Vulnerability Solutions
A VAPT solution document outlines the process of identifying and addressing security vulnerabilities in an organization's IT infrastructure. It covers both vulnerability assessments, which detect weaknesses, and penetration testing, which simulates cyberattacks to exploit them. This document helps organizations improve security by proactively identifying risks and ensuring compliance with security standards. Read on to learn how the various vulnerabilities are resolved.
- The VAPT solution document applies to the Ubuntu OS v22.04.
- Please use ROOT user to execute the commands.
VAPT List
IDX-002 - Privilege Escalation
Description:
Attackers exploit weaknesses in a system or application to bypass user restrictions, leading to:
- Horizontal Privilege Escalation – Gaining access to another user's data or actions.
- Vertical Privilege Escalation – Obtaining higher-level permissions, such as administrator rights.
Solution:
Created a new REST API and mapped it with flotouser REST API to update requests based on field visibility from the UI.
IDX-007 - EXIF Geolocation Data Not Stripped from Uploaded Images
Description:
When a user uploads an image, sensitive metadata is not removed, allowing attackers to access:
- Geolocation Data – Revealing the user's exact location.
- Device Information – Including device name, version, software, and software version used.
Solution:
Images were not sanitized before uploading, leading to exposure of metadata.
IDX-009 - Username Enumeration
Description:
The application displays different error messages for incorrect usernames and passwords, allowing attackers to:
- Identify valid usernames.
- Use this information for further attacks (e.g., brute force attempts).
Solution:
Implemented a common error response message for incorrect username/email in the forgot password and login flows, along with improved logging mechanisms.
IDX-008 - Frontend Restriction Bypassed
Description:
Attackers manipulate client-side security controls, such as:
- Disabling JavaScript validation to bypass input checks.
- Altering input limits to exceed intended values.
- Modifying hidden fields using browser developer tools or scripts.
Solution:
No backend validation was implemented, making frontend restrictions ineffective.
JDK Vulnerability: Need to Upgrade JDK Version to 17.0.14
Description:
The existing JDK version contains multiple security vulnerabilities, requiring an upgrade to JDK 17.0.14.
Solution:
Upgraded JDK from 17.0.12 to 17.0.14 to address security issues.
Exploitable HTTP Methods ("PUT")
Description:
Allowing unused HTTP methods increases security risks:
- Attack Surface Expansion: If methods like PUT, DELETE, or PATCH are enabled, attackers can modify, delete, or overwrite data.
- Exploitation Risk: Even if the application does not actively use these methods, they can still be targeted for attacks.
Solution:
Removed the PUT method from API calls to prevent unauthorized modifications.
PostgreSQL Vulnerability: Version Upgrade to 16.8
Description:
Zero-day vulnerability in PostgreSQL exposes the system to potential threats.
Solution:
Upgraded PostgreSQL from versions 11 and 16.1 to 16.8 to patch security vulnerabilities.
Elastic Search Vulnerability: Version Upgrade to 8.17
Description:
Zero-day vulnerability in Elastic Search poses security risks.
Solution:
Update Elastic Search from v7.3.2 to v8.17.2 to ensure security compliance.
Lib Curl
To resolve the vulnerability, upgrade lib curl to version 8.4 or later. To upgrade, follow the below steps:
Download and extract the "curl_VAPT" zip file.
Login to the terminal server.
