Configuring Microsoft Azure for OAuth
What is Microsoft Azure?
Microsoft Azure is a public cloud computing service owned by Microsoft. It provides a wide range of cloud services, including analytics, storage, computing, and networking.
What is OAuth?
OAuth is an Open Standard Authorization protocol that allows you to authenticate one application communicating with another on your behalf without sharing the password. It uses client secret values instead of a password to allow access to a secured resource. Thus, the email communication will be secured.
This functionality is applicable from version 7.9 and above.
Prerequisites
Internet connectivity between ServiceOps and Microsoft Azure/Office 365 is required.
Redirect URL should be HTTPS.
To enable HTTPS in ServiceOps, a valid SSL Certificate is required.
Configure your firewall settings to allow communication between ServiceOps and the following Microsoft Office 365 URLs:
- login.microsoftonline.com (For Enterprise application)
- outlook.office365.com (SMTP, IMAP, and POP3) (For Enterprise application)
- login.live.com (For Personal accounts)
Whitelist these URLs to ensure that they are not blocked or restricted by your organization's network infrastructure. For more URLs and IP Address, refer to the link Office 365 URLs and IP address ranges.
The Microsoft Azure user should have administrator rights.
Configuring Microsoft Azure as Incoming Email Server
To configure Microsoft Azure as the Incoming Email server, follow the below steps:
- Sign in to the Microsoft Azure portal.
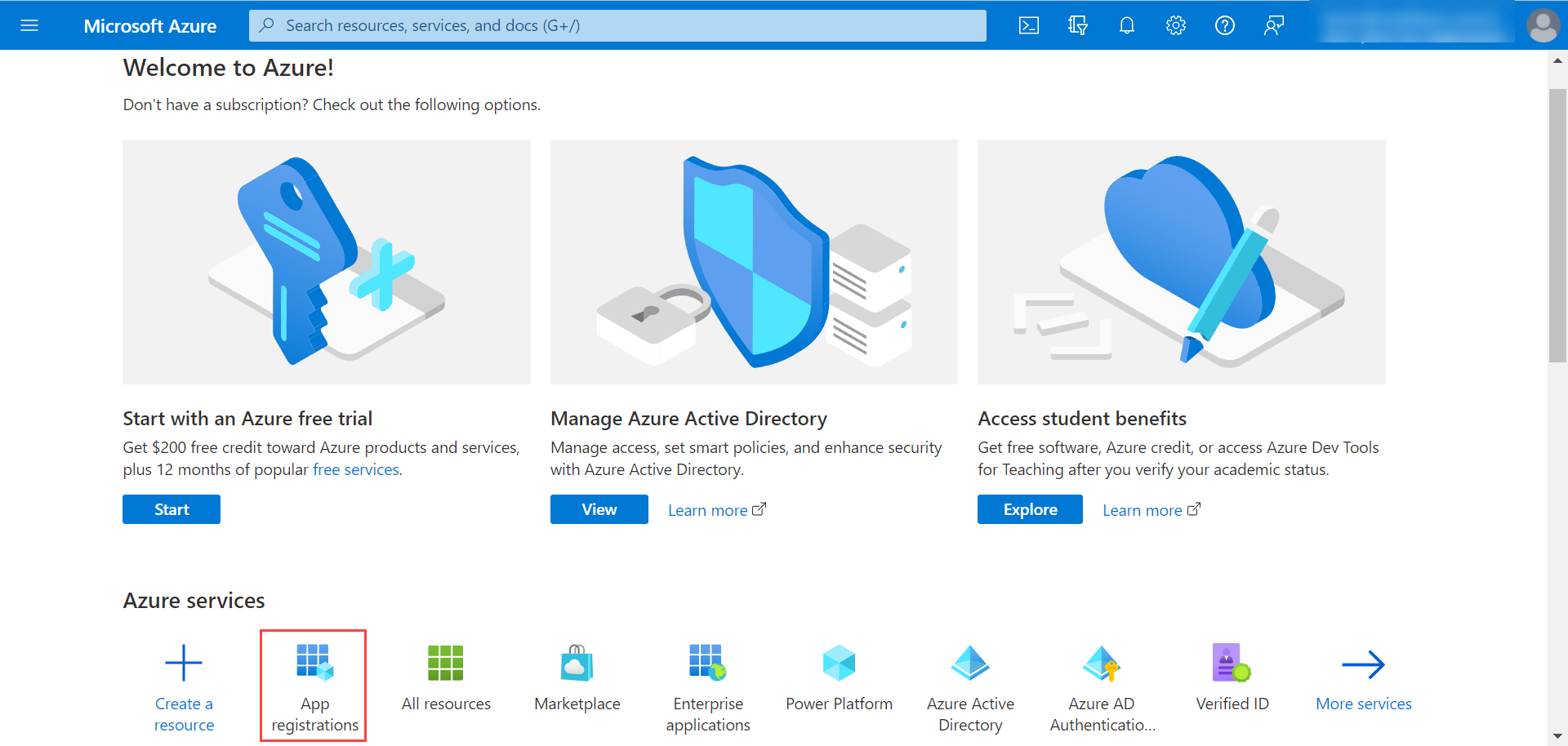
In the Azure services section, click App registrations > New Registration.
noteCreate a separate app for every incoming email server (in ServiceOps), if multiple servers are configured each with different domains.
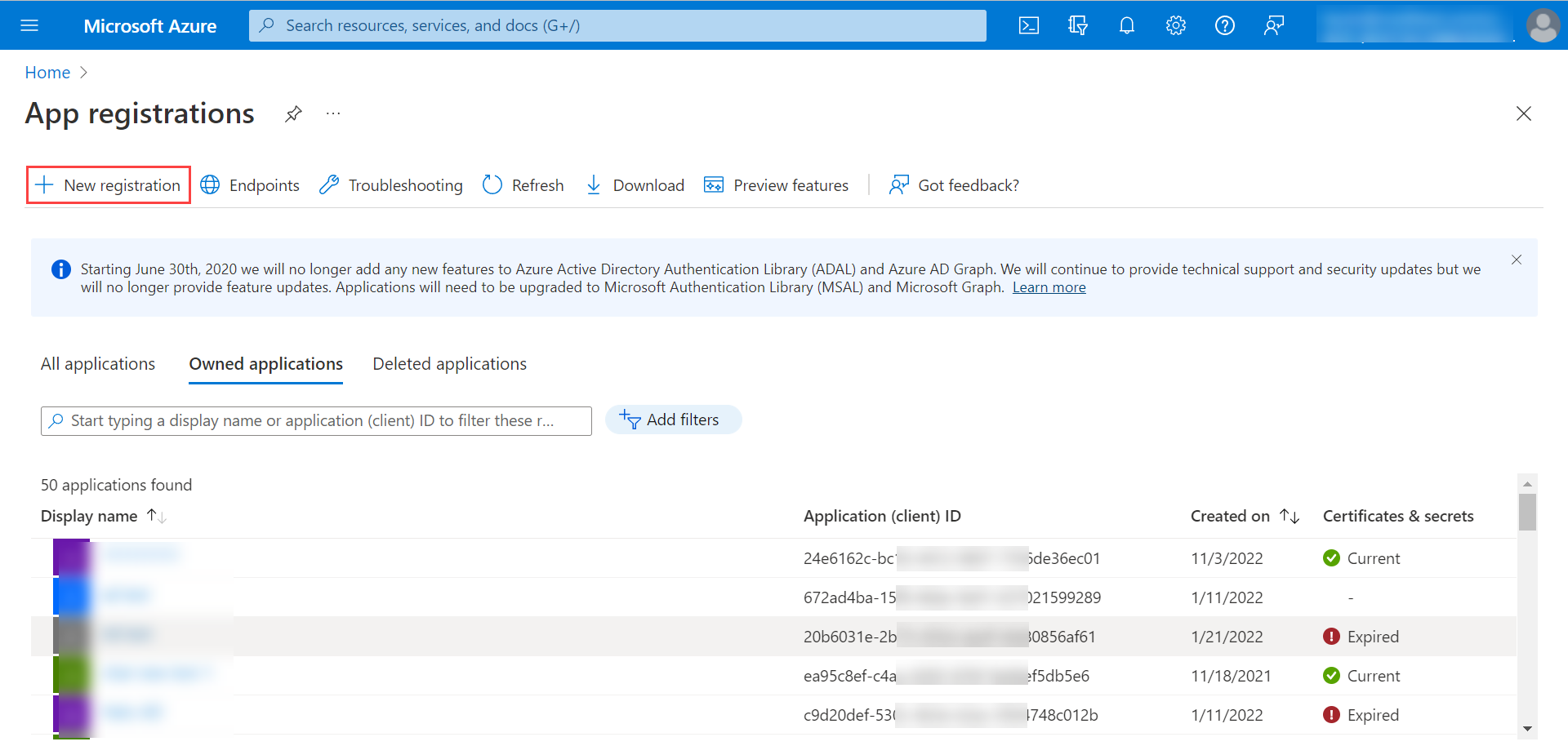
In the next screen, enter the name, and select the Supported account types. Under Redirect URI section, select the Platform as Web, and enter the Redirect URI.
