Active Directory Self Service
Active Directory Self Service allows users to manage certain AD account-related tasks without administrator intervention. Some common self service functionalities include:
- Unlocking a locked account
- Resetting password
This reduces the IT support dependency and improve productivity.
Why is LDAPS Required for Self Service?
For self service password resets and account unlocks, the self service tool must communicate with Active Directory to modify user account details. This communication occurs over LDAPS (Lightweight Directory Access Protocol Secure), which ensures that directory information is accessed and updated securely.
LDAPS (LDAP over SSL/TLS) is essential for,
- Encrypting communication between the AD server and LDAP clients
- Preventing eavesdropping and man-in-the-middle attacks
- Ensuring secure authentication and data transfer when modifying AD accounts
How Does LDAPS Secure Communication?
LDAPS secures data transmission by leveraging SSL/TLS encryption with a certificate installed on the Active Directory server. The process works as follows:
- The LDAPS client sends a request to secure connection over port 636.
- The ServiceOps server verifies the certificate to ensure it is from a trusted source.
- Once validated, an encrypted session is established for secure data exchange.
- The user sends the authentication details.
- The AD server validates the credentials and process the requests like password reset and unlock account.
Thus using LDAPS, all sensitive information — such as passwords and account modifications — remains fully protected from security threats.
- Install SSL/TLS certificates on the AD server.
- LDAPS must be configured on both primary and backup servers in high-availability setups.
Configuring LDAPS Certificate
