Configuring WinRM to monitor Windows Environment
- Enable PowerShell on Windows Stand Alone Machine
Note: Following are commands we need to execute on the machine from which we need to pull the data, using Remote PowerShell (All windows machine that we want to monitor using Motadata). Commands Recommended to Execute in order as mentioned below.
Run Below Commands In CMD as Administrator:
winrm quickconfig and Press Y when prompted.
winrm set winrm/config/service/Auth @{Basic=“true”}
winrm set winrm/config/service @{AllowUnencrypted=“true”}
winrm set winrm/config/winrs @{MaxMemoryPerShellMB=“1024”}
winrm set winrm/config/client/Auth @{Basic=“true”}
winrm set winrm/config/client @{AllowUnencrypted=“true”}
winrm set winrm/config/winrs @{MaxProcessesPerShell=“2147483647”}
winrm set winrm/config/winrs @{MaxConcurrentUsers=“100”}
winrm set winrm/config/service @{MaxConnections=“50”}
winrm set winrm/config/winrs @{MaxShellsPerUser=“2147483647”}
winrm set winrm/config/service @{MaxConcurrentOperationsPerUser=“4294967295”}
net stop winrm
net start winrm
Run Below Commands In Windows PowerShell
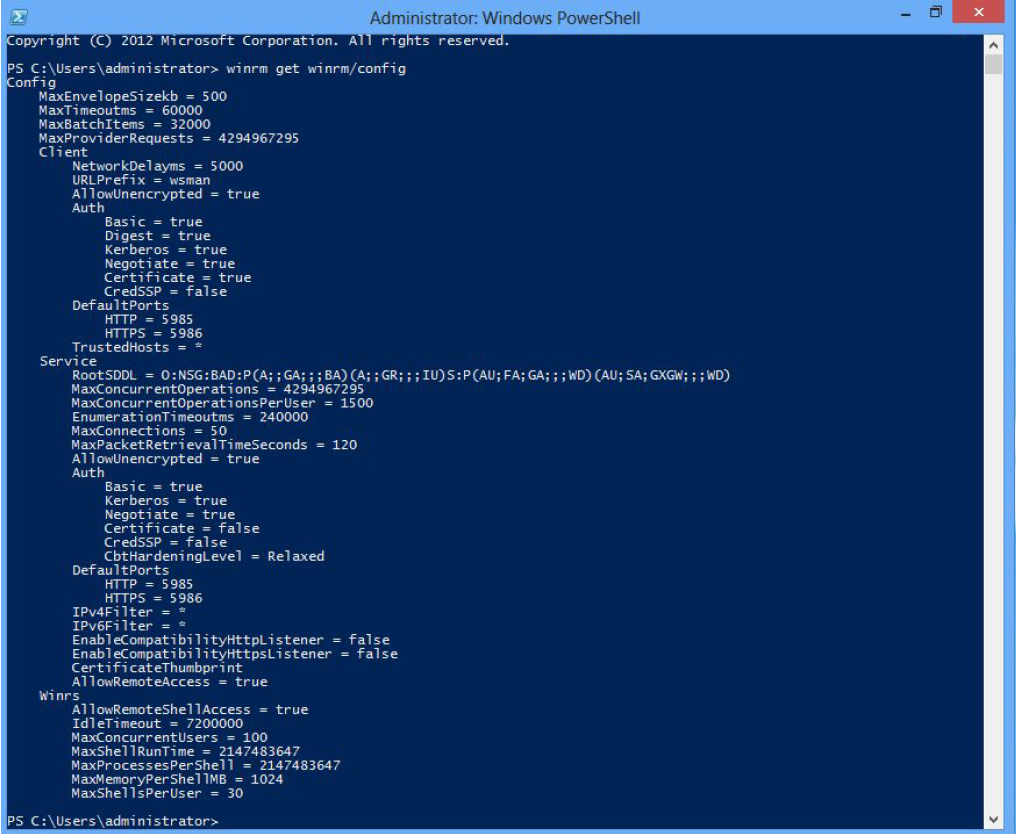
winrm get winrm/config (You can verify all configuration by this command which will look as mention below)
net stop winrm
net start winrm
- Configuring Windows Server 2012/2008 Using Group Policy
This configuration creates a local user account on each monitored Windows system for authentication instead of a domain account. The specified user account must be present on each system to allow Motadata to pull information from the target system.
Log on to a domain controller as a user with ‘Domain Admin’ privileges.
- On Server 2012 (non R2):
Press the Windows key on the keyboard to display the Start screen. Click the Group Policy Management tile.
The Group Policy Management Console (GPMC) is normally installed by default on the domain controller. You can install GPMC on a member server as long as it is a member of the domain. If the tile is not present and you need to install it, use the instructions provided at: http://technet.microsoft.com/enus/library/cc725932.aspx
On Server 2012 R2:
- Press the Windows key on the keyboard to display the Start screen
- Click Server Manager.
- Click Tools in the upper right
- Select Group Policy Management.
The Group Policy Management Console (GPMC) is normally installed by default on the domain controller. You can install GPMC on a member server as long as it is a member of the domain. If the tile is not present and you need to install it, use the instructions provided at: http://technet.microsoft.com/enus/library/dn265969.aspx
- Navigate to your target domain in the tree at the left:
- Expand the section for the domain Forest you want to edit.