Syntax for Redirect URI: https://{server URL}/oauth/callback
For example: https://dummy.com/oauth/callback
Once done, click Register.
The application will appear in the list as shown below.
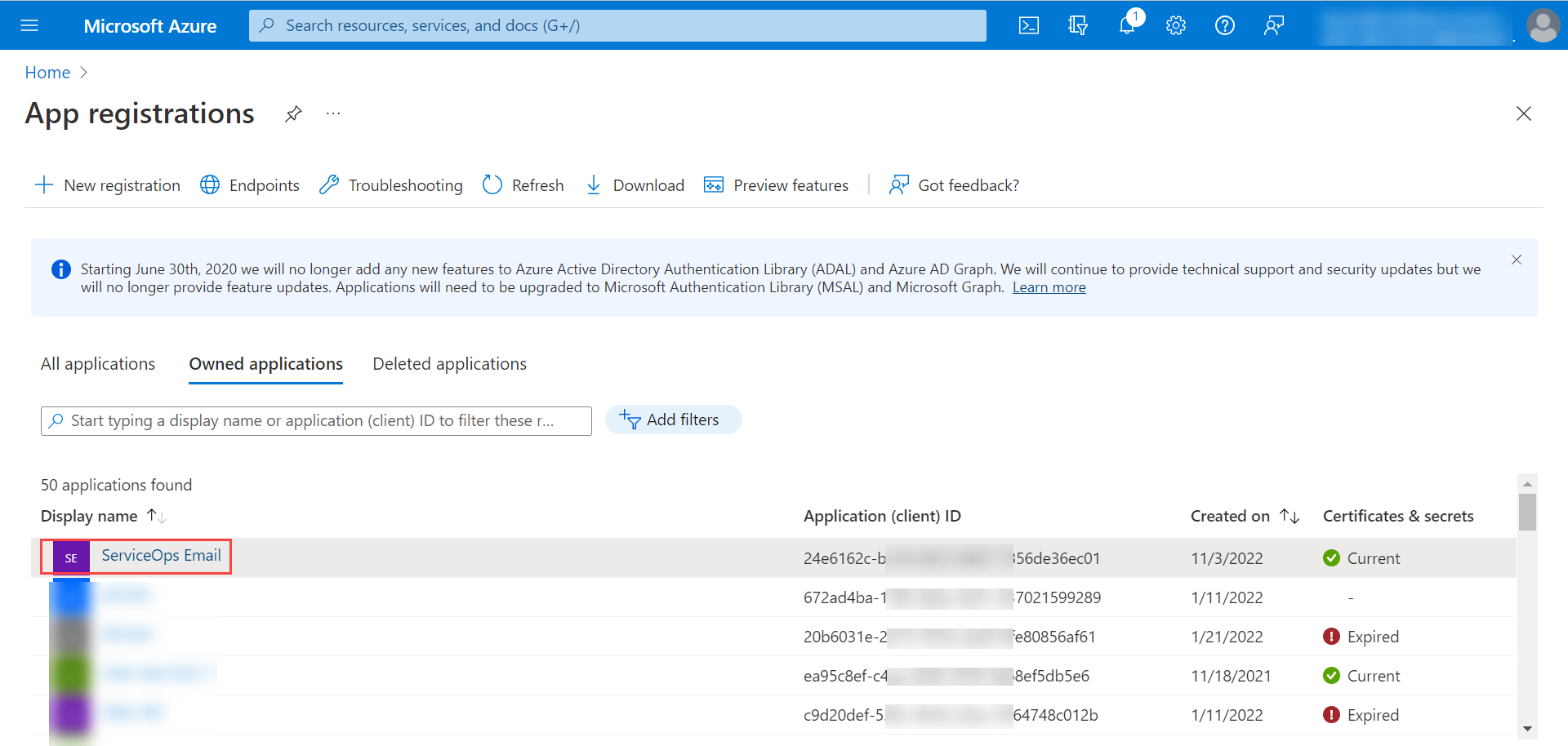
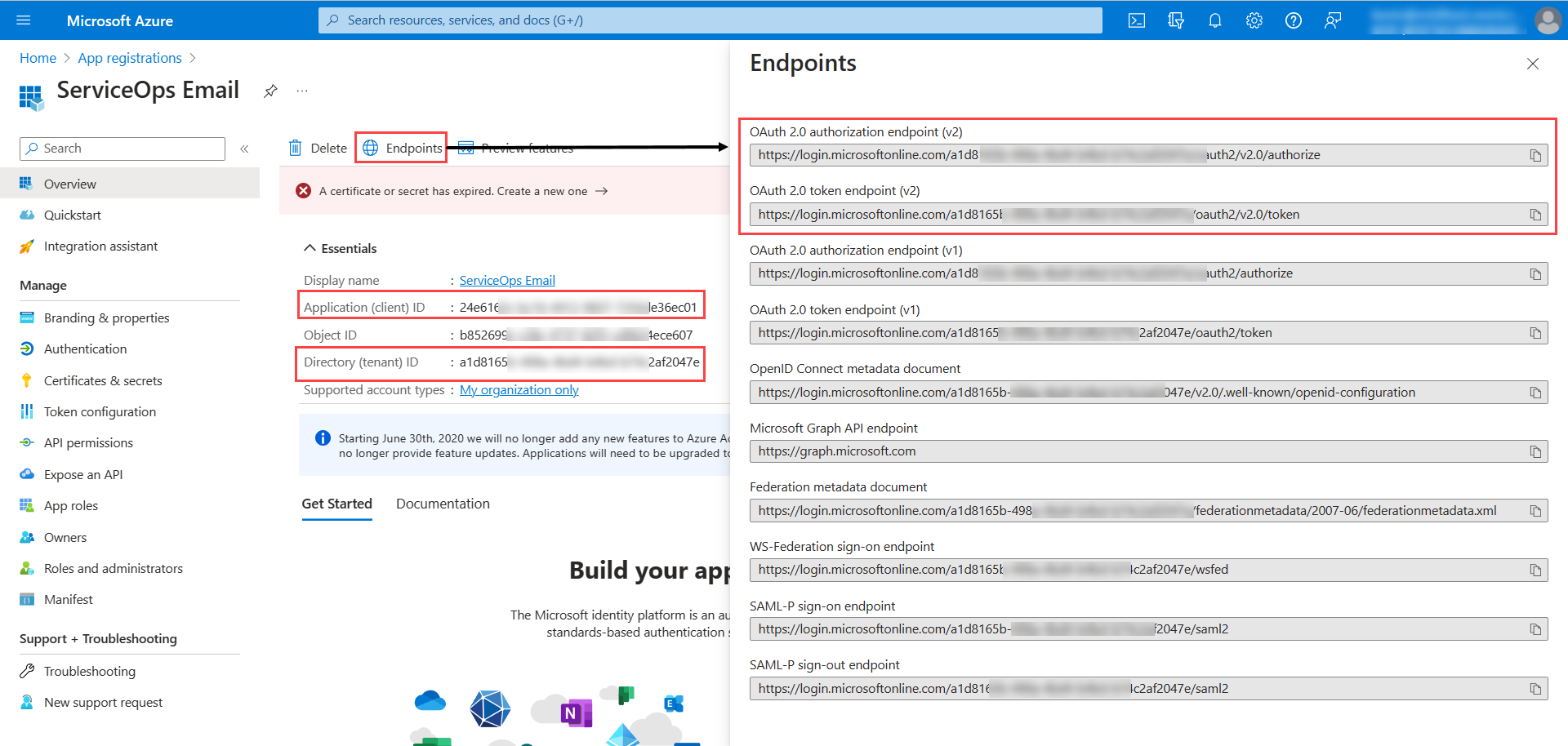
- Click on the application, and the below screen appears. Copy the Application (client) ID and paste it in ServiceOps. For Authorization and Token URL either click the Endpoints tab and copy OAuth 2.0 authorization endpoint (v2) and OAuth 2.0 token endpoint (v2) URLs from the popup or copy the Tenant ID from Overview and use it for both the URLs in ServiceOps.