To configure LDAPS, follow the below procedure:
Login to the terminal server and create a folder named "Backup" using the below command.
mkdir backup
Move to the Backup folder using the below command:
cd backup
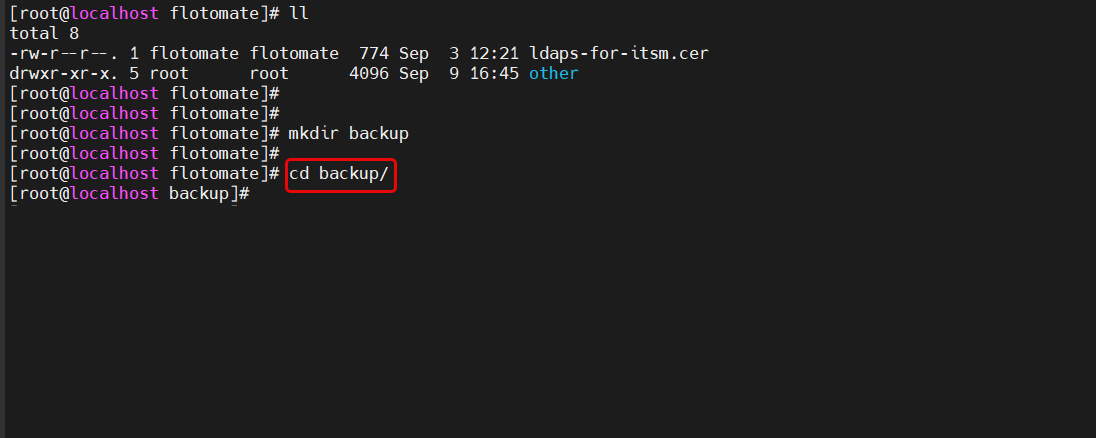
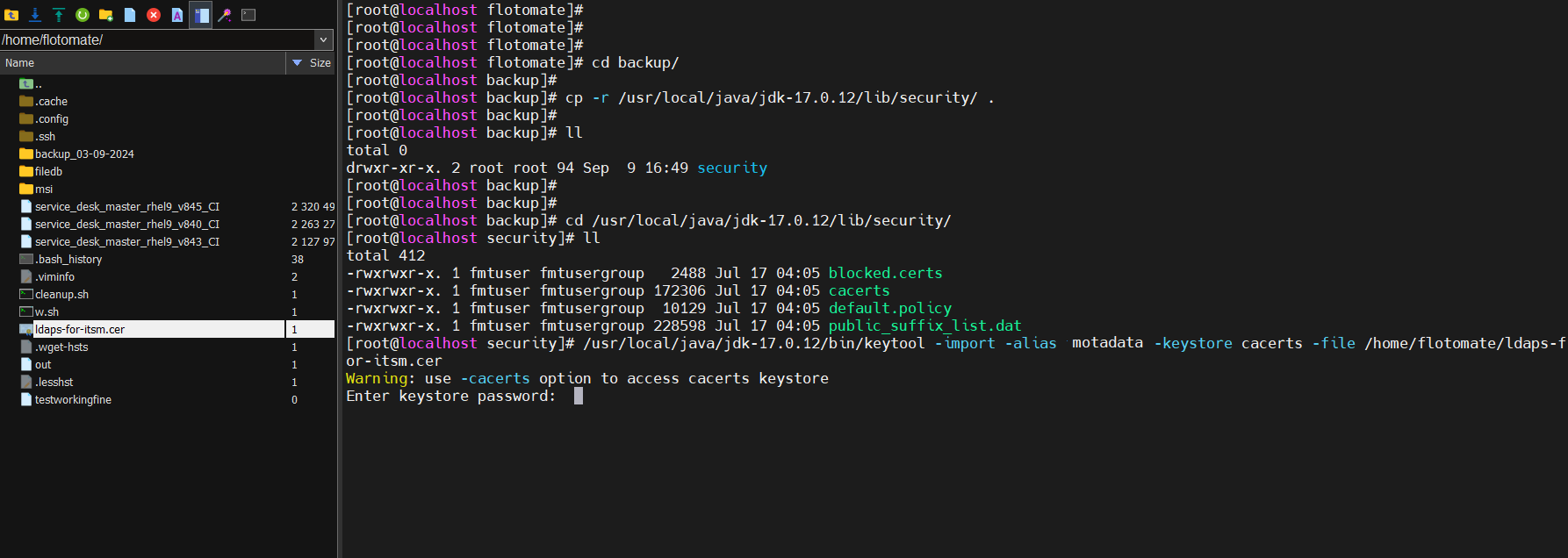
Navigate to the Java security directory where
cacertsis located:cd /usr/local/java/jdk-17.0.12/lib/security/Copy the "cacerts" file to the "backup" folder you created earlier:
cp cacerts /home/flotomate/backup/
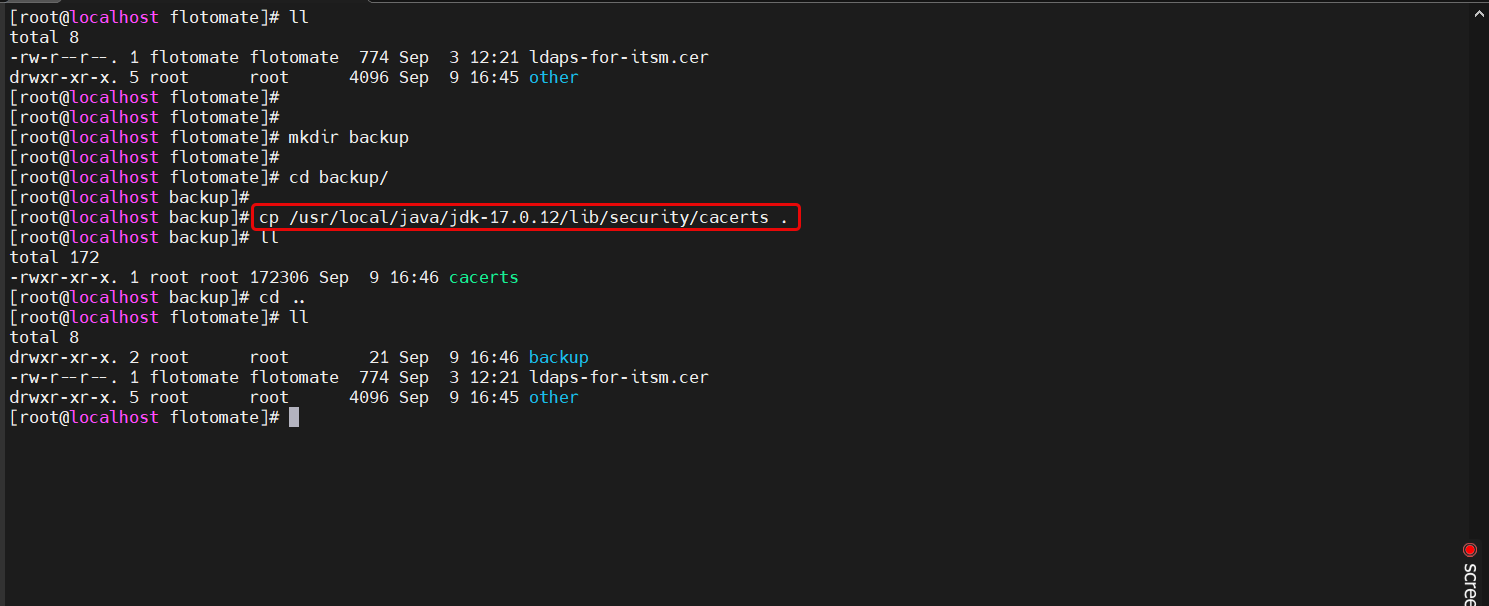
After copying the file, run the below command:
Syntax: /usr/local/java/jdk-17.0.12/bin/keytool -import -alias {alias_example} -keystore cacerts -file /{filepath}"
Example: /usr/local/java/jdk-17.0.12/bin/keytool -import -alias motadata -keystore cacerts -file /home/flotomate/ldaps-for-itsm.cer
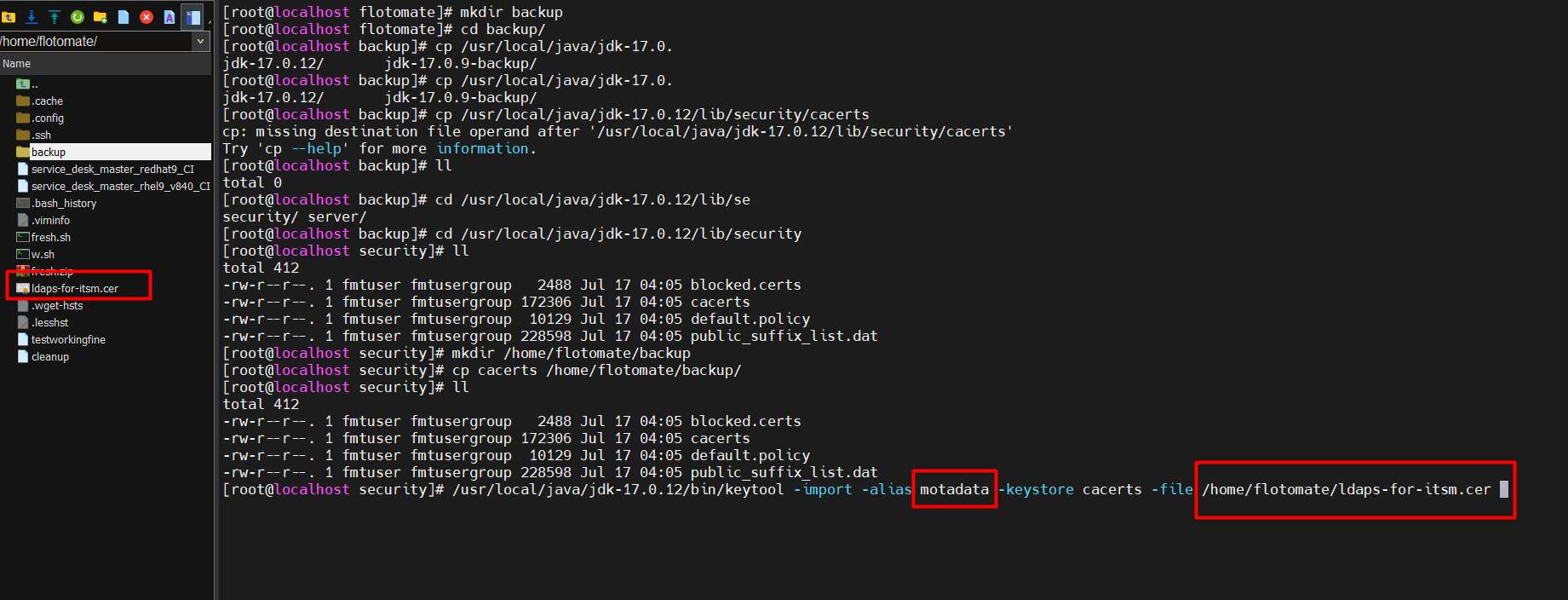
Save the alias name for future use.
