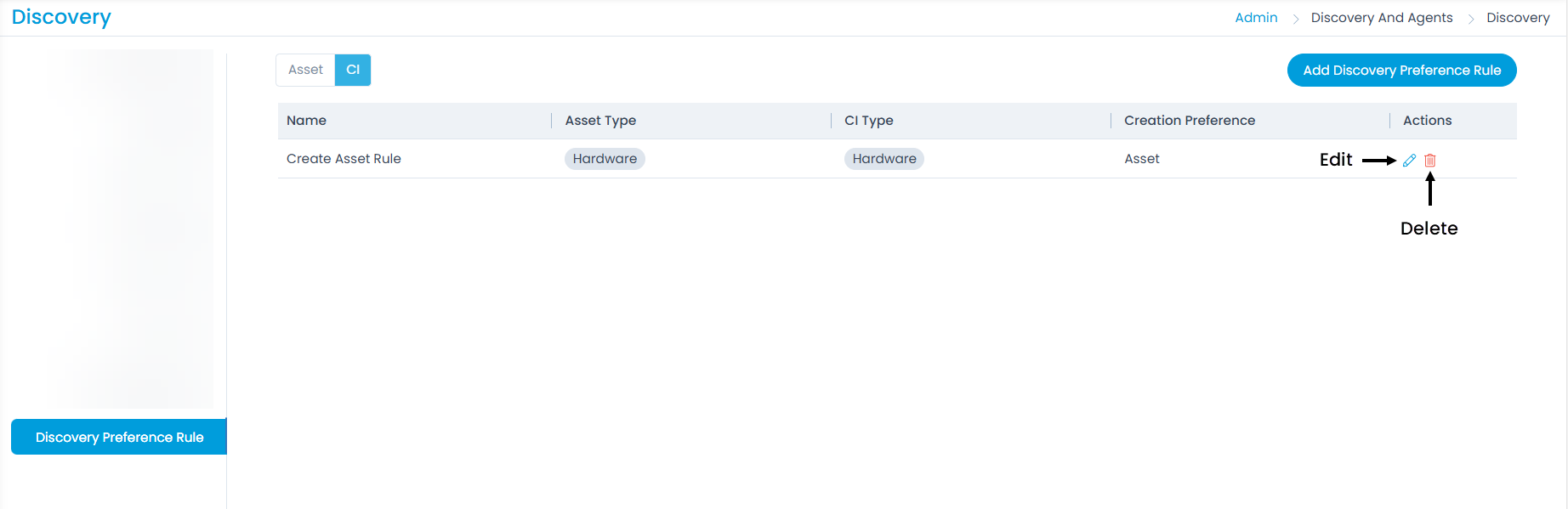
Discovery Preference Rule
This enables to create rules based on which the asset or CI will be created at the time of discovery. Here, you can set the global (default) discovery preference and also create rules to override it.
To view the Discovery Preference Rule, navigate to Admin > Discovery and Agents > Discovery > Discovery Preference Rule tab.
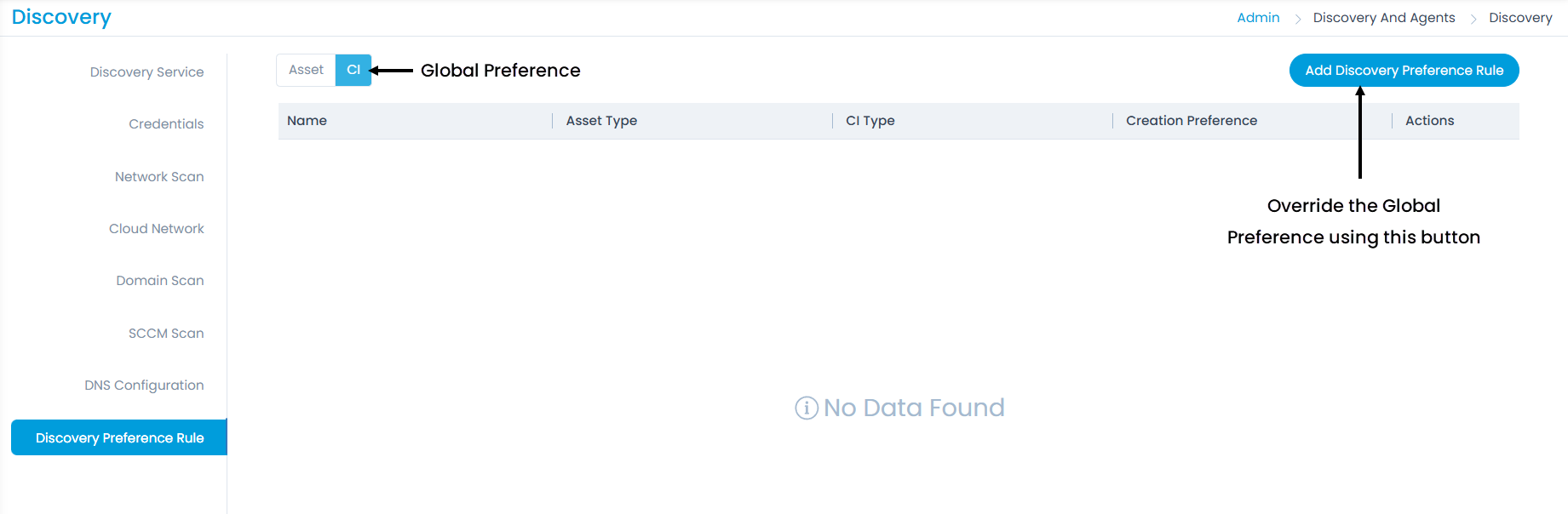
Here, you have two options:
- Set the global preference: You can set the default or global preference as Asset or CI. Based on the selection whenever an item is discovered it will be either created as CI or Asset.
- Override the global preference: If you prefer not to modify the global preference but want to override it, you can create a separate rule by using the 'Add Discovery Preference Rule' button located at the top-right corner of the section. For example, the global preference is set as CI and you want to override it. You can create a rule that will create an Asset on discovery.
To add a Discovery Preference Rule,
- Click the Add Discovery Preference Rule button and the following popup appears.

- Enter the following details:
- Name: Enter the rule name.
- Asset Type: Select the asset type that is to be considered for creating asset or CI.
- CI Type: Select the CI type that is to be considered for creating asset or CI.
- Creation Preference: Select the option from Asset or CI that you want to create on discovery based on the selected Asset and CI type.
- Once done, click Add. The rule will appear on the list page. You can now edit or delete it if required.