How to Install the SSL Certificate?
SSL means a Self-signed certificate. An organization needs to install the SSL Certificate onto its web server to initiate a secure session with browsers. Once a secure connection is established, all web traffic between the web server and the web browser will be secure.
When a certificate is successfully installed on your server, the application protocol (HTTP) will change to HTTPs, where the ‘S’ stands for ‘secure’. Depending on the type of certificate you purchase and what browser you are surfing the internet on, a browser will show a padlock or green bar in the browser when you visit a website that has an SSL Certificate installed.
- The customer will share SSL certificate files like key, private, Security, and certificate files with us. Here, we need only the .key and crt file to install SSL in the Motadata server.
- When a key file is generated, it is required to generate a password, which we need during the installation of SSL in the Motadata Server.
- Password size must require six or more letters, and we recommend using the same password at every instance where a password/passphrase is asked.
Installation Steps
- If the user already has .key and .crt files, please rename them to jcg.key and jcg.crt (private key and Certificate files) and upload them in /opt/SSL directory, and follow the steps from No. 9.
- If the user does not have a .key and .crt file and wants to generate a self-signed certificate, please follow the steps from No. 1.
Take SSH and connect to the Motadata server.
Create a directory in /opt
sudo mkdir /opt/SSLGo to the SSL directory.
cd /opt/SSLRun the below command to generate the key. Here, we have taken the name of the key file as jcg.key. You can keep the desired name of the file:
sudo openssl genrsa -des3 -out jcg.keyMotadata will prompt for a password. Enter the password (minimum 4 characters). Type again to confirm the password.
Enter pass phrase for jcg.key:
Verifying - Enter pass phrase for jcg.key:Run the below command to create a certificate file. Here, we have taken the name of the certificate file as jcg.crt. You can choose the desired name of the file. Motadata will ask you for a password. Enter a password (minimum 4 characters). Type again to confirm the password.
sudo openssl req -new -x509 -key jcg.key -out jcg.crtEnter the password you defined for the key file.
Enter pass phrase for jcg.key:The system will ask for some details to fill in your certificate. These details are called distinguished names. You can leave some fields blank. If you enter ‘.’, the field will be left blank.
You are about to be asked to enter information that will be incorporated into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank
For some fields there will be a default value, If you enter '.', the field will be left blank.
Country Name (2 letter code) [AU]:IN
State or Province Name (full name) [Some-State]:Gujrat Locality Name (eg, city) []:Ahmedabad
Organization Name (eg, company) [Internet Widgits Pty Ltd]:Mindarray Systems Organizational Unit Name (eg, section) []:Motadata
Common Name (e.g. server FQDN or YOUR name) []:Shubham
Email AddressRun the below command to convert the CRT file to PKCS12 format.
sudo openssl pkcs12 -inkey jcg.key -in jcg.crt -export -out jcg.pkcs12
jcg.pkcs12 Enter the password you defined for the key file:
Enter pass phrase for jcg.key:
Enter a password to export the file. You can use any password (more than 4 characters). Enter once more to verify the password.
Enter Export Password:
Veriying - Enter Export Password:Import the PKCS12 file in the keystore of Jetty. Run the below command to copy JCG.PKCS12 file to the /motadata/motadata/jetty- hightide/etc directory:
sudo cp jcg.pkcs12 /motadata/motadata/jetty-hightide/etc/Change permission of JCG.PKCS12 file:
sudo chmod 755 /motadata/motadata/jetty-hightide/etc/jcg.pkcs12Move the existing keystore file using the below command:
sudo mv /motadata/motadata/jetty-hightide/etc/keystore /tmpExecute the keytool import command. Kindly check if the command is pasted properly (The link below is in small font to manage it in a single line).
sudo /motadata/motadata/jdk/bin/keytool -importkeystore -srckeystore jcg.pkcs12 -srcstoretype PKCS12 -destkeystore keystoreEnter a password for the destination and source keystore:
Enter destination keystore password: Re-enter new password:
Enter source keystore password:Copy the keystore to the path:
/motadata/motadata/jetty-hightide/etc/
sudo cp keystore /motadata/motadata/jetty-hightide/etcChange the permission of the keystore file using the below command.