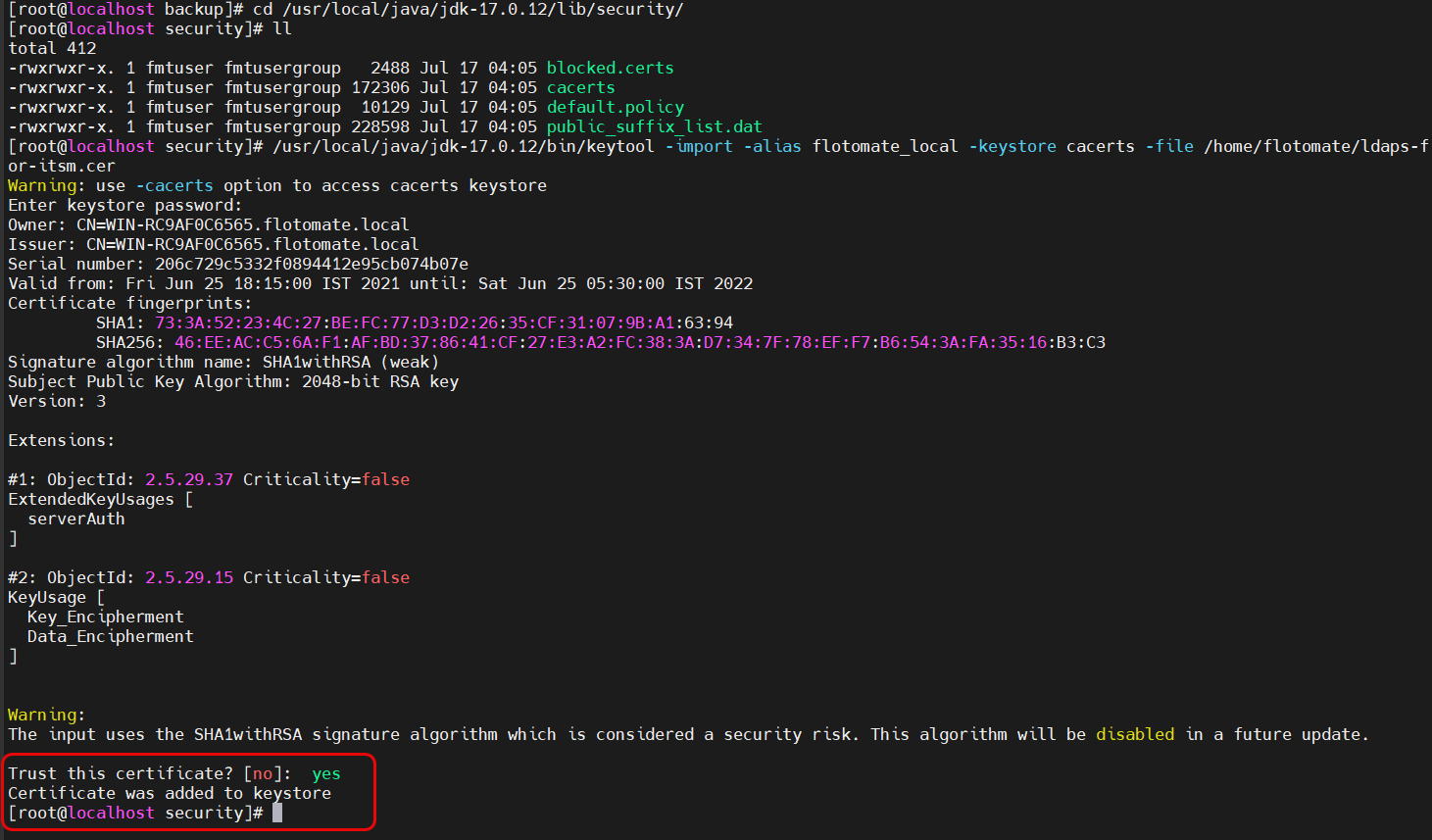
- Press enter and provide the keystore certificate password. For example, here "changeit" is used.
