Configuring SSL for HA Proxy, Nginx, and MeshCentral Servers
Overview
Configuring SSL for HAProxy, MeshCentral, and Nginx servers is crucial for securing communications by encrypting data between clients and your web services. SSL enhances security, protecting sensitive information such as login credentials and personal data during transmission. This guide will take you through the process of setting up SSL certificates and configuring each of these servers: HAProxy as a load balancer, MeshCentral for remote management, and Nginx as a web server. By the end, you will have SSL-enabled services that ensure secure access and protect your network from potential vulnerabilities.
Prerequisites
- Valid SSL Certificate and Key files
- HTTPS 443 port must be accessible
HA Proxy Server
To configure SSL in the HA Proxy server,
Create a .pem file from the cert and key files using the below command.
cat example.crt example.key >> example.pemPlease check the below standard (default) configuration on HTTP port 80.
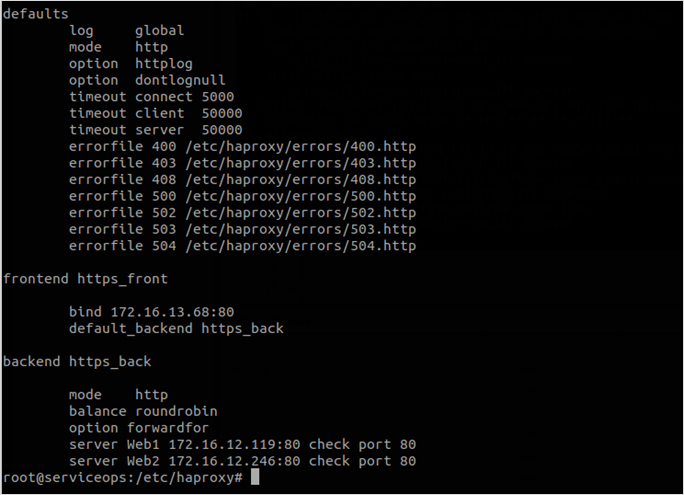
To change the HTTP port 80 configuration to HTTPS port 443, use the below command:
Syntax:
bind <server_ip_address>:443 ssl crt /etc/ssl/<file_name>.pemExample:
bind 172.16.13.68:443 ssl crt /etc/ssl/example.pem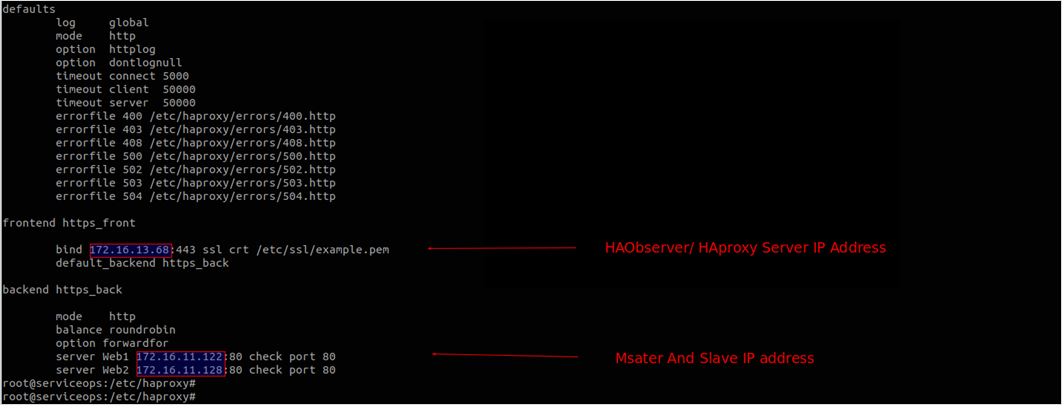
Verify the HA Proxy configuration using the below command:
haproxy –c –f /etc/haproxy/haproxy.cfg-2941fe92bed387b472a9368ccf449aed.png)
If the configuration file is valid, restart the HA Proxy server service using the below command:
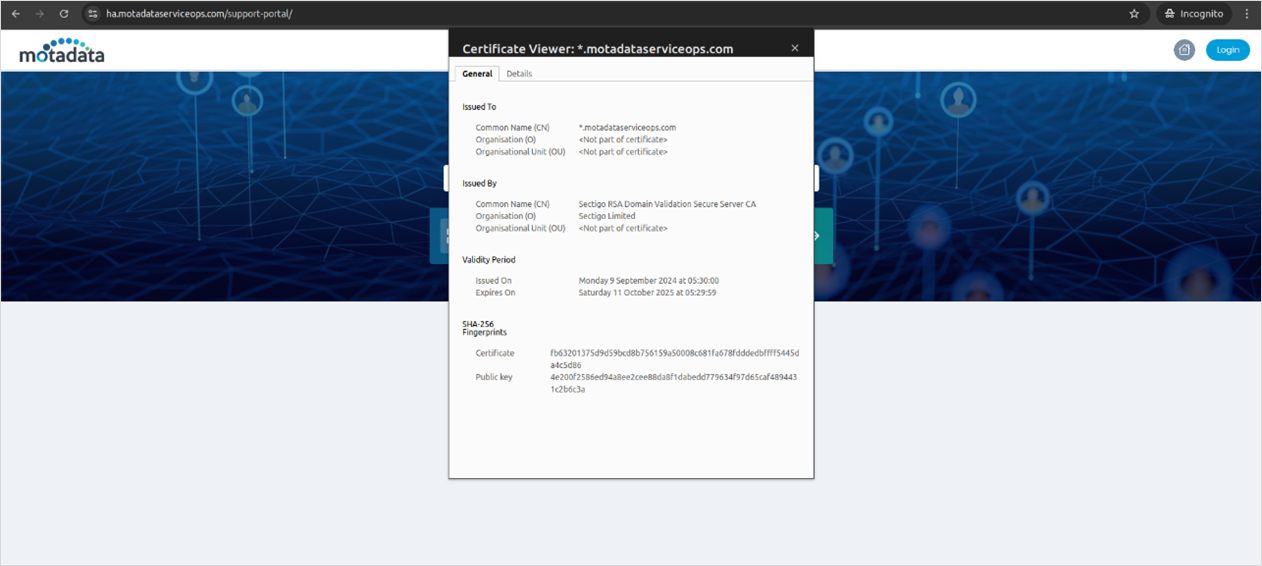
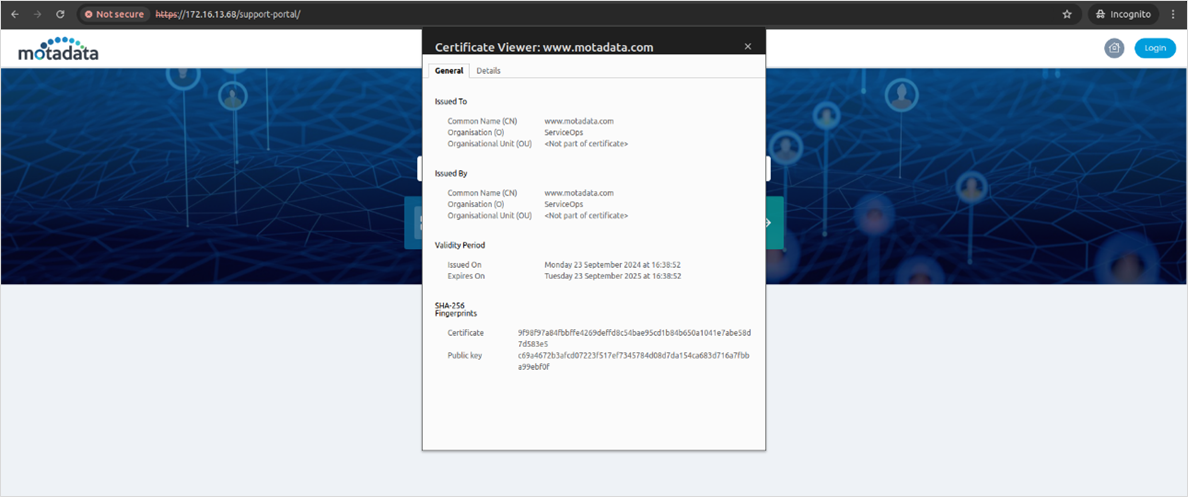
systemctl restart haproxyVerify the HTTPS URL by viewing the certificate on the browser.