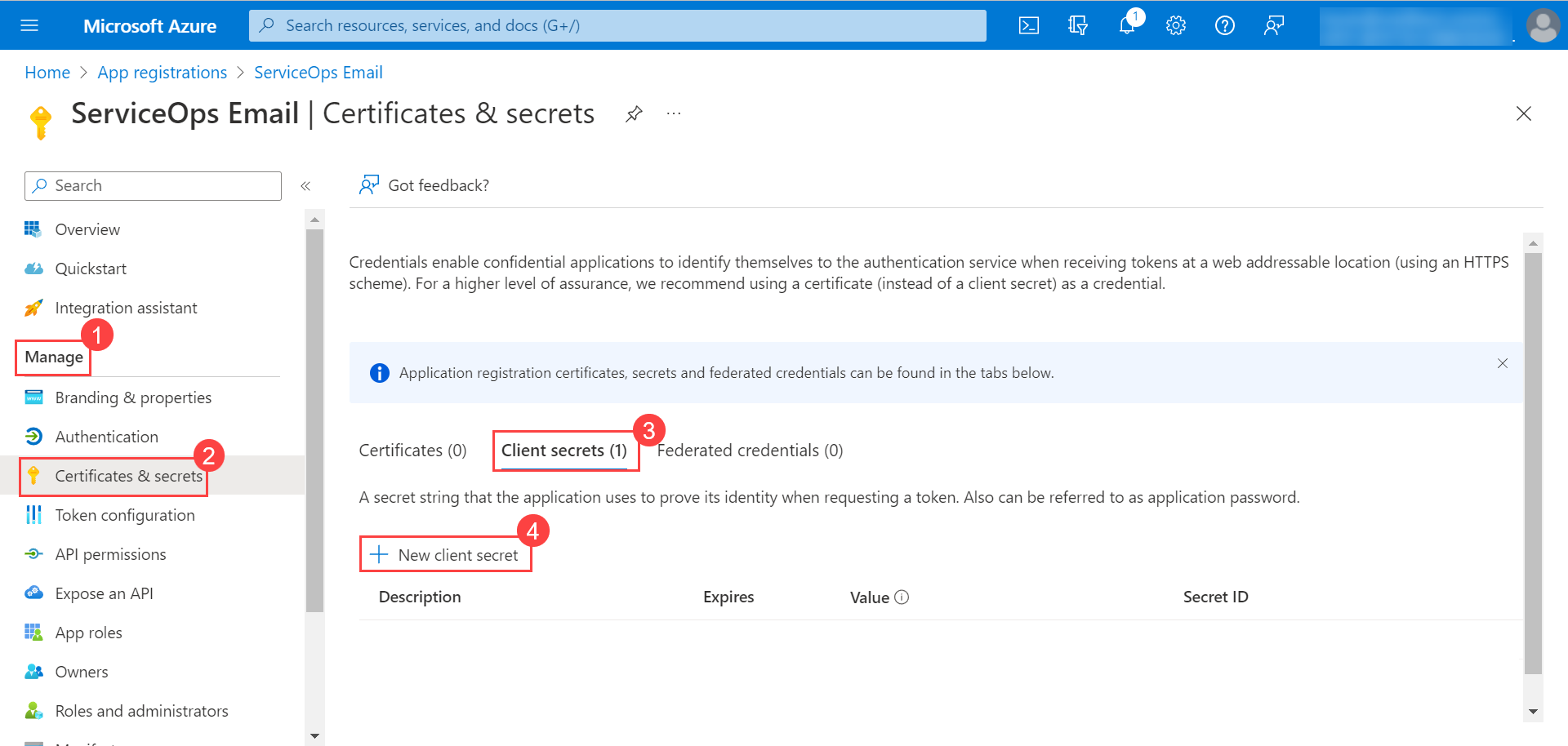
- Go to the Manage > Certificates & secrets > Client secrets tab, and click New Client Secret.
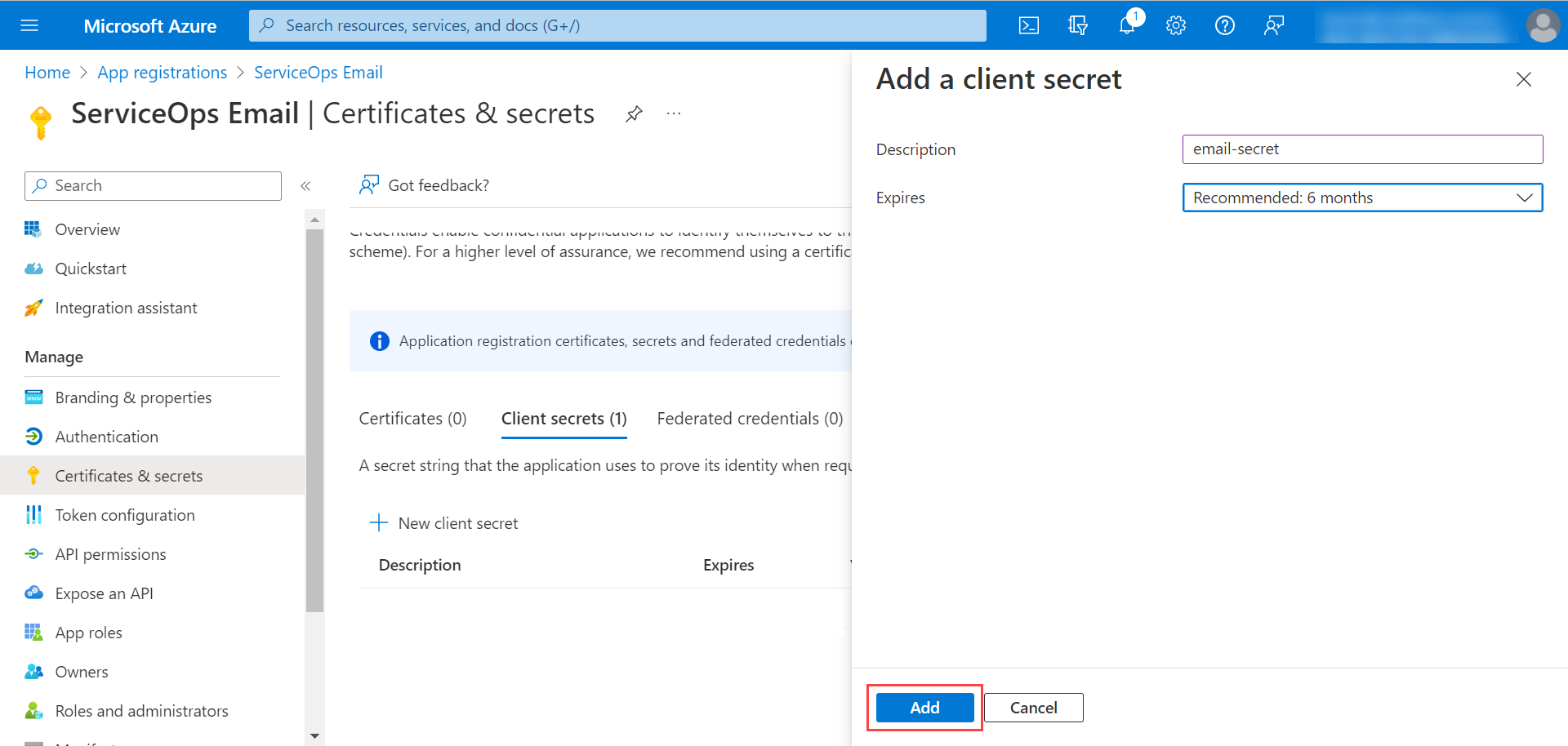
- Enter the description, select the expiry time, and click Add.