- A confirmation message "Trust this certificate?" will appear. Type Yes.
Restart the main-server and analytics-server services using the below commands:
sudo systemctl restart ft-main-server.service
sudo systemctl restart ft-analytics-server.serviceNow, change the LDAP configuration to LDAPS and port 636.

- Test the connection. Once successful, try to reset the password and it will work.
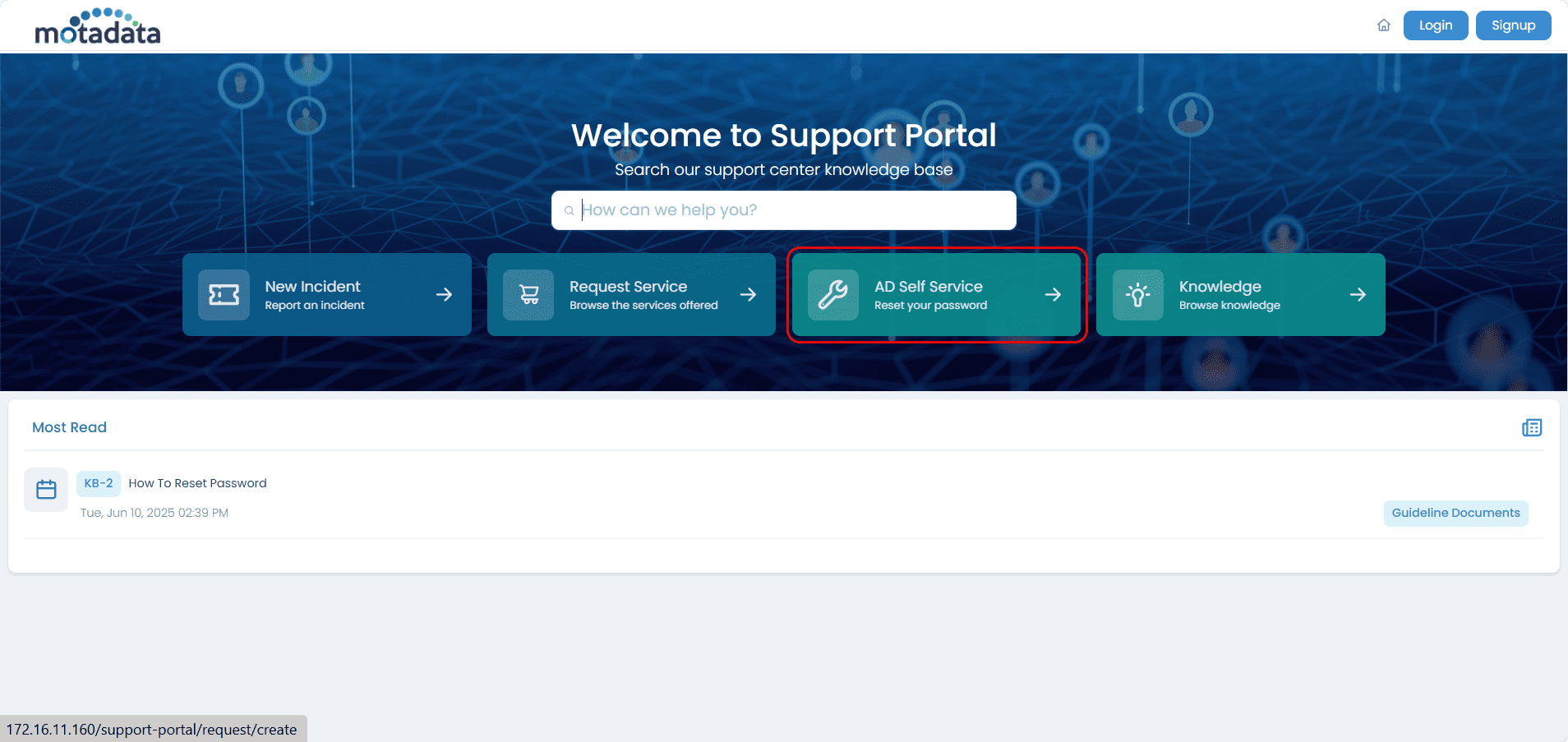

Enter the Email ID or Logon Name and click on Reset Password or Unlock Account whichever is feasible.