Navigate to the extracted folder and install the deb packages using the below command:
dpkg -i *.deb
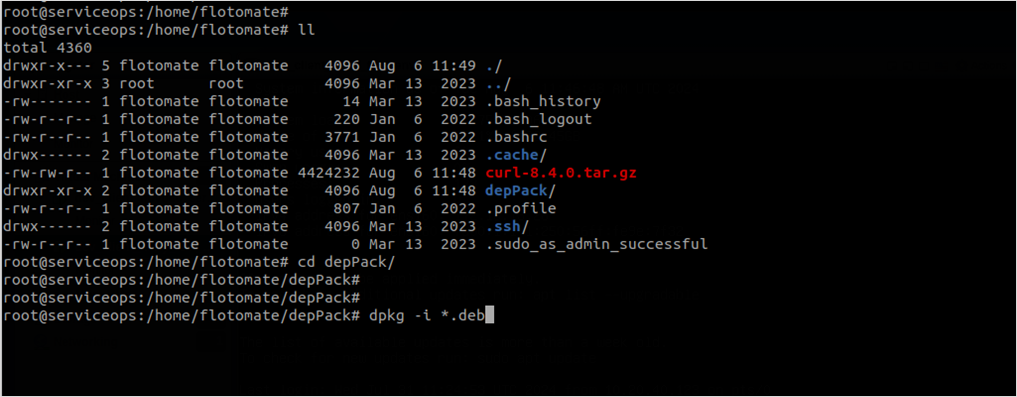
- Once the dependency packages are installed, update the curl package.
- Install the curl setup by extracting the tar file.
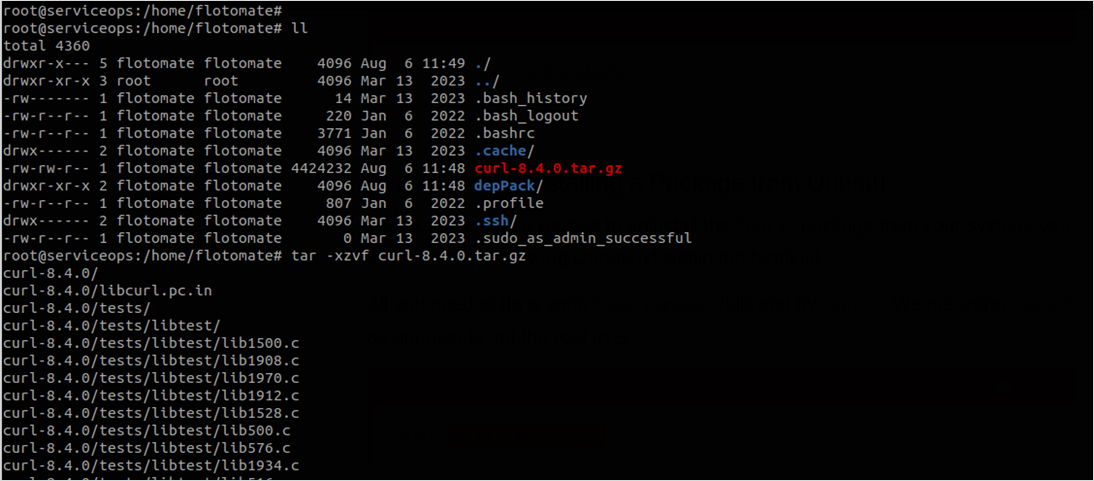
- Navigate to the curl folder as shown below:
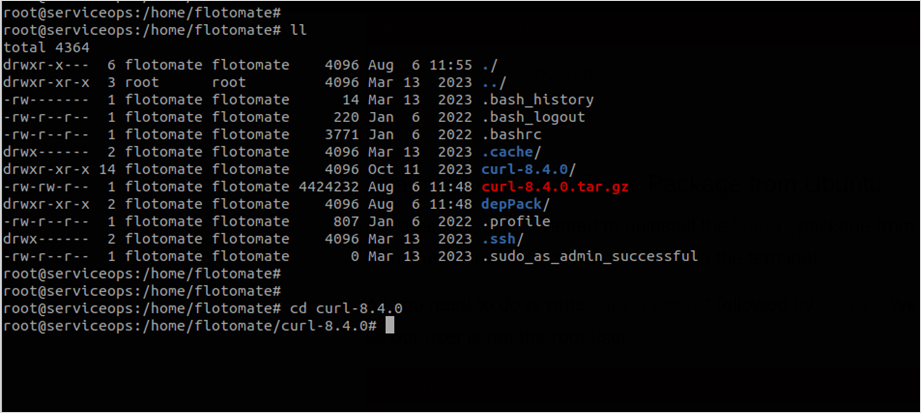
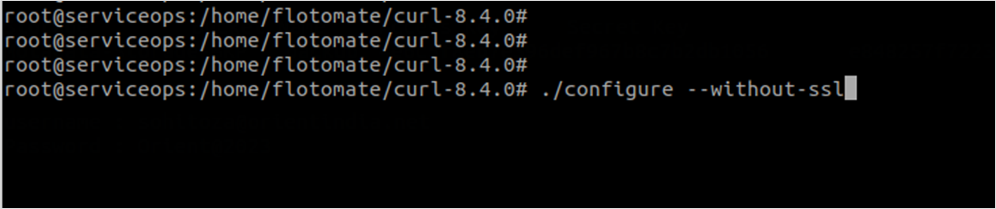
Run the below commands:
./configure --without-ssl
make
make install
ldconfig
Once done, check the curl version using the below command:
curl --version
SSH Terrapin Prefix Truncation Weakness Vulnerability
To resolve the vulnerability, follow the below steps:
Add the below line to the /etc/ssh/sshd_config file.