- Expand Domains.
- Expand your target domain.
- Rightclick Group Policy Objects and select New. In the form that displays:
- Enter a name for your new Group Policy Object, for example, WinRM_RemoteMonitoring.
- Leave “(none)” in the Source Starter GPO field.
- Click OK to save and exit the form.
- Select your new Group Domain Policy Object, WinRM_RemoteMonitoring, for example.
- Right click your new Group Domain Policy Object and select Edit to open the Group Policy Management Editor.
Expand the Computer Configuration section of the tree and navigate the tree to:
Policies\Administrative Templates:Policy...\Windows Components\Windows Remote Management(WinRM)
- Enable remote server management:
- Click on WinRM Service to access the WinRM Service Group Policy settings in the right pane.
- Double-click the Allow remote server management through WinRM property.
- Click the Enabled radio button.
- Place an asterisk as a wildcard (’ * ‘) in the IPv4 filer and IPv6 fields or specify a range of IP addresses for WinRM to listen on.
- Click OK at the bottom to submit the form.
- Enable authentication:
- Double-click the Allow Basic authentication property in the right pane.
- Select the Enabled radio button.
- Click OK at the bottom to submit the form.
- Specify unencrypted traffic:
- Double click the Allow unencrypted traffic property.
- Select the Enabled radio button.
- Click OK at the bottom to submit the form.
- Select Windows Remote Shell in the left pane to set its Group Policy settings.
This is located in the group policy tree in the following location (which might be located right below WinRM service in the tree):
Computer Configuration\Policies\Administrative Templates\WindowsComponents\Windows Remote Shell
- In the right pane, configure following:
- Double-click Allow Remote Shell Access. Select the Enabled radio button.
- Double-click Specify maximum number of processes per Shell. Select the Enabled radio button. Set MaxShellsPerUser field to value 2147483647
- Double-click MaxProcessesPerShell. Select the enabled radio button. Set MaxProcessesPerShell field to value 2147483647
- Double-click MaxConcurrentUsers. Select the enabled radio button. Set MaxConcurrentUsers field to value 100
- Double-click MaxConnections. Select the enabled radio button. Set MaxConnections field to value 50
- Double-click MaxConcurrentOperationsPerUser. Select the enabled radio button. Set MaxConcurrentOperationsPerUser field to value 4294967295
- Click OK at the bottom to submit the form.
- Windows Server 2012: Configuring Firewall Group Policies
The appropriate port must be opened on the firewalls of monitored servers. You can use Group Policy to open the required ports on all servers across the organization. By default WinRM service listens on port 5985 when data payload encryption is not used and on port 5986 when encryption is used. Additionally, ICMP (ping) requests must be enabled for availability monitoring.
In the Group Policy Manager Editor, navigate to:
Computer ConfigurationPoliciesWindows SettingsSecurity SettingsWindows Firewall with Advanced SecurityWindows Firewall with Advanced Security LDAP;…Inbound Rules
- Create a new Inbound Rules policy for Windows Remote Management:
- Right click Inbound Rules in the left pane.
- Select New Rule…
- Select the Predefined radio button.
- Select Windows Remote Management from the drop down list.
- Click Next.
- Ensure that all items in the list are checked.
- Click Next.
- Ensure that the Allow the connection radio button is selected.
- Click Finish.
- Create a new Inbound Rules policy for Echo Request ICMP (ping) requests:
- Right click Inbound Rules in the left pane.
- Select New Rule…
- Select the Predefined radio button.
- Select File and Printer Sharing from the drop down list.
- Click Next.
- Ensure the check boxes for the following items are selected:
- File and Printer Sharing (Echo RequestICPMv4IN)
- File and Printer Sharing (Echo RequestICPMv6IN)
- Click Next
- Ensure that the Allow the connection radio button is selected.
- Click Finish.
Link your new GPO to one or more Organizational Units (OU) containing servers to which you wish to have the policies applied. Alternatively, you can apply the policies to all Windows servers in the domain by linking the new GPO to the domain itself. To link the GPO to the domain, complete the following process.
Substitute a specific OU for the domain if you want to link only to a subset of servers.
- Right click your domain in the left pane of the Group Policy Management window.
- Choose Link an Existing GPO
- Configuring the Motadata Server to Access the Windows DNS Server
The Motadata server and collectors must be able to resolve the target server’s pointer records (PTR) to their Active Directory fully qualified domain name. Administrators can meet this requirement by using one of two methods:
Configuring the Motadata server to access the Windows DNS server for its DNS resolutions. OR Manually entering PTR records for each server in to the /etc/hosts file. For example, the server prod1.example.com at the IP address 172.10.16.20 has the following PTR record: 172.10.16.20 prod1.example.com
- Configuring the Kerberos Enabled Windows Domain in Motadata Server
Motadata must authenticate to the Windows systems it will monitor using Windows domain credentials. Specify the windows domain information where dedicated User account created for remote monitoring.
- Navigate to Motadata web console > Admin > Kerberos domain > New.
- Provide IP address and FQDN of the target windows domain.