7. If backend port 443 (HTTPS) is required, change it as shown below.
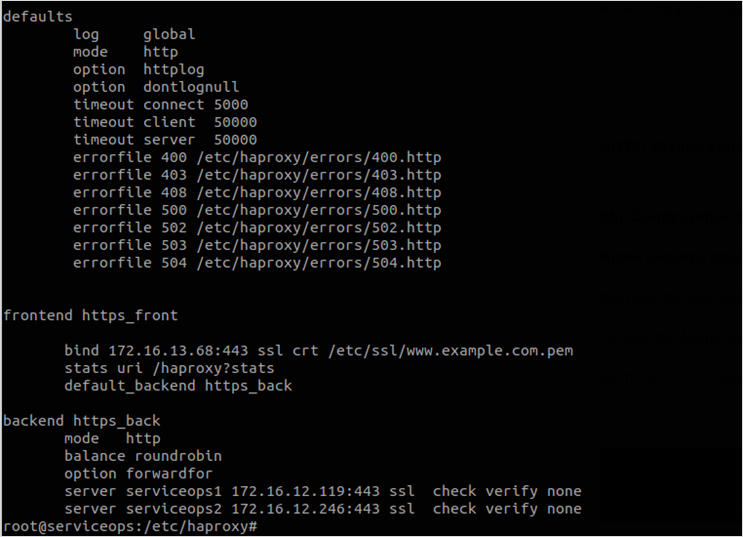
The SSL certificate file must be the same on all three nodes: HA Proxy, Master, and Slave.
Next, after updating the port, restart the HA Proxy server service before validating the haproxy.cfg file.
Verify the port number is open from the OS Firewall and Network side.
Nginx Server
To configure SSL in the Nginx server,
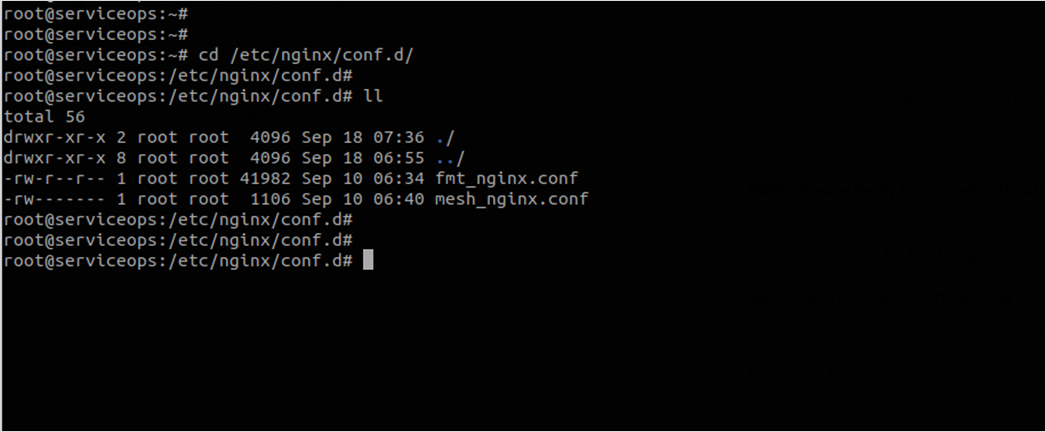
- Add the below code in the fmt_nginx.conf file. You can find the file from the location “/etc/nginx/conf.d/fmt_nginx.conf”.