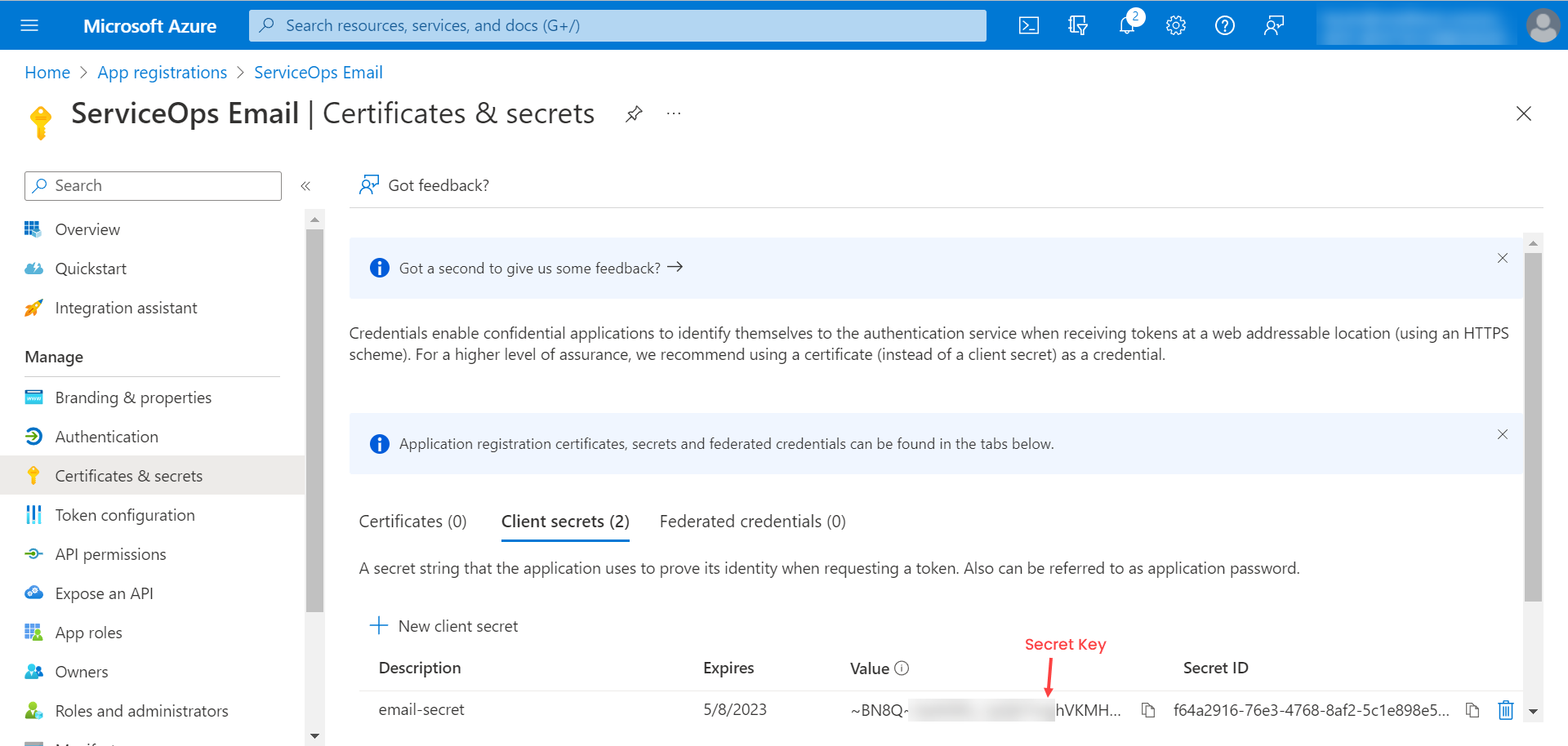
The secret appears in the table as shown below. Copy it too.
noteThe client secret value can be viewed only once immediately after creation. Hence, it is recommended to save the secret key before leaving the page.
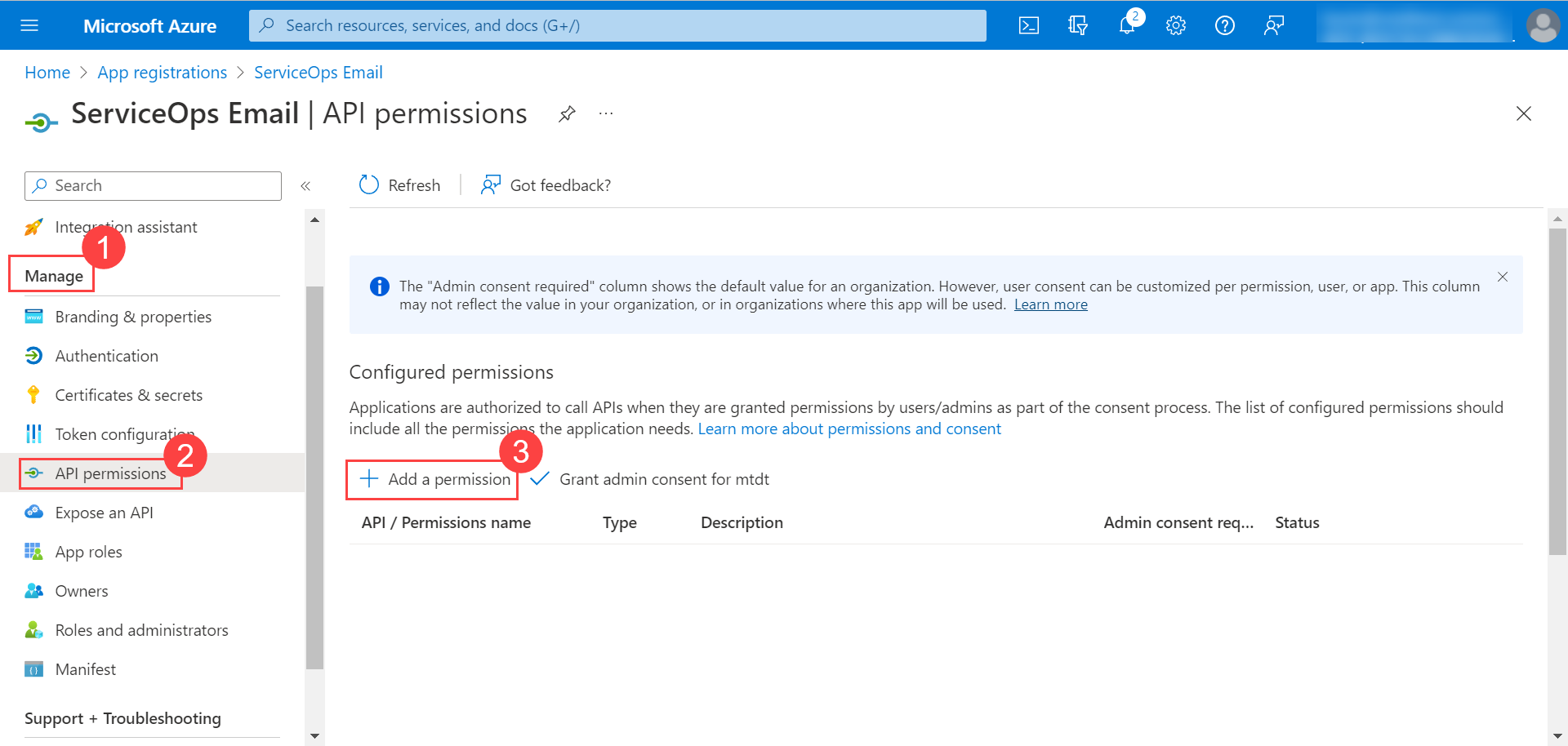
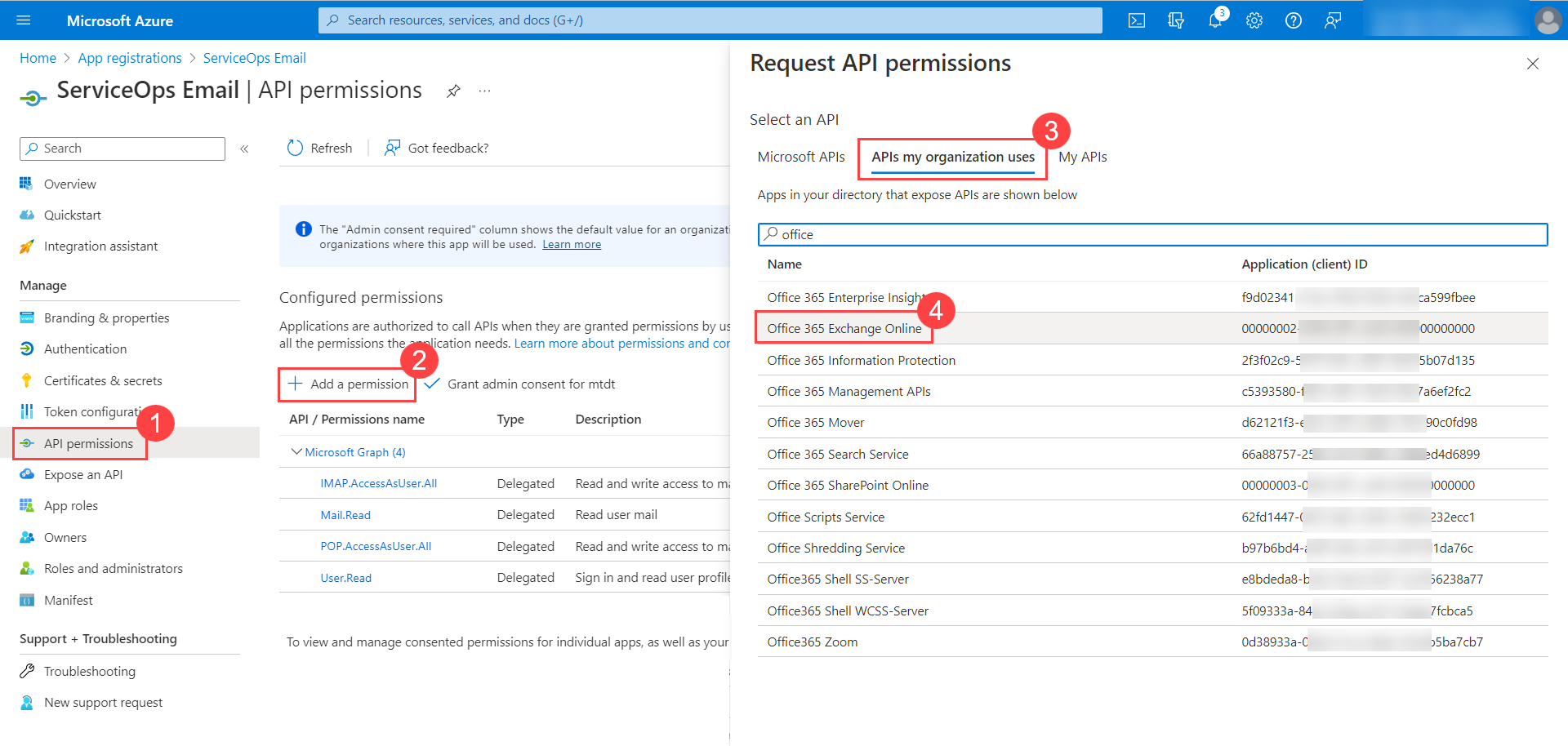
- In Microsoft Azure, go to Manage > API Permissions tab, and click Add a permission to add permissions for the application.