Ciphers -chacha20-poly1305@openssh.com
Save the file by pressing the Esc key, typing ":wq!", and pressing Enter.
Check the status of sshd using the command:
systemctl status sshdRestart sshd using the command:
systemctl restart sshdCheck the status of sshd using the command:
systemctl status sshd
OpenSSL 1.0.1 < 1.0.1u Multiple Vulnerabilities (Ubuntu 22.04)
To resolve the vulnerability, follow the below steps:
Download the openssl zip file.
Execute and install the dpkg packages using the below commands:
cd openssl/
dpkg -i openssl_3.0.2-0ubuntu1.18_amd64.deb
APACHE Log4j, Upgrade Apache Log4j version 2.17.1, 2.12.4, or 2.3.2 or later, or apply the vendor mitigation (Elasticsearch) / Apache Log4j 2.0 < 2.3.2 / 2.4 < 2.12.4 / 2.13 < 2.17.1 RCE
To resolve the vulnerability, follow the below steps:
Before performing the steps below, ensure the file path is from the VAPT sheet or docs.
Download the ElasticSearchlog4jVAPT zip file.
Replace the two files and assign ownership to them.
Check the elastic search service status and stop it using the below commands:
systemctl status elasticsearch
systemctl stop elasticsearch
cd /usr/share/elasticsearch-7.3.2/libRemove the older log4j library files using the below commands:
rm log4j-core-2.11.1.jar
rm log4j-api-2.11.1.jarReplace the new updated log4j library file to /usr/share/elasticsearch-7.3.2/lib/ using the below commands:
cp log4j-core-2.17.2.jar /usr/share/elasticsearch-7.3.2/lib/
cp log4j-api-2.17.2.jar /usr/share/elasticsearch-7.3.2/lib/Assign fmtuser and fmtusergroup permission using the below commands:
cd /usr/share/
chown -R fmtuser:fmtusergroup elasticsearch-7.3.2/Check the elastic search service status and start it using the below commands:
systemctl status elasticsearch
systemctl start elasticsearch
systemctl status elasticsearch
OpenSSH Upgrade v8.9 to 9.6
To resolve the vulnerability, follow the below steps:
- Take the VM snapshot before you implement the below VAPT solution.
- Please copy the database and fileDB backup to another location.
- The attached ZIP file includes two fully functional methods for the OpenSSH solution.
Download and extract the OpenSSH_VAPT zip file.
Execute the file using the below command:
cd OpenSSH_VAPT/OpensshPack/DepPack
dpkg -i *.debOnce the above packages are installed, begin the OpenSSH upgrade process.
Extract the tar file using the below command:
tar -xzvf openssh-9.6p1.tar.gzNavigate to the extracted folder using the below command:
cd openssh-9.6p1Verify the SSH version using the below command:
ssh –VInstall using the below command.
./configure
make
sudo make install
source /etc/environmentVerify the SSH version using the below command:
ssh -V
- This document can be updated for future improvements or to add new VAPT point solutions.
- The download links can be updated if needed in the future or if another method becomes available.