server {
listen 80;
server_name localhost;
return 301 https://$host$request_uri;
}
server {
listen 443 ssl;
server_name localhost;
ssl on;
ssl_certificate /etc/ssl/certs/nginx.crt; <------ Add Client’s CRT file path
ssl_certificate_key /etc/ssl/private/nginx.key; <------ Add Client’s Key File Path
}
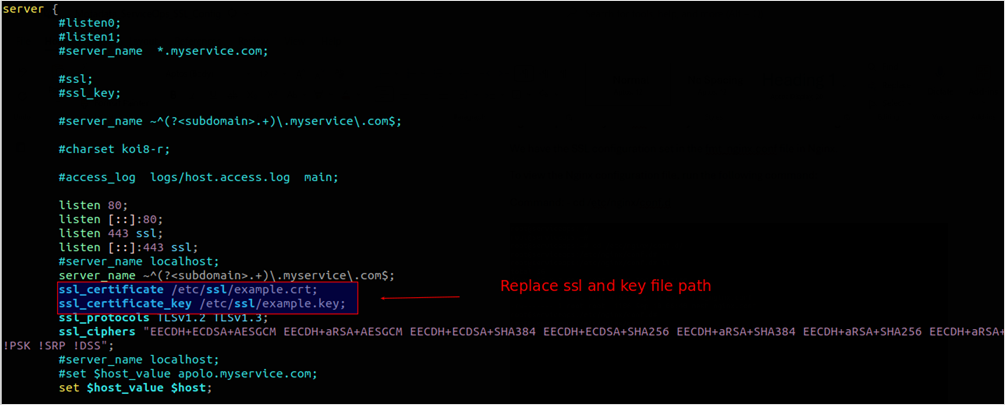
The above figure sets the SSL certificate path to /root/ssl on the server. The example.crt and example.key files are located at /root/ssl.
Once the necessary changes are done, save the file.
To check the syntax and validate the Nginx configuration, use the following command:
nginx -t
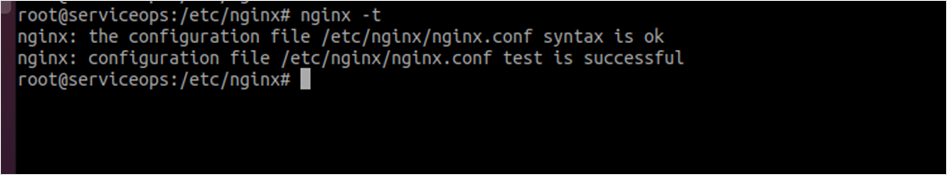