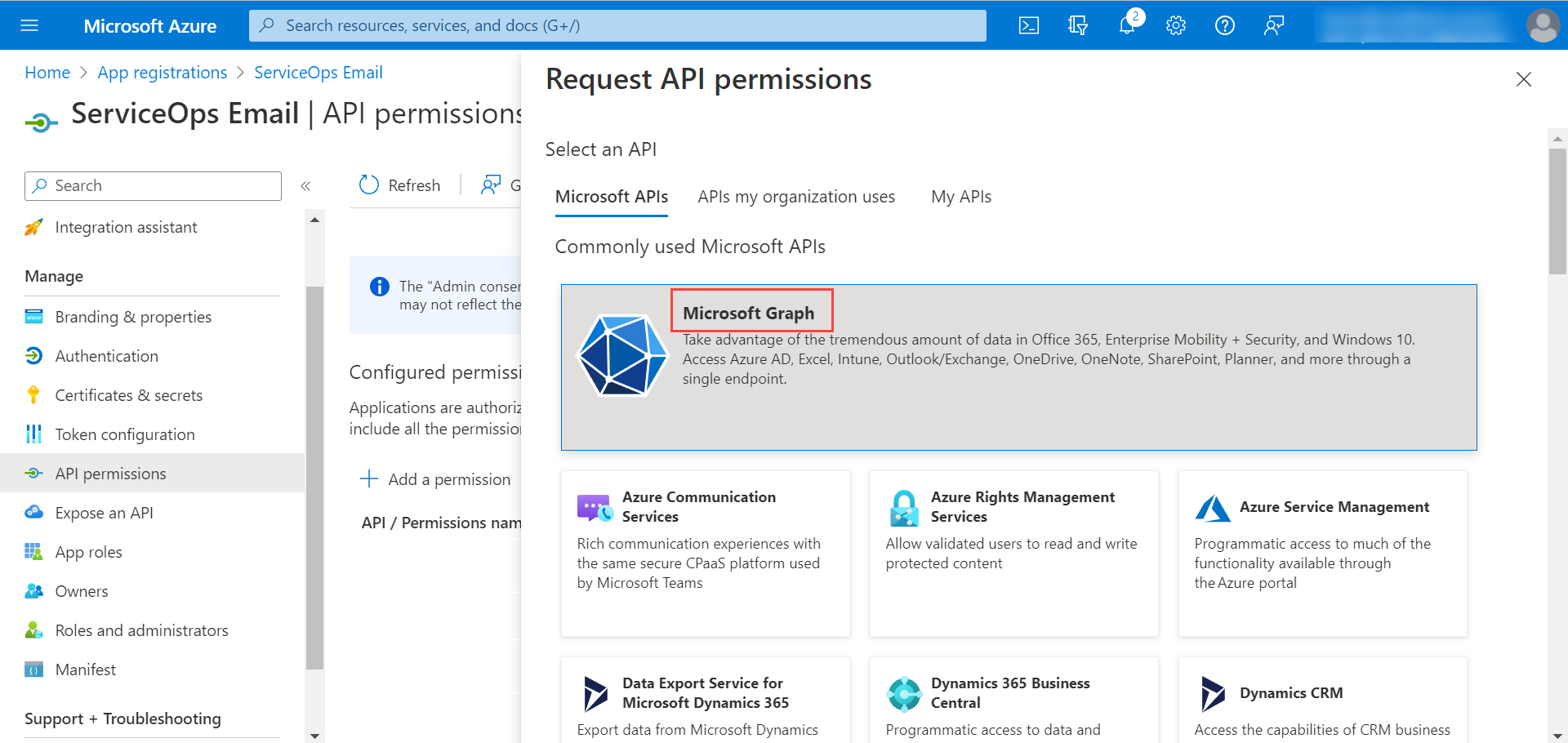
- The Request API Permissions popup appears. Click Microsoft Graph.
- Add Permissions for IMAP or Office 365 Exchange Online (MAPI).
IMAP
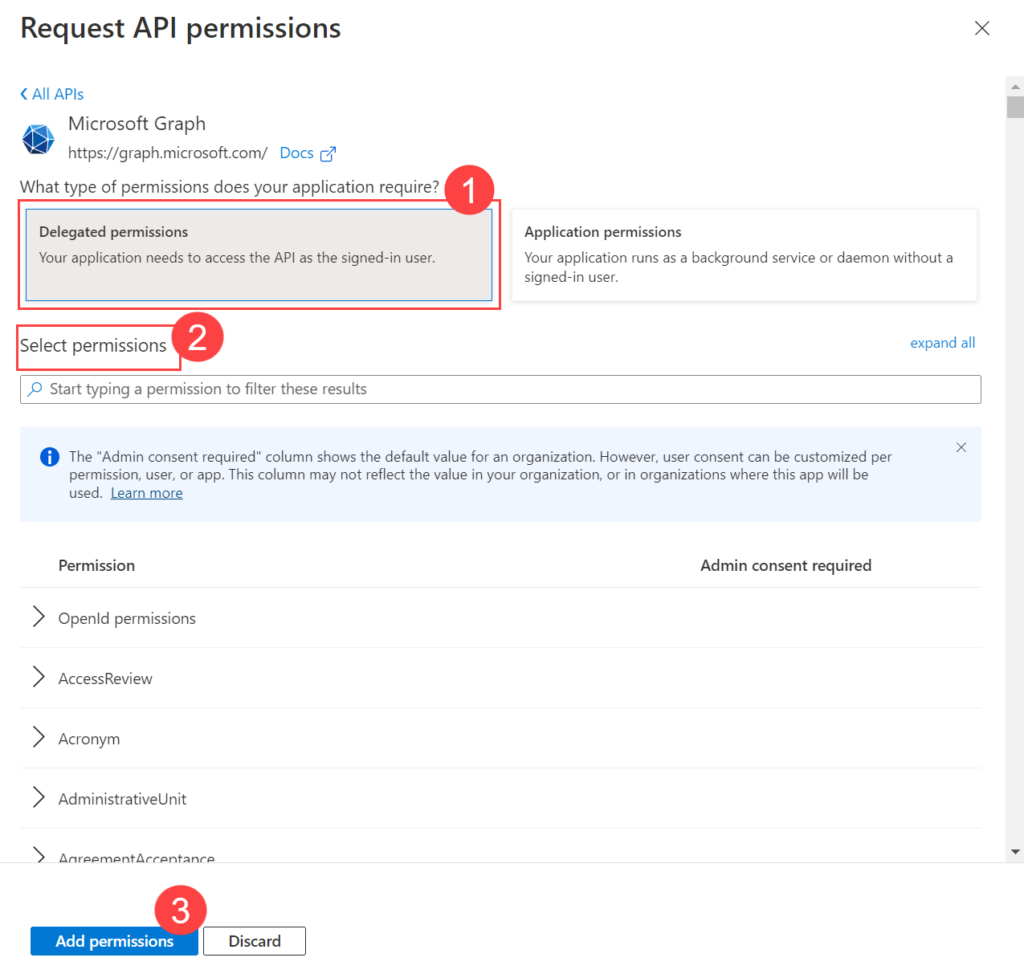
Select Delegated Permissions, select the desired permissions for the application, and click Add Permissions.