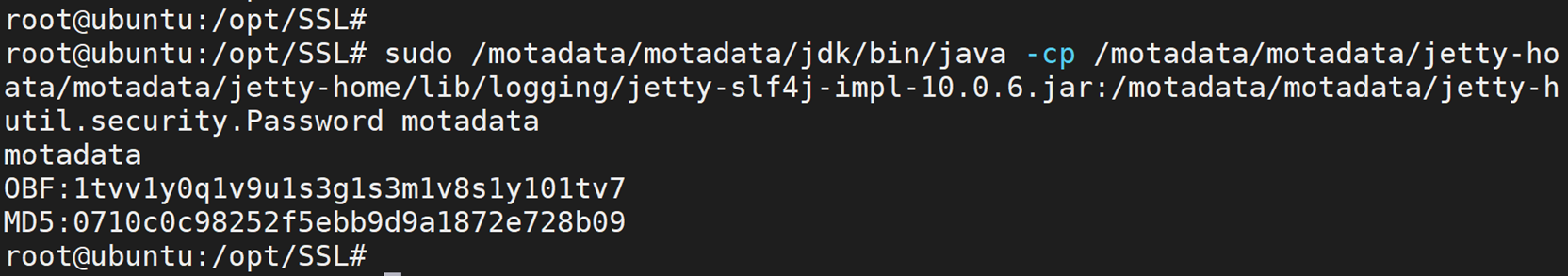
sudo chmod 755 /motadata/motadata/jetty-hightide/etc/keystoreGenerate an encrypted password for the jcg.key file (The below link is in small font to manage it in a single line). You need to enter your jcg key password at last without using < > operators.
sudo /motadata/motadata/jdk/bin/java -cp /motadata/motadata/jetty-home/lib/logging/slf4j-api-2.0.0-alpha1.jar:/motadata/motadata/jetty-home/lib/logging/jetty-slf4j-impl-10.0.6.jar:/motadata/motadata/jetty-home/lib/jetty-util-10.0.6.jar org.eclipse.jetty.util.security.Password motadataCopy the OBF password and note it somewhere:
Edit the jetty-ssl-context.xml file using the following command:
vi /motadata/motadata/jetty-home/etc/jetty-ssl-context.xml
Replace the OBF values for the keystore and save the file. Use the standard Linux command: i to make changes in the file and !wq! to save the changes in the file.

Make changes on the path below:
/motadata/motadata/jetty-hightide/start.d/ssl.ini--module=ssl
jetty.ssl.host=0.0.0.0 >> uncomment this line
jetty.ssl.port=8443 >> uncomment this line
jetty.sslContext.keyStorePassword=OBF:1ku11l181ltu1ri71vu71ri71vv31ri71lq41kxu1kqt >>> change the OBF which we create while SSL configuration
jetty.sslContext.keyManagerPassword=OBF:1ku11l181ltu1ri71vu71ri71vv31ri71lq41kxu1kqt >>> change the OBF which we create while SSL configurationIf a client wants to restrict access to the HTTP protocol, follow the steps below.
/motadata/motadata/jetty-hightide/start.d/http.ini#--module=http >> comment this line
jetty.http.host=0.0.0.0 >> uncomment this line
jetty.http.port=8443 >> uncomment this lineNow, restart the service of Motadata using: service Motadata stop then sudo service Motadata start:
sudo service motadata stop
sudo service motadata start
You can check if port 8443 is in the listening mode or not for the Motadata server using the below command:
sudo netstat -apn | grep 8443
If yes, you can access the Motadata NMS GUI using HTTPS and port 8443. Example: https://172.16.8.73:8443/