When the syntax validation is successful, restart the Nginx service using the below command:
systemctl restart nginx.servicePlease verify the HTTPS URL below.
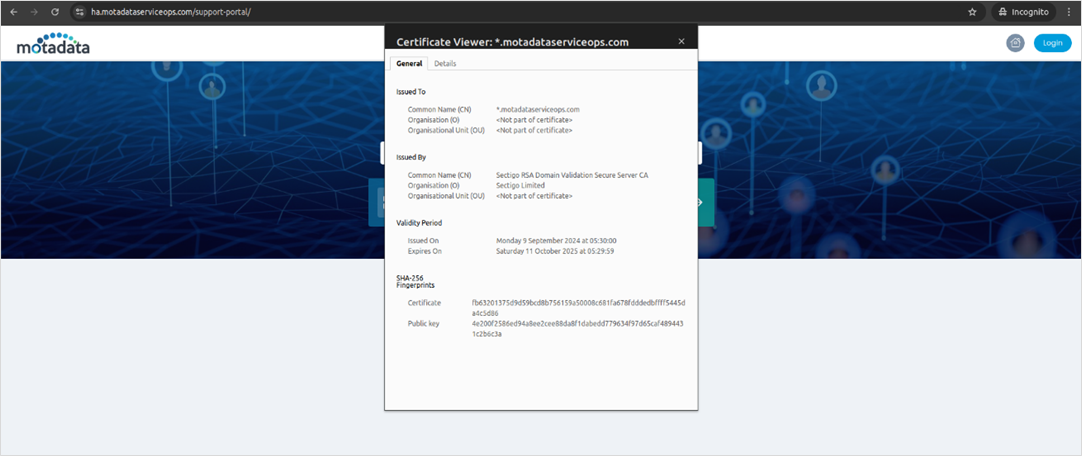
MeshCentral Server
Once the MeshCentral server is installed, update its valid SSL certificate file by following the below steps:
- Check and stop the MeshCentral server service using the below commands:
systemctl status meshcentral
systemctl stop meshcentral
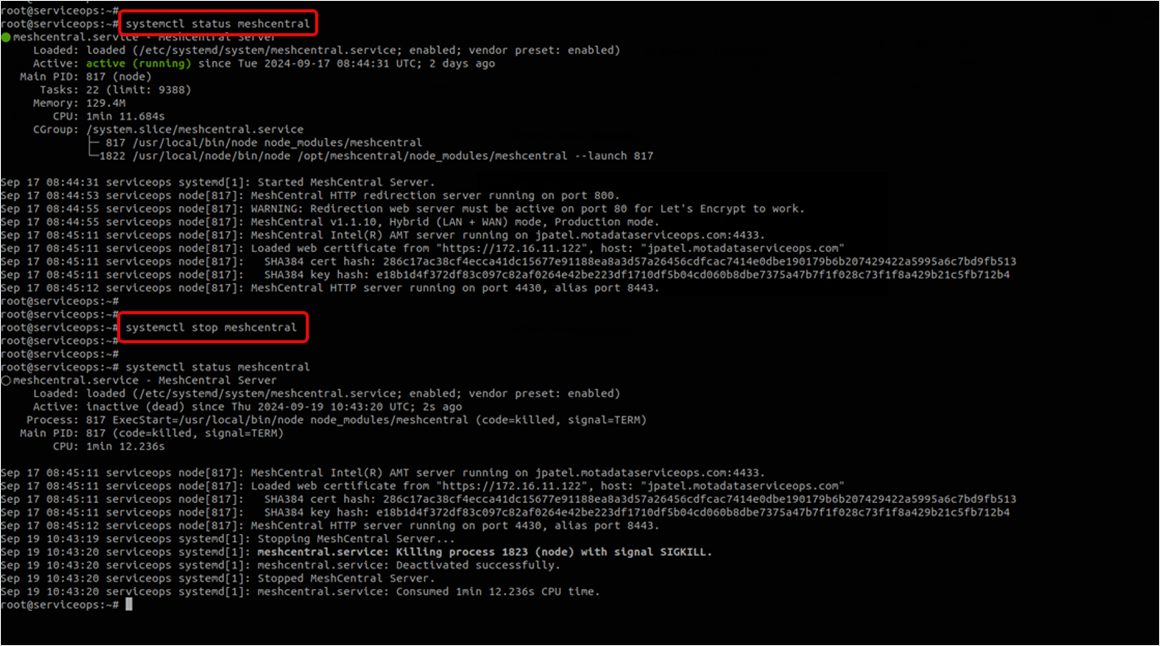
Once the service is stopped, verify its status using the above command again.
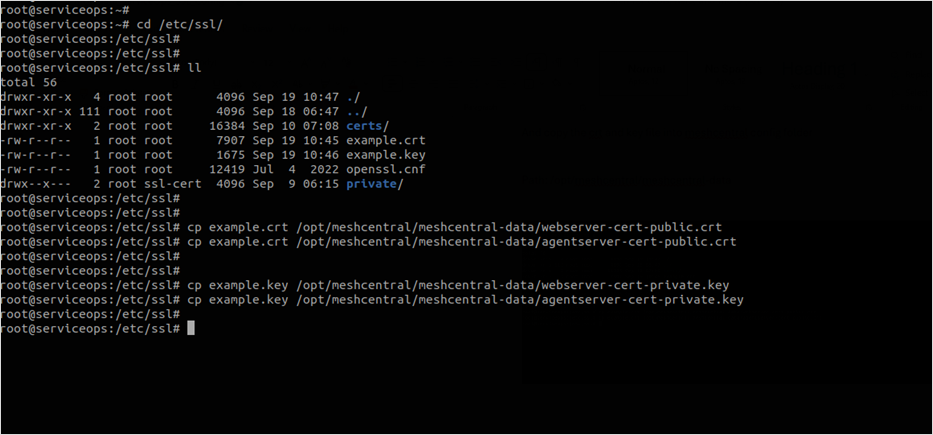
Next, download or transfer the valid SSL certificate file into the meshcentral server and go to the file path “/etc/ssl/”.