The Azure application must have the below Delegated permissions for IMAP: Microsoft Graph (Delegated Type):
- IMAP.AccessAsUser.All
- Mail.Read
Office 365 Exchange Online (For MAPI)
- For Office 365 Exchange, click Add a Permission > APIs my organization uses tab, search for the Office 365 Exchange Online permission, and click on it.
The Azure application must have the below Application permissions for MAPI: Office 365 Exchange Online: (Application Type):
- Exchange.ManageAsApp
- Full_access_as_app
- Mail.Read
- Mail.ReadWrite
- Next, click on the Application permissions tab, select the desired permissions, and click Add Permissions.
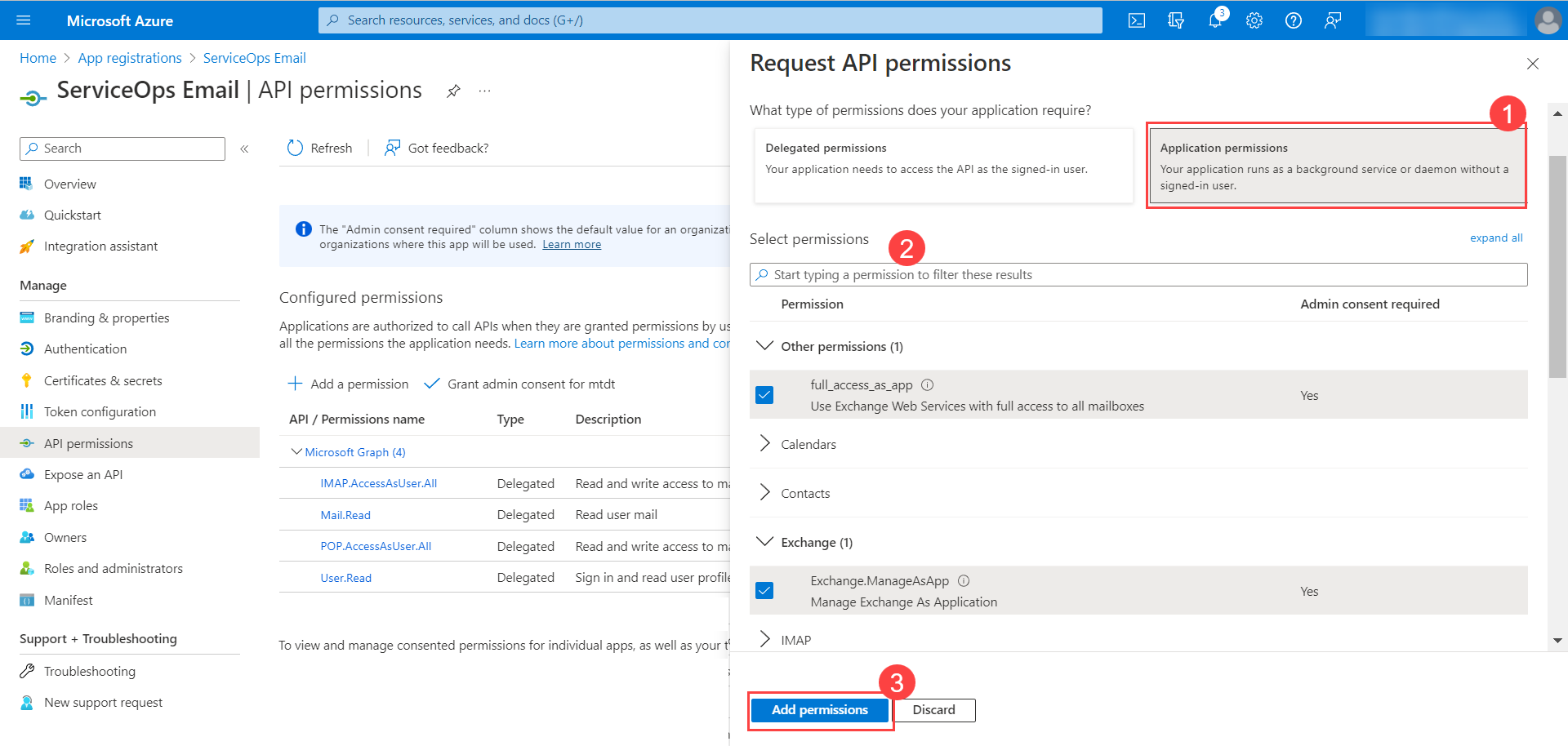
- Click Grant admin consent for
. A confirmation window will appear. Click Yes to continue.
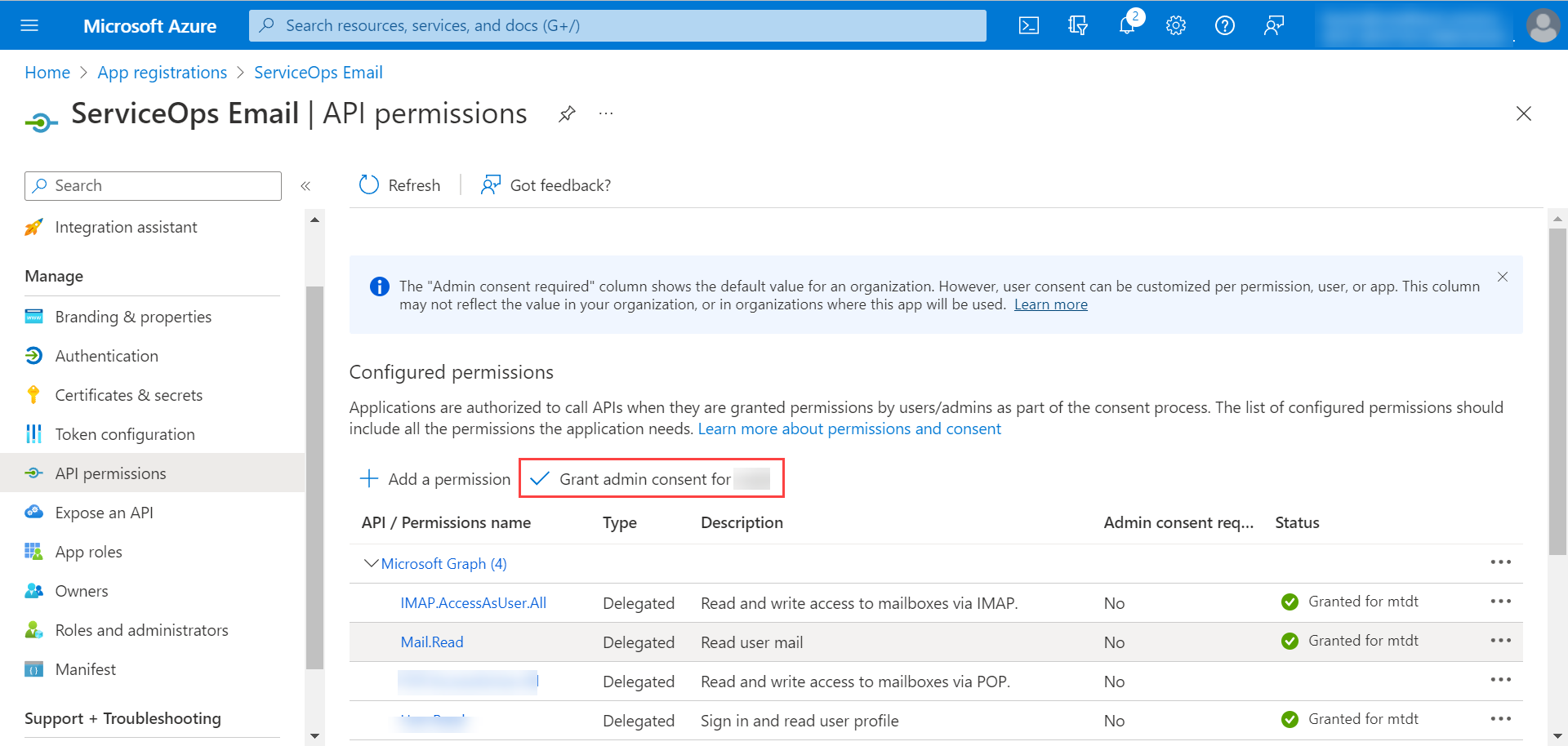
The Grant admin consent option will be enabled only if you are logged in as a user with Azure Global Administrator rights. For more details, refer Grant Tenant-wide admin consent to an application.