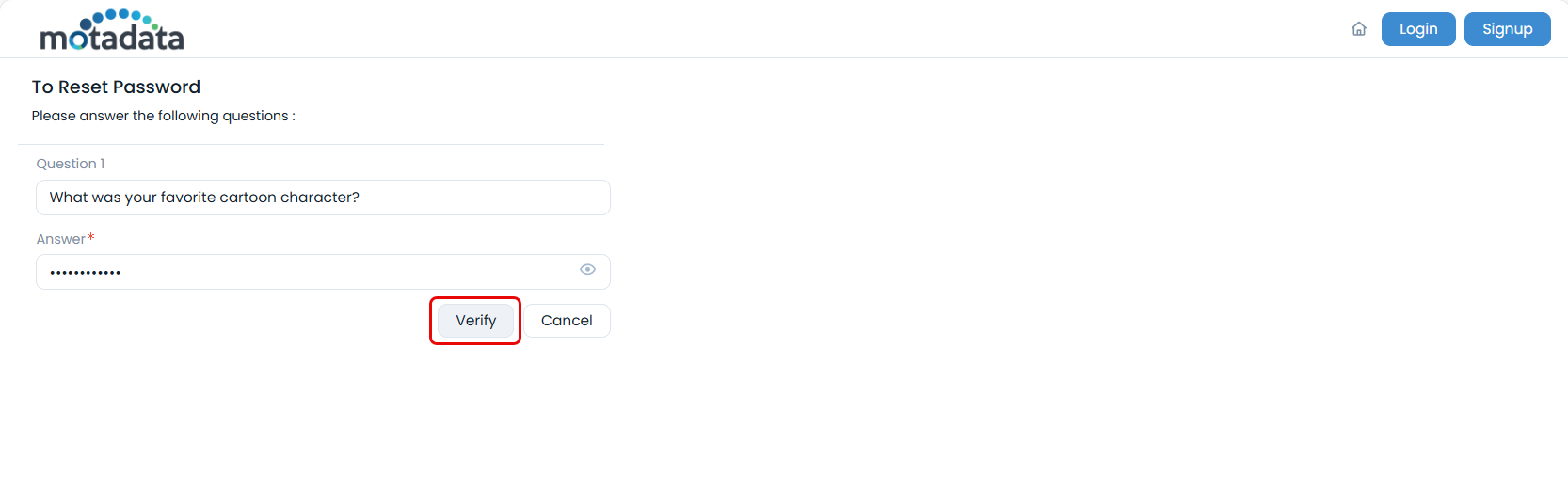
On clicking, answer and verify the security questions asked as shown below. The Security Questions configured in the Edit User Profile will be used here for Reset Password and Unlock Account.
Once all the questions are verified, Reset the Password by entering the new Password and Confirm Password as shown below.
Once done, click Submit, and the password will get changed. Also, it will get updated in the LDAP server. You can now login to the Support Portal using the new password.
Similarly, following the same process you can unlock your account if it gets locked somehow.