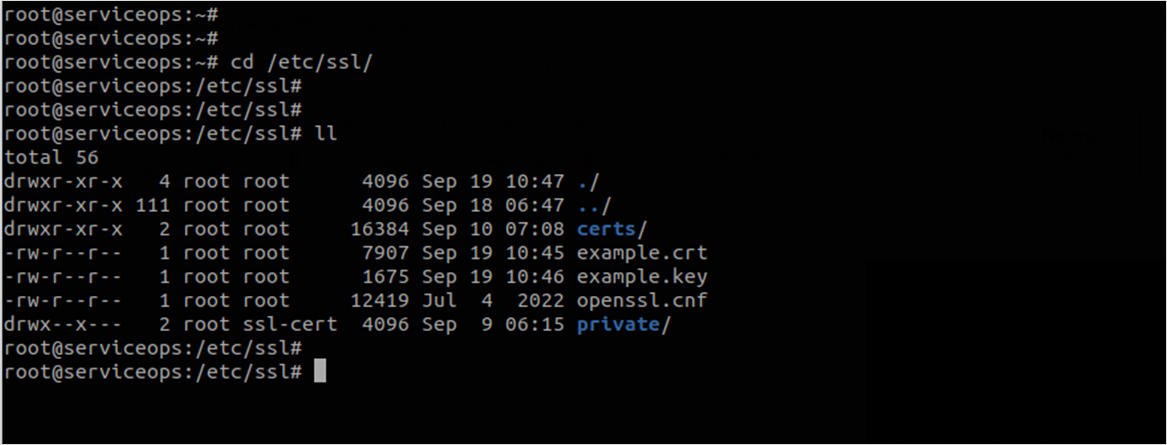
- Copy the .crt and .key files into the meshcentral config folder located at the location “/opt/meshcentral/meshcentral-data”
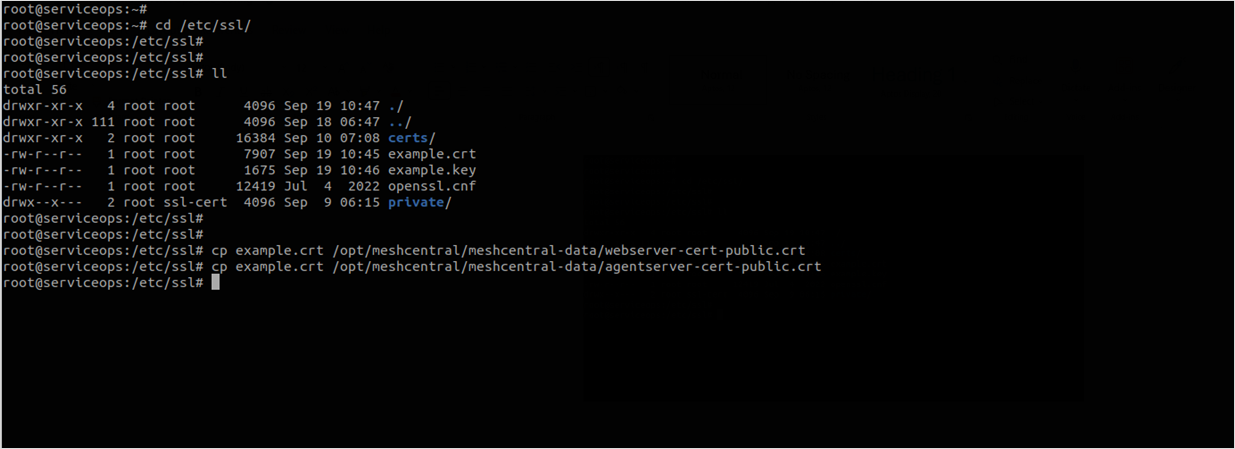
Copy the cert file into the meshcentral config folder using the below commands:
cp example.crt /opt/meshcentral/meshcentral-data/webserver-cert-public.crt
cp example.crt /opt/meshcentral/meshcentral-data/agentserver-cert-public.crtAlso, copy the private key files into the meshcentral config folder using the below commands:
cp example.key /opt/meshcentral/meshcentral-data/webserver-cert-private.key
cp example.key /opt/meshcentral/meshcentral-data/agentserver-cert-private.key
Once the configuration is added, verify it using the below command:
nginx -tOnce done, restart the meshcentral server service using the below command:
systemctl start meshcentral
- Once the cert and key files are copied into the meshcentral config folder, ensure that the ssl cert files on the meshcentral config folder have the required user ownership and permission.
- Ensure the meshcenral nginx ssl file path is proper. Kindly verify once you start using meshcentral server services.