- For IMAP, register your Azure AD Application service principals in Exchange Online and grant access to the Exchange Online mailbox to this service principal. For more details, refer Register service principals in Exchange.
- For IMAP and MAPI, it is recommended to restrict the mailbox access, so that Azure app can access only a single mailbox. For more details, refer Limiting application permissions to specific Exchange Online mailboxes.
Configuring Microsoft Azure in ServiceOps
Now, login to the ServiceOps Portal, and go to Admin > Support Channel > Emails > Incoming Email Servers tab. Click the Add Incoming Email Server button, and the below popup appears.
After upgrading the ServiceOps version from 8.0 to 8.1, kindly check for the additional parameters unavailable in the previous version.
In ServiceOps version 8.0, the email configuration was based on the Client ID, Client Secret, Tenant ID, and the Authorization URL details. And now in version 8.1, it is based on the Client ID, Client Secret, Authorization URL, Token URL, Scope, and Redirect URL. You can get all these details by following the steps described in the above sections.

Enter the required details,
| Parameters | Description |
|---|---|
| Name | Enter the name of the email server. |
| Enter the email address of the Azure user. | |
| Technician Group | Select the technician group that should be assigned when a new request is created via the email. |
| Category | Select the category that you want to assign. If selected, the selected Category will get assiged to the ticket created using this email server. |
| Proxy Server | Select the proxy server. |
| Email Provider | Other |
| Server | Enter the server address of the server as per the protocol selected. The addresses are: - IMAP: outlook.office365.com - POP3: outlook.office365.com - MAPI: outlook.office365.com |
| Port | Enter the port number of the email server. The numbers are: - IMAP: 993 - POP3: 995. |
| Protocol | Select the protocol that the email server supports. The options are: IMAP, MAPI, and POP3. |
| Security Type | Select the type of security that the email server supports. The options are: None, SSL and TLS. |
| Email Auth Type | Select Oauth as email auth type. |
| Client ID | Paste the client ID copied from Microsoft Azure (Step 4). |
| Client Secret | Paste the client secret copied from Microsoft Azure (Step 7). |
| Authorization URL | Enter the OAuth 2.0 authorization endpoint (v2) URL copied from Step 4. |
| Token URL | Enter the OAuth 2.0 token endpoint (v2) URL copied from Step 4. |
| Scope | Enter the scope as per the protocol selected. - IMAP: offline_access https://outlook.office365.com/IMAP.AccessAsUser.All - MAPI: offline_access https://outlook.office365.com/EWS.AccessAsUser.All - POP: offline_access https://outlook.office365.com/POP.AccessAsUser.All |
| Redirect URL | This is an editable field. It is set from the Application Settings Base URL. |
| Enabled | Toggle the switch to enable or disable the server. |
| Company | Select the company that should be assigned to the request when created via email. Note: This field is available only if Managed Services Provider feature is enabled. |
| Primary | Enable if you want to use this server as primary for receiving the emails. |
| Outgoing Email Severs | Enable if you want to set the outgoing email server. |
| Outgoing Email | Select the outgoing email server from the dropdown. The list displays the servers added in the Outgoing Email Servers section. |
| Filter Type | Select whether to allow or ignore the emails received. |
| Emails | Add the email addresses that should be evaluated based on the filter type selected. |
| Domains | Add the domains that should be evaluated based on the filter type. For example: yahoo.com. |
| Keywords | Add the keywords that should be evaluated based on the filter type. The system will look for keywords in the email subject and body. |
For Active Directory Users:
Authorization Url: Enter the OAuth 2.0 authorization endpoint (v2) URL copied from Step 4. You can also use the Tenant ID from step 4 and enter the URL as per the below format.
Format: https://login.microsoftonline.com/{Tenant-ID}/oauth2/v2.0/authorize
Sample: https://login.microsoftonline.com/a1d8165b-498a-4bd4-b4bd-b74c2af2047e/oauth2/v2.0/authorize
Token Url: Enter the OAuth 2.0 token endpoint (v2) URL copied from Step 4. You can also use the Tenant ID from step 4 and enter the URL as per the below format. Format: https://login.microsoftonline.com/{Tenant-ID}/oauth2/v2.0/token
Sample: https://login.microsoftonline.com/a1d8165b-498a-4bd4-b4bd-b74c2af2047e/oauth2/v2.0/token
For Non-Active Directory Users:
- Authorization Url: https://login.live.com/oauth20_authorize.srf
- Token Url: https://login.live.com/oauth20_token.srf
Once done, click Save to add the Incoming Email Server. You can later check its connection using the Test Connection button from the server list page.
Microsoft Azure is now configured as an email server for ServiceOps.
Configuring Microsoft Azure as Outgoing Email Server
To configure Microsoft Azure as the Outgoing Email Server, follow the below steps:
Follow the above steps from 1 to 9 of the Incoming Email Server section.
Add Permissions for SMTP. Select Microsoft Graph > Delegated Permissions, select the SMTP permission for the application, and click Add Permissions.
noteThe Azure application must have the SMTP.Send Delegated permission.
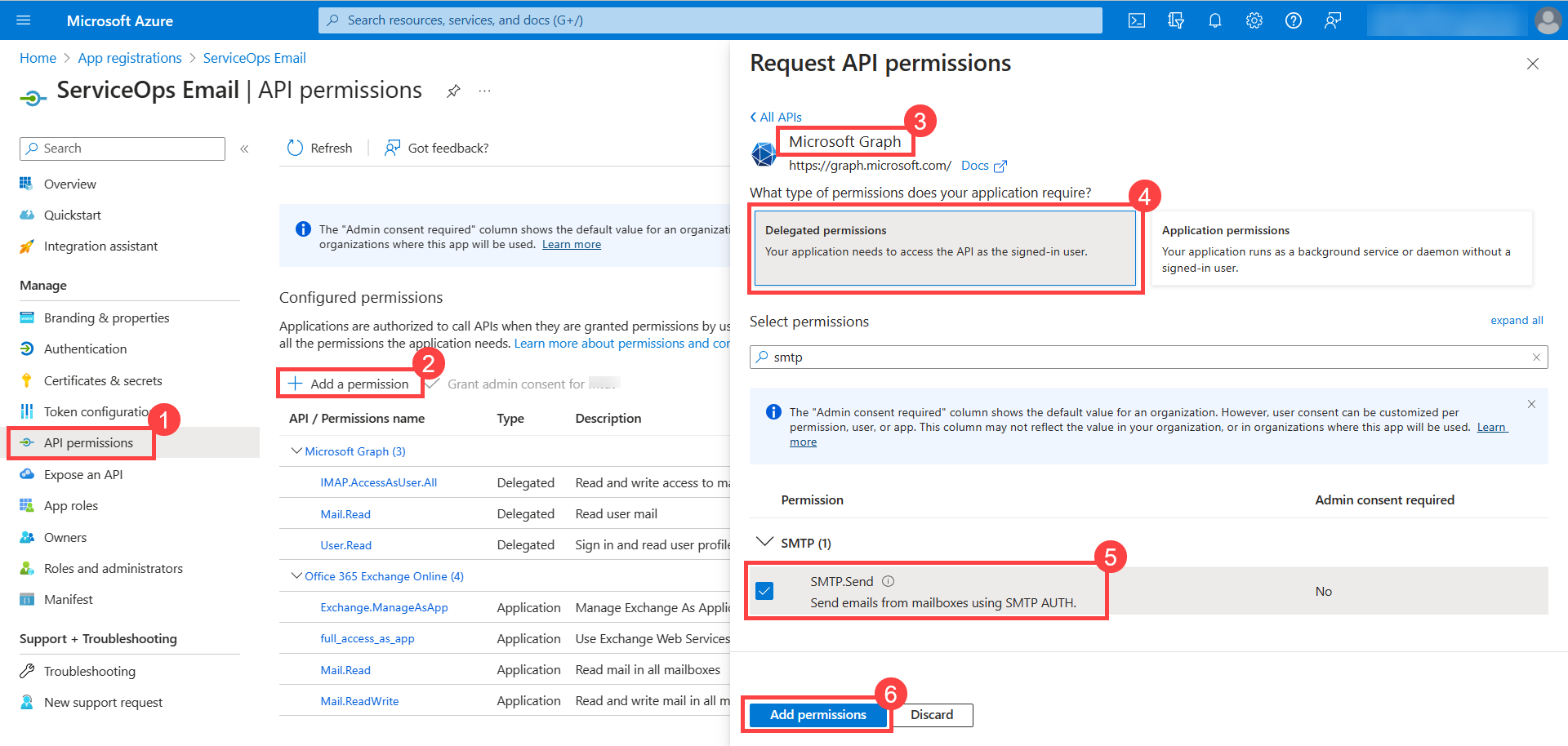
Click Grant admin consent for {directory}. A confirmation window will appear. Click Yes to continue.
The Grant admin consent option will be enabled only if you are logged in as a user with Azure Global Administrator rights. For more details, refer Grant Tenant-wide admin consent to an application.
Configuring Microsoft Azure in ServiceOps
Now, login to the ServiceOps Portal, and go to Admin > Support Channel > Emails > Outgoing Email Servers tab. Click the Add Outgoing Email Servers button, and the below popup appears.

Enter the required details,
| Parameters | Description |
|---|---|
| Name | Enter the name of the email server. |
| Enter the email address of the Azure user which will be used for authentication. | |
| Protocol | Select the protocol that the email server supports. The options are: SMTP and MAPI. |
| Sender Name | Enter the name of the sender. |
| Email Provider | Other |
| Server | Enter the address of the server. - SMTP: smtp.office365.com - MAPI: outlook.office365.com |
| Port | Enter the port number of the email server. - SMTP (TLS): 587 - SMTP(SSL): 465 |
| Security Type | Select the type of security that the email server supports. The options are: None, SSL and TLS. |
| Authentication Needed | Enable the flag if you want the user to authenticate to the server while logging in. |
| Email Auth Type | Select Oauth as the email auth type. |
| Username | Enter the username of the server to login. |
| Client ID | Paste the client ID copied from Microsoft Azure (Step 4). |
| Client Secret | Paste the client secret copied from Microsoft Azure (Step 7). |
| Authorization URL** | Enter the OAuth 2.0 authorization endpoint (v2) URL copied from Step 4. |
| Token URL** | Enter the OAuth 2.0 token endpoint (v2) URL copied from Step 4. |
| Scope | Enter the scope as per the protocol selected. - SMTP Scope: offline_access https://outlook.office365.com/SMTP.send - MAPI Scope: offline_access https://outlook.office365.com/EWS.AccessAsUser.All |
| Redirect URL | This is an editable field. It is set from the Application Settings Base URL. |
| Reply-To Email | Enter the email address for replying over the email. |
| Proxy Server | Select the required proxy server. |
| Enabled | Toggle the switch to enable or disable the server. |
| Primary | Enable if you want to use this server as primary for sending emails. |
For Active Directory Users:
Authorization Url: Enter the OAuth 2.0 authorization endpoint (v2) URL copied from Step 4. You can also use the Tenant ID from step 4 and enter the URL as per the below format.
Format: https://login.microsoftonline.com/{Tenant-ID}/oauth2/v2.0/authorize
Sample: https://login.microsoftonline.com/a1d8165b-498a-4bd4-b4bd-b74c2af2047e/oauth2/v2.0/authorize
Token Url: Enter the OAuth 2.0 token endpoint (v2) URL copied from Step 4. You can also use the Tenant ID from step 4 and enter the URL as per the below format.
Format: https://login.microsoftonline.com/{Tenant-ID}/oauth2/v2.0/token
Sample: https://login.microsoftonline.com/a1d8165b-498a-4bd4-b4bd-b74c2af2047e/oauth2/v2.0/token
For Non-Active Directory Users:
- Authorization Url: https://login.live.com/oauth20_authorize.srf
- Token Url: https://login.live.com/oauth20_token.srf
Once entered, click Save.
Microsoft Azure is now configured as an Outgoing Email Server for ServiceOps. Once done, you can later check its connection using the Test Connection button from the server list page. If you face any issue while connecting to the SMTP server, ensure that it is enabled from the Microsoft Admin Center account.
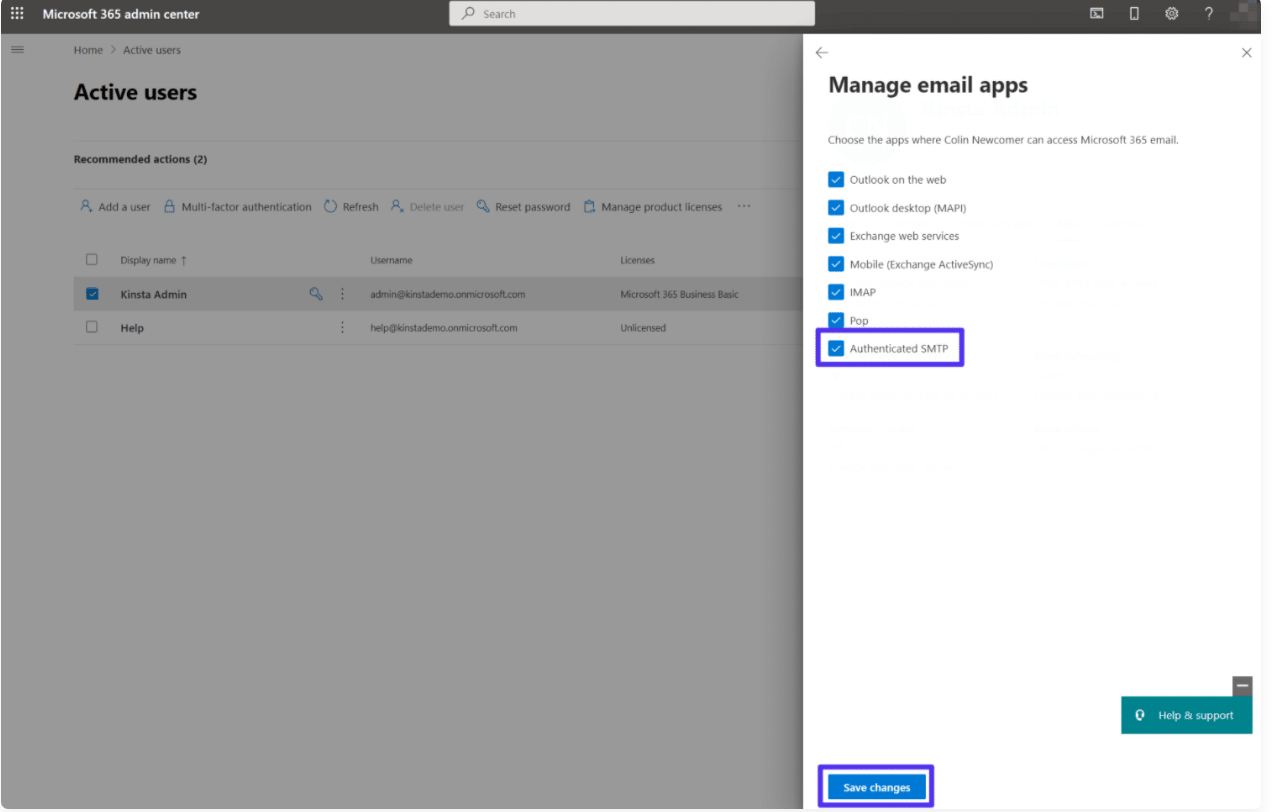
To enable SMTP Authentication, follow the below steps:
- Sign-in to your Microsoft 365 Admin Center with the admin account.
- Navigate to Users > Active Users, click the desired email address, and a popup appears.
- Select the Mail tab and click the Manage email apps link below the Email apps section.
- Select the option Authenticated SMTP and click Save changes